https://www.oracle.com/java/technologies/javase/javase8-archive-downloads.html 先下载8u20
回顾学习
回顾7u21反序列化利用链
| |
| |
修复方式是,在sun.reflect.annotation.AnnotationInvocationHandler#readObject里面,之前捕获异常但是直接返回了,不影响反序列化,现在是直接抛出异常,就阻碍反序列化了。
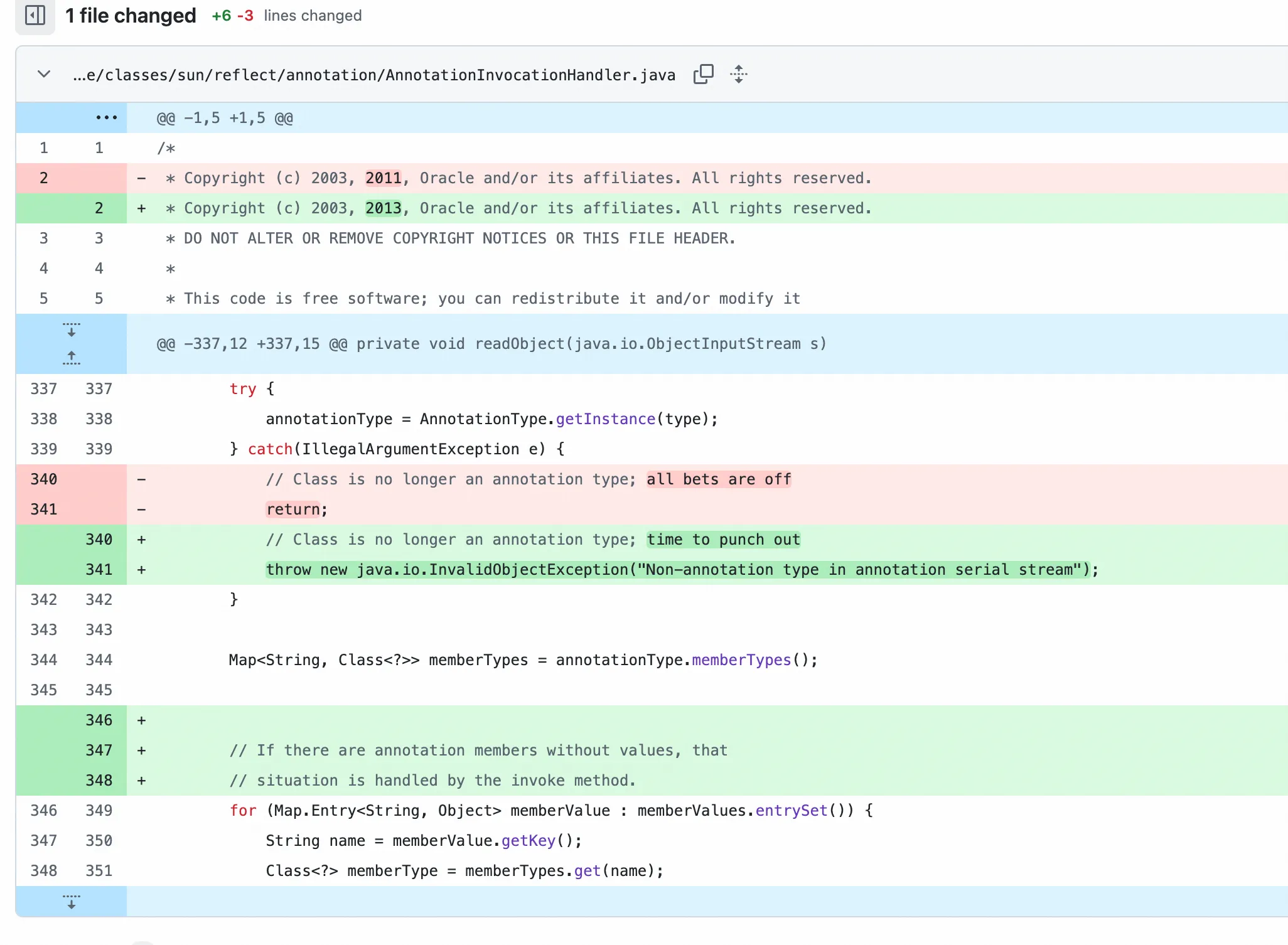
但是我们观察到AnnotationInvocationHandler 的 readObject() 当中,除了第一行调用了 ObjectInputStream 的 defaultReadObject() 