action
我们先链接远程桌面,把D盾准备好
然后输入账号密码连接先,进来我发现这玩意是真的卡,首先把D盾搞里面
直接把本地资源管理器打开,然后本机复制,然后CV就好了
直接扫出来了shell.php
然后查看日志拿到IP
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
| 192.168.126.1 - - [26/Feb/2024:22:37:13 +0800] "GET /admin/plugin.php HTTP/1.1" 200 16392
192.168.126.1 - - [26/Feb/2024:22:37:13 +0800] "POST /admin/plugin.php?action=check_update HTTP/1.1" 400 94
::1 - - [26/Feb/2024:22:37:27 +0800] "-" 408 -
192.168.126.1 - - [26/Feb/2024:22:39:15 +0800] "POST /admin/plugin.php?action=upload_zip HTTP/1.1" 302 -
192.168.126.1 - - [26/Feb/2024:22:39:15 +0800] "GET /admin/plugin.php?error_e=1 HTTP/1.1" 200 16479
192.168.126.1 - - [26/Feb/2024:22:39:15 +0800] "POST /admin/plugin.php?action=check_update HTTP/1.1" 400 94
192.168.126.1 - - [26/Feb/2024:22:44:36 +0800] "GET /admin/plugin.php?action=inactive&plugin=tips/tips.php&token=2dac908ae2df3b0237dee7081da123d213176d24 HTTP/1.1" 302 -
192.168.126.1 - - [26/Feb/2024:22:44:36 +0800] "GET /admin/plugin.php?inactive=1 HTTP/1.1" 200 16103
192.168.126.1 - - [26/Feb/2024:22:44:36 +0800] "POST /admin/plugin.php?action=check_update HTTP/1.1" 400 94
192.168.126.1 - - [26/Feb/2024:22:44:37 +0800] "GET /admin/plugin.php?action=active&plugin=tips/tips.php&token=2dac908ae2df3b0237dee7081da123d213176d24 HTTP/1.1" 302 -
192.168.126.1 - - [26/Feb/2024:22:44:37 +0800] "GET /admin/plugin.php?active=1 HTTP/1.1" 200 16392
192.168.126.1 - - [26/Feb/2024:22:44:37 +0800] "POST /admin/plugin.php?action=check_update HTTP/1.1" 400 94
::1 - - [26/Feb/2024:22:45:47 +0800] "GET /admin/plugin.php HTTP/1.1" 200 16392
::1 - - [26/Feb/2024:22:45:47 +0800] "POST /admin/plugin.php?action=check_update HTTP/1.1" 400 94
::1 - - [26/Feb/2024:22:45:51 +0800] "GET /admin/plugin.php HTTP/1.1" 200 16392
::1 - - [26/Feb/2024:22:45:51 +0800] "GET /admin/views/images/favicon.ico HTTP/1.1" 200 15406
::1 - - [26/Feb/2024:22:45:51 +0800] "POST /admin/plugin.php?action=check_update HTTP/1.1" 400 94
192.168.126.1 - - [26/Feb/2024:22:45:57 +0800] "GET /admin/plugin.php?action=del&plugin=tips/tips.php&token=2dac908ae2df3b0237dee7081da123d213176d24 HTTP/1.1" 302 -
192.168.126.1 - - [26/Feb/2024:22:45:57 +0800] "GET /admin/plugin.php?activate_del=1 HTTP/1.1" 200 14725
192.168.126.1 - - [26/Feb/2024:22:45:57 +0800] "POST /admin/plugin.php?action=check_update HTTP/1.1" 400 94
192.168.126.1 - - [26/Feb/2024:22:46:05 +0800] "POST /admin/plugin.php?action=upload_zip HTTP/1.1" 302 -
192.168.126.1 - - [26/Feb/2024:22:46:05 +0800] "GET /admin/plugin.php?activate_install=1 HTTP/1.1" 200 16182
192.168.126.1 - - [26/Feb/2024:22:46:05 +0800] "POST /admin/