起环境的时候发现了这样的报错
1 | [+] Running 1/0 |
也就是说IP池满了,清理一下就好了
1 | # 删除所有未使用的网络 |
haschbargeld
附件里面没有代码,而是一些简单的设置,先去docker里面拿源码
1 | # 1. 进入容器 shell |
在post_comment.php里面
1 |
|
跟进函数,关键代码如下
1 | function hc_CheckStamp() |
我们必须通过所有验证,才能保证$validstamp为TRUE,才能得到flag,由于是global关键字,所以直接看hc_config.php,看到参数
1 |
|
1 | hc_contract=31&hc_stamp=8位的字符串&hc_collision=9位字符串 |
这是前三个if,到了第四个if进行跟进hc_CheckExpiration,
1 | function hc_CheckExpiration($a_stamp) |
时间戳哪里我其实挺迷惑的后面测试发现等效
1 |
|
继续跟进hc_HashFunc
1 | function hc_HashFunc($x) { return sprintf("%08x", crc32($x)); } |
写出相应处理
1 |
|
他虽然生成会生成两次,但是只需要对一次就可以过第四个if,也就是说应该需要爆破,看第五个if
1 | function hc_CheckContract($stamp, $collision, $stamp_contract) |
传参的时候就不知道$contract是多少,所以应该是NULL,跟进函数hc_ExtractBits