外,其他位置都没有再从 stream 中读内容,也就是说,在 throw Exception 之前,一个 AnnotationInvocationHandler 对象已经被完整构造好了。来看一个有趣的逻辑问题
| |
最终回显为good,典型的双重否定变肯定!那现在需要找到一个合适的 readObject,前面的反序列化入口是Hashset#readObject,并且其中还会触发s.readObject()
| |
这个 for 循环学习CC链的时候经常见,有两次,第一次是通过 readObject() 构造一个 TemplatesImpl ,第二次是通过 readObject() 构造一个 proxy ,然后 put 这个 proxy ,而也就是这第二次的 put 触发了RCE。而 Proxy 对象只有一个属性 InvocationHandler 那必然是复用这个地方
Java序列化协议允许通过TC_REFERENCE(0x71)引用已反序列化的对象。这种设计原本是为了优化重复对象的存储,但是现在,hiahia,所以现在再找一个和jdk7u21时的AnnotationInvocationHandler一样的类就行了,找到java.beans.beancontext.BeanContextSupport
| |
跟进到 readChildren
| |
可以看到 readChildren 方法里面的catch模块全是 continue,并且也进行了ois.readObject()来反序列化,结合序列化中 Reference 的特性,只要让上面的 for 循环运行3次(也就是 s.readObject() 