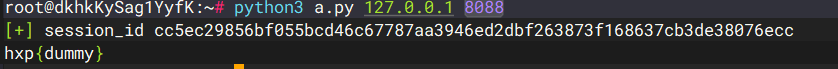
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
| package main
import (
"fmt"
"io"
"net"
"net/http"
"os"
"strings"
"time"
)
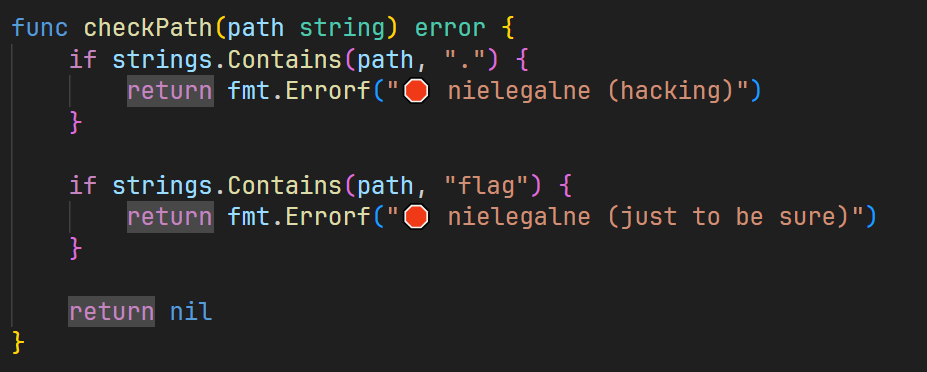
func checkPath(path string) error {
if strings.Contains(path, ".") {
return fmt.Errorf("🛑 nielegalne (hacking)")
}
if strings.Contains(path, "flag") {
return fmt.Errorf("🛑 nielegalne (just to be sure)")
}
return nil
}
func main() {
time.AfterFunc(180*time.Second, func() {
os.Exit(0)
})
session, ok := os.LookupEnv("SESSION")
if !ok {
panic("SESSION env not set")
}
dataDir := "/tmp/kv." + session
err := os.Mkdir(dataDir, 0o777)
if err != nil {
panic(err)
}
err = os.Chdir(dataDir)
if err != nil {
panic(err)
}
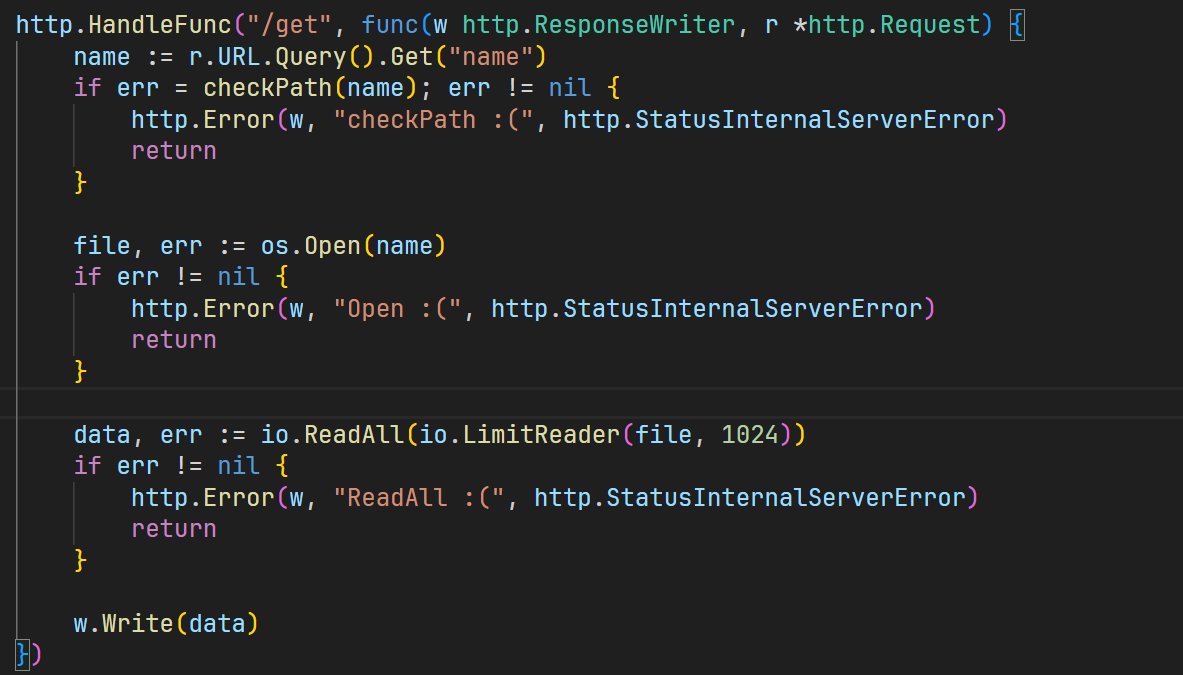
http.HandleFunc("/get", func(w http.ResponseWriter, r *http.Request) {
name := r.URL.Query().Get("name")
if err = checkPath(name); err != nil {