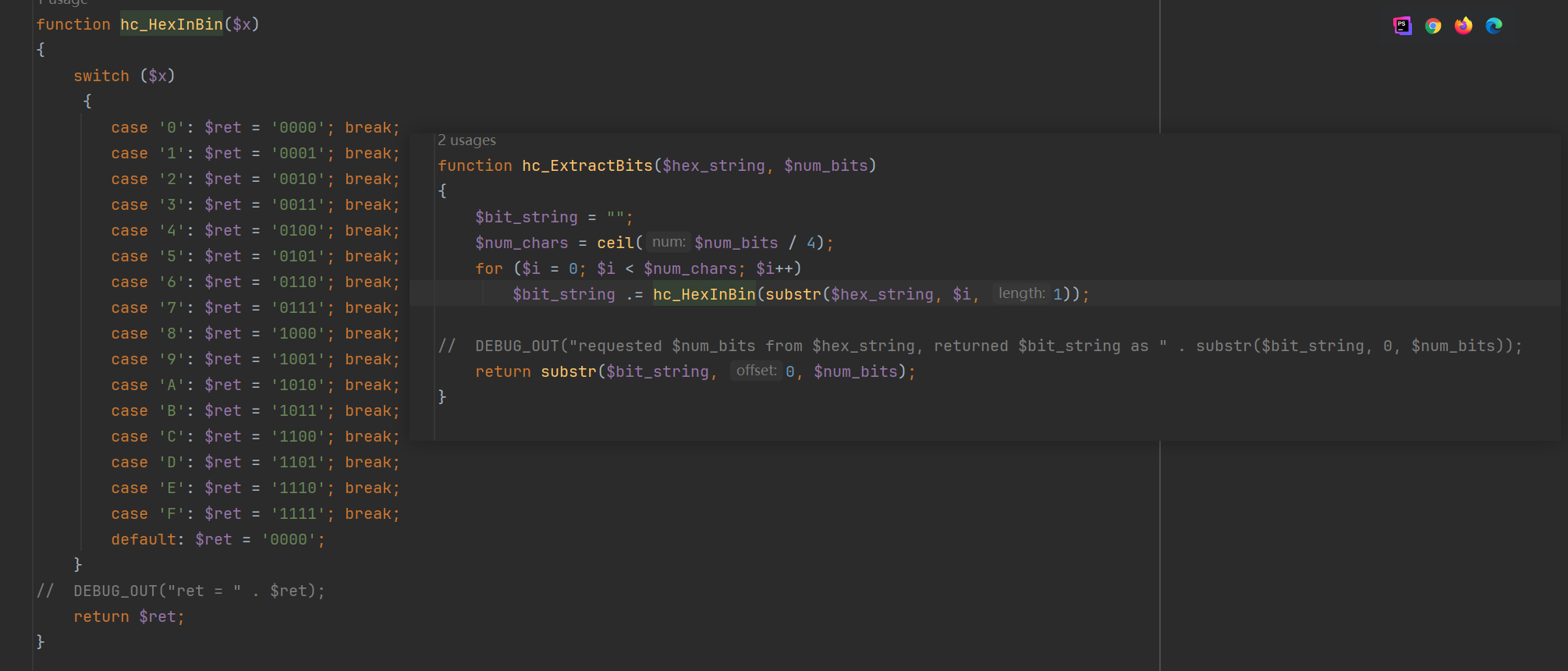
这函数就是一个十六进制转二进制的函数,但是由于$contract为NULL所以前四层过了,第五层也会过,就可以获得flag了
Fajny Jagazyn Wartości Kluczy
是一个go的web应用,代码量很小
1 | package main |
1 | package main |
我们先看kv.go,首先对路径关键字进行约束
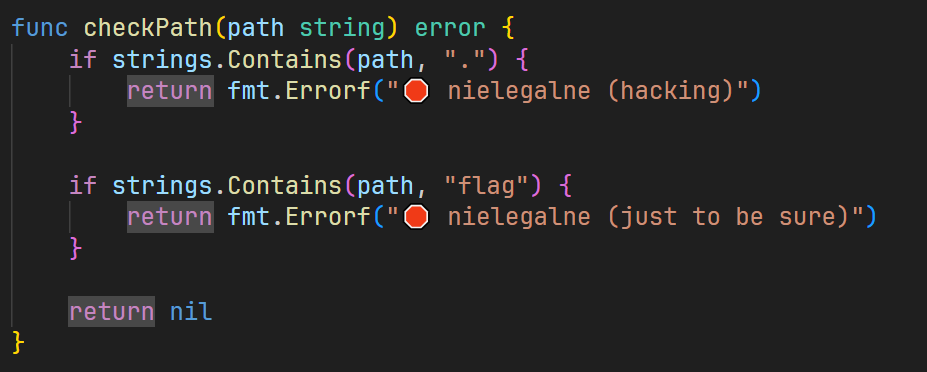
设置180s自动退出,也就是说我们的session是有时限的
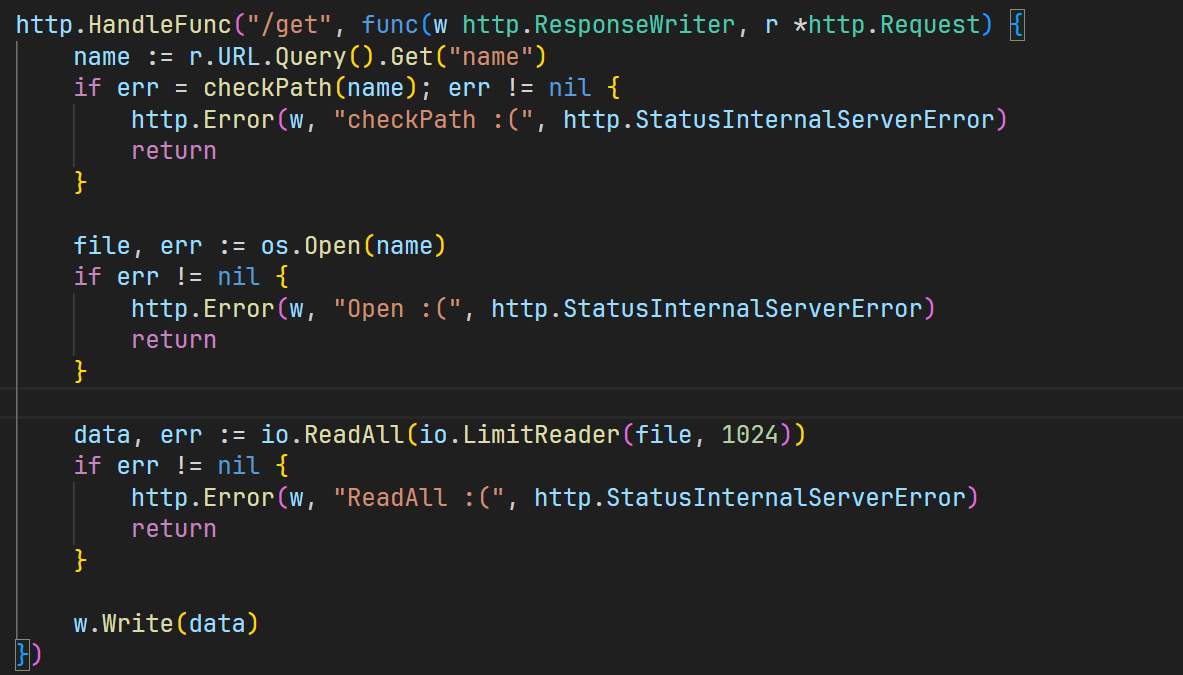
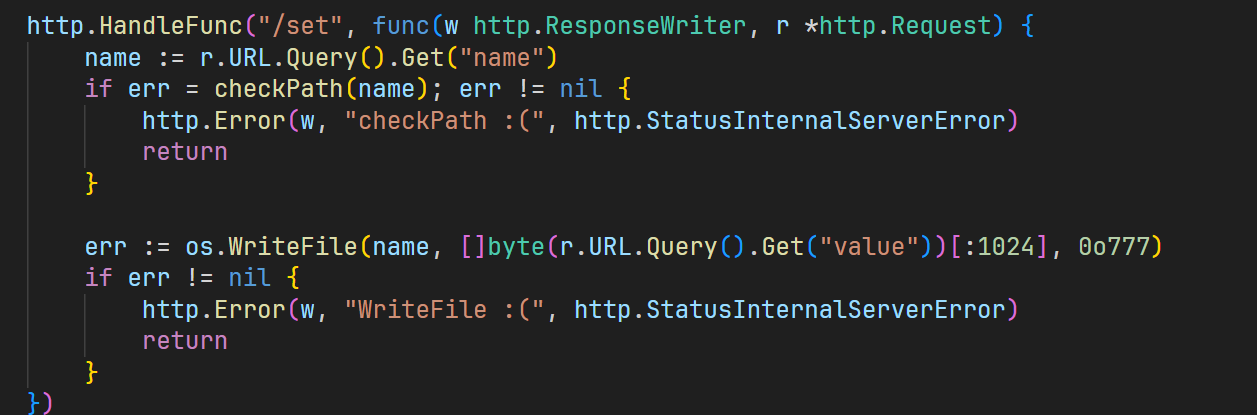
可以写入文件或者是读取文件,成功读取环境变量
1 | /get?name=/proc/self/environ |
首先想到的就是Unicode来进行绕过但是失败了
1 | /get?name=/home/ctf/flag.txt |
后面想着能否进行条件竞争呢,如果我一个文件路径是正常的,一个文件路径是flag,可能就可以做到
1 | import requests |
这是我写的,在Windows上面运行的,一直没有竞争成功,看到官方WP的脚本
1 | #!/usr/bin/env python3 |
真是有点想不明白了,重启一下容器
1 | docker stop c058cf94e5ea && docker rm c058cf94e5ea && docker rmi 36b594cdd39d |
结果还是一样的不能成功