运行三次),第一次构建AnnotationInvocationHandler,第二次和原来一样,构造一个 TemplatesImpl , 第三次用 TC_REFERENCE 让 proxy 的 h 指向第一次构建的AnnotationInvocationHandler,而为了这样精准的控制,我们需要使用 LinkedHashSet 而不是 Hashset,LinkedHashSet 的序列化/反序列化行为会严格保持插入顺序,而 HashSet 的顺序是不确定的。
Poc
poc1 报错
首先设置 serializable 为1触发 readChildren,然后引用 handler,在 children 字段注入 Hashmap,LinkedHashSet 不要把顺序弄错了,最后注入 memberValues形成比较触发RCE
| |
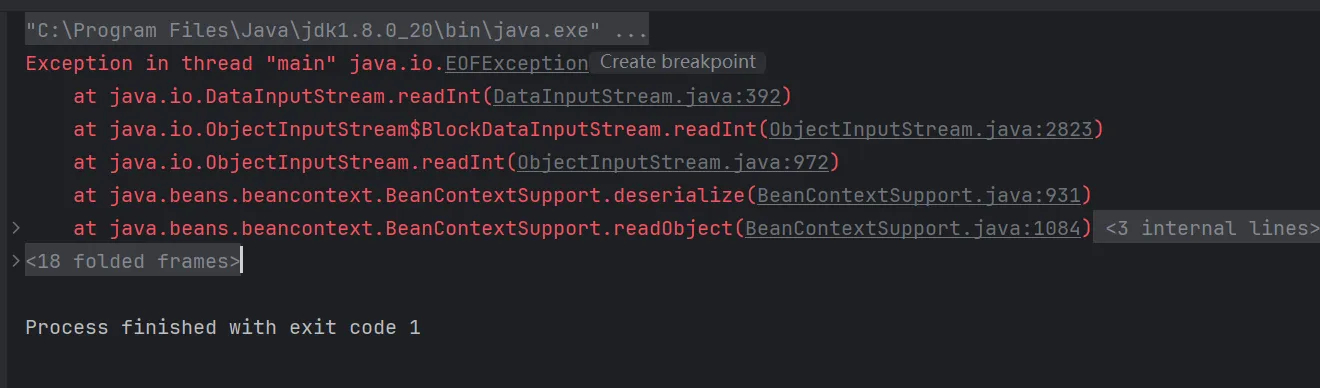
看到报错里面BeanContextSupport#deserialize跟进之后发现到这里就会抛出错误
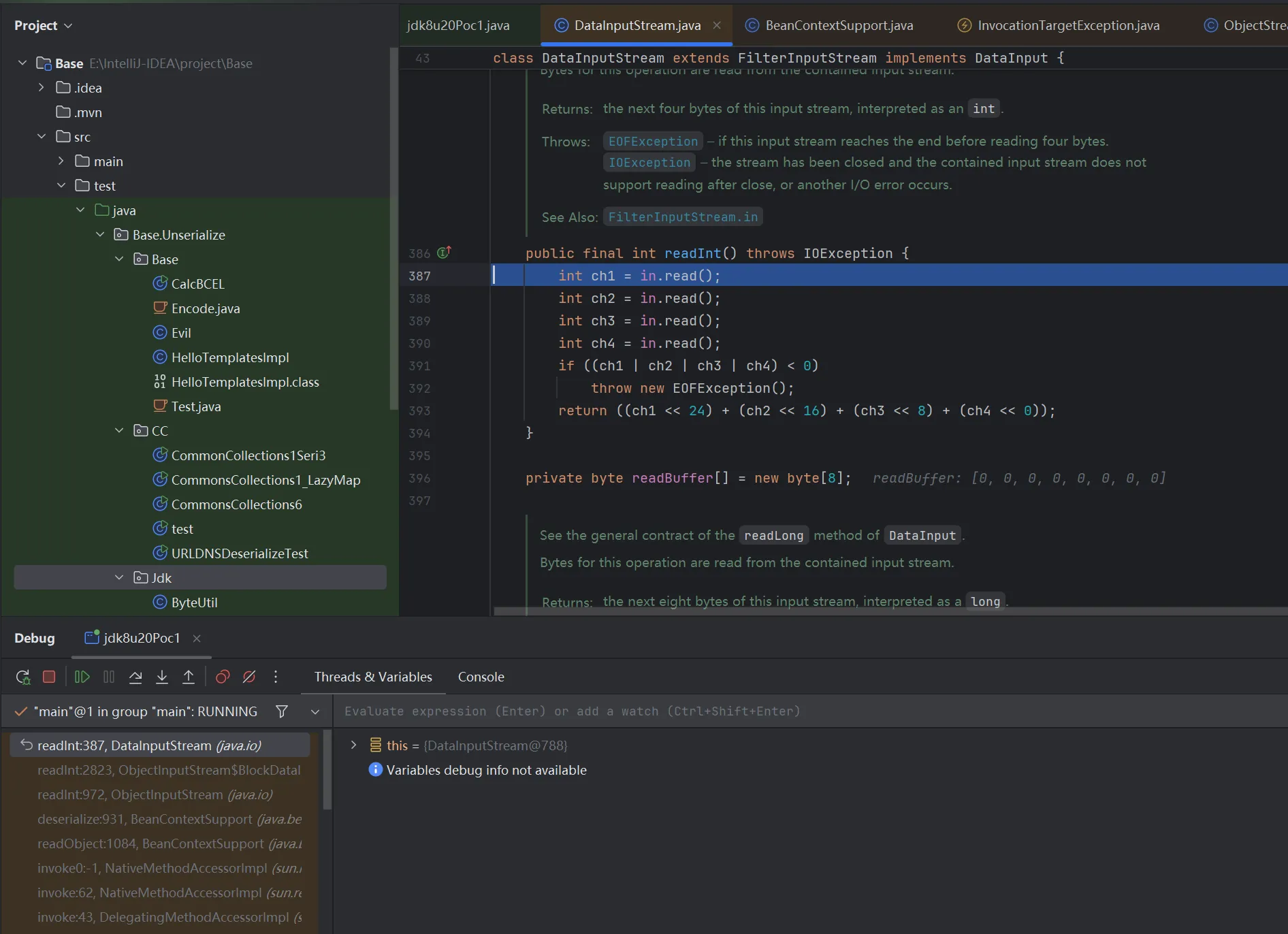
继续跟进到发现根本问题在这里
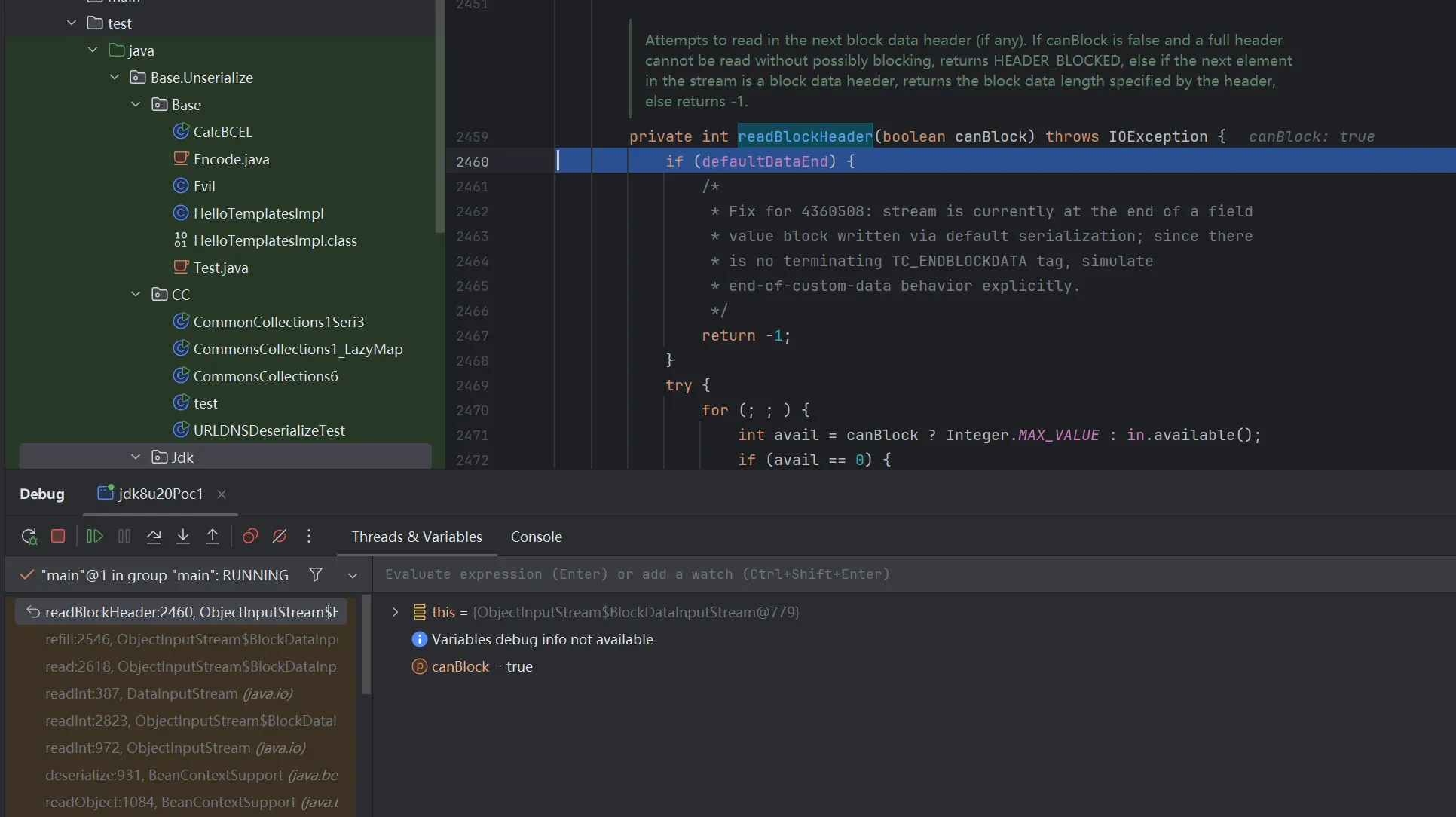
全局搜索 defaultDataEnd 找到这里给赋值的true
| |
可以看出需要自定义一个 WriteObject 方法,用 javassist 给AnnotationInvocationHandler加一个 writeObjecct()方法
poc2 报错
| |
依旧报错,调试发现在这里到下面的 switch 语句会直接跳出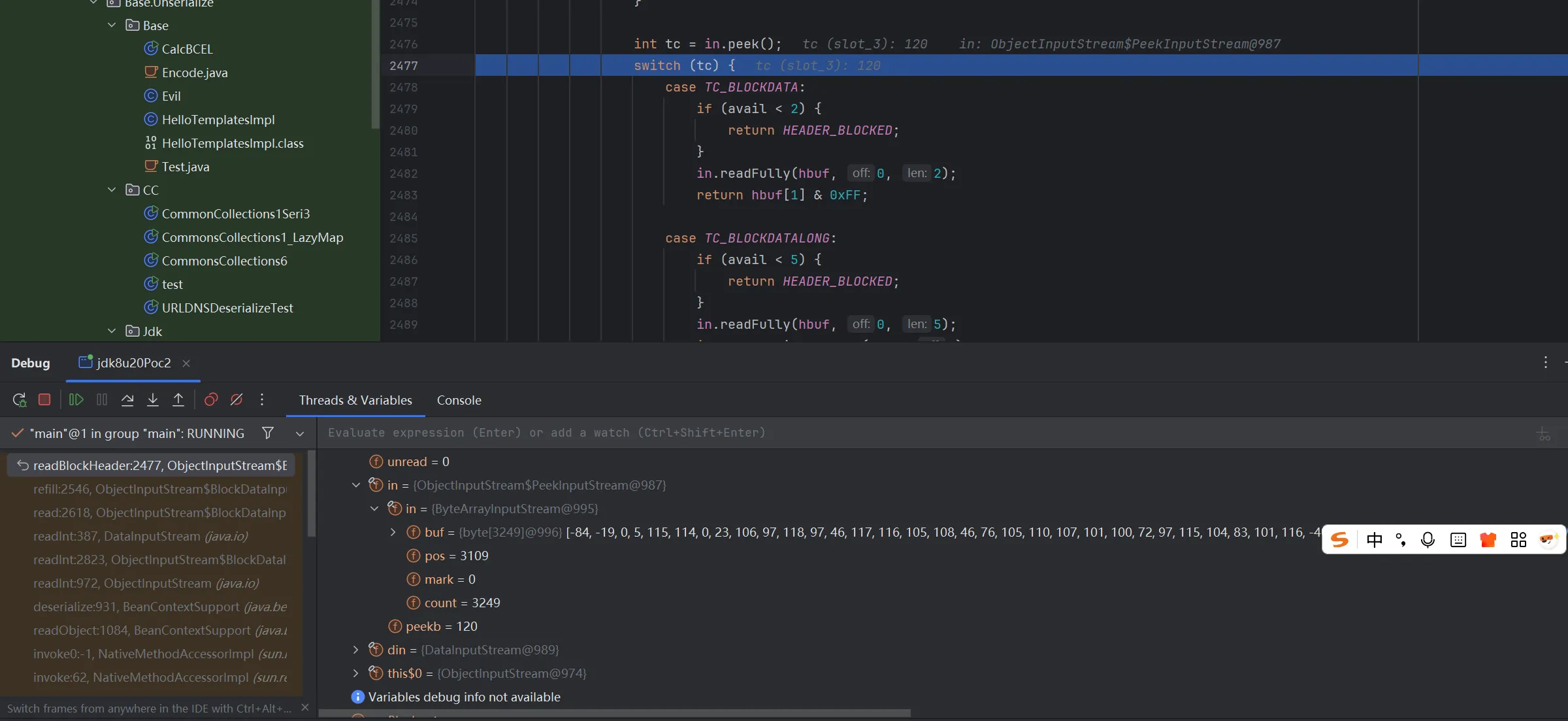
将序列化函数和反序列化函数进行修改,写入到文件中,
| |
分析下序列化流,找到3109的位置
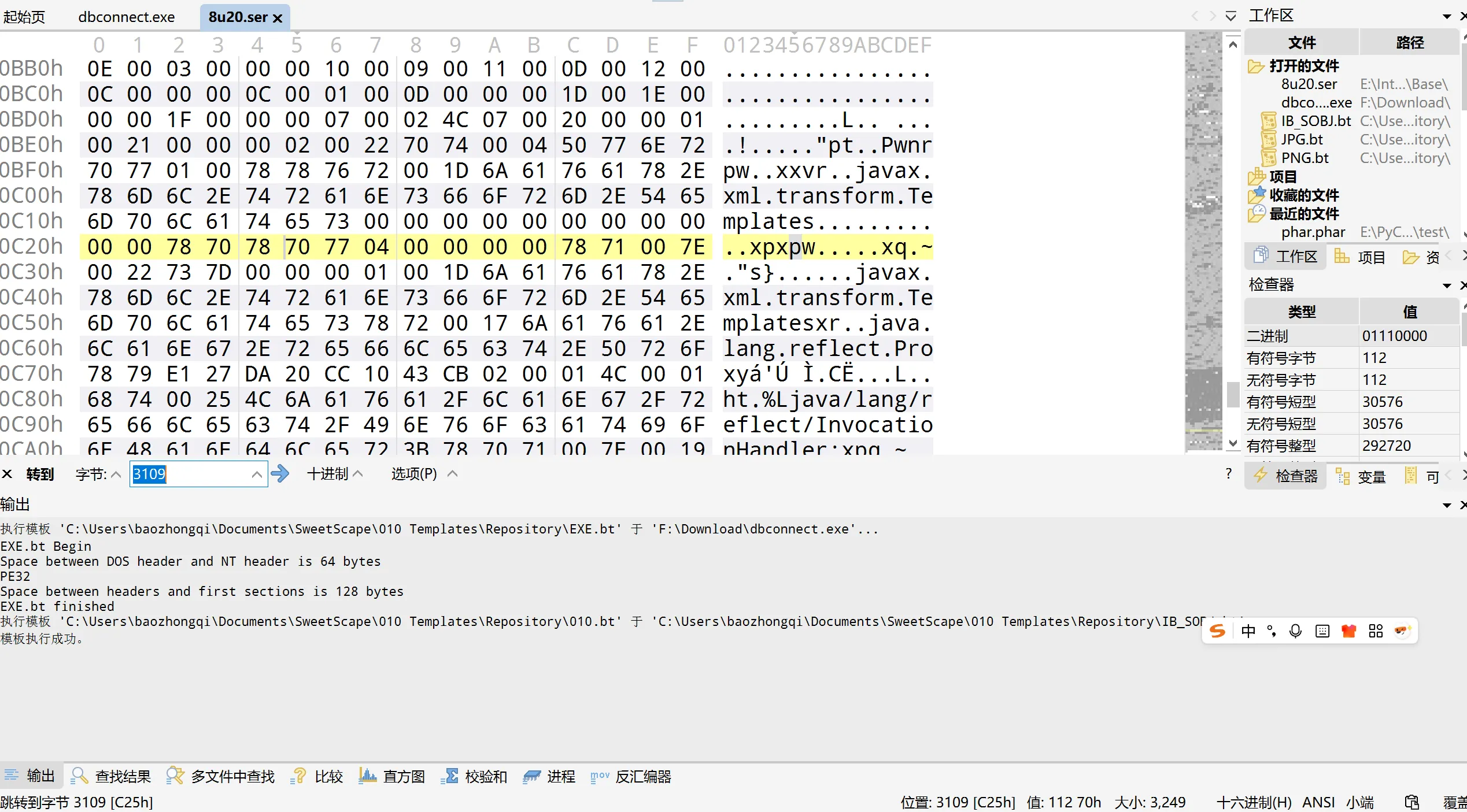
https://docs.oracle.com/javase/8/docs/platform/serialization/spec/protocol.html 查看文档发现是
| |
把这两玩意删了,
| |
最终poc
我们要把删除字节的功能实现在代码中,由于Byteutils有时候我获取不到,有时候又可以,保险起见,我直接从源码里面抄出来。
| |
这里有一个坑点就是我们不能直接在poc中反序列化,如果这样的话是必然会失败的,我看到
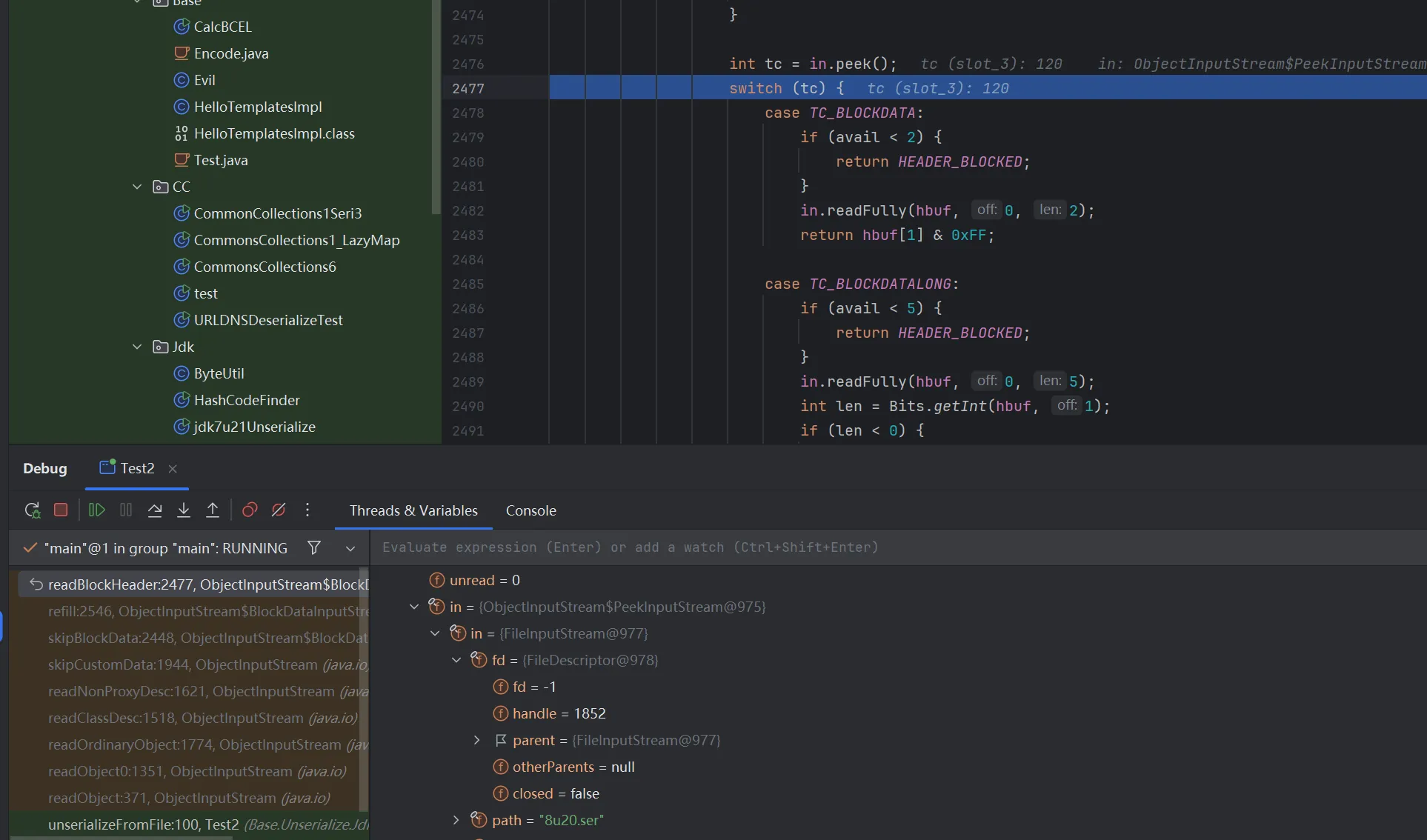
这一看就不对了,但是原因是什么,我暂时理解为是我在运行时强行修改导致的。
还有个面向对象反序列化的工具 https://github.com/QAX-A-Team/SerialWriter,如果是使用的修改序列化流的话,这个工具非常实用。
https://xz.aliyun.com/news/9065
https://xz.aliyun.com/news/1399
https://www.inhann.top/2022/09/11/8u20/
https://github.com/pwntester/JRE8u20_RCE_Gadget/blob/master/src/main/java/ExploitGenerator.java