http.Error(w, "checkPath :(", http.StatusInternalServerError)
return
}
file, err := os.Open(name)
if err != nil {
http.Error(w, "Open :(", http.StatusInternalServerError)
return
}
data, err := io.ReadAll(io.LimitReader(file, 1024))
if err != nil {
http.Error(w, "ReadAll :(", http.StatusInternalServerError)
return
}
w.Write(data)
})
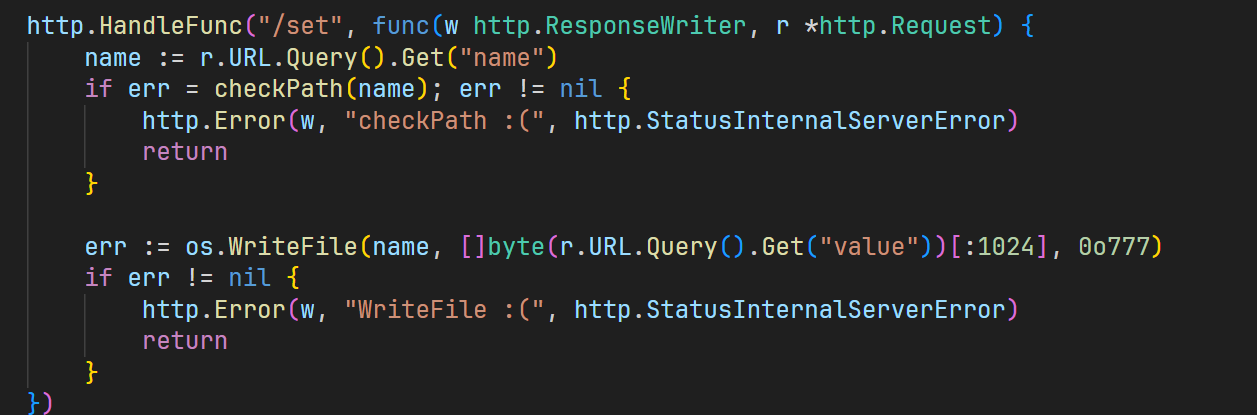
http.HandleFunc("/set", func(w http.ResponseWriter, r *http.Request) {
name := r.URL.Query().Get("name")
if err = checkPath(name); err != nil {
http.Error(w, "checkPath :(", http.StatusInternalServerError)
return
}
err := os.WriteFile(name, []byte(r.URL.Query().Get("value"))[:1024], 0o777)
if err != nil {
http.Error(w, "WriteFile :(", http.StatusInternalServerError)
return
}
})
unixListener, err := net.Listen("unix", dataDir+"/kv.socket")
if err != nil {
panic(err)
}
http.Serve(unixListener, nil)
}
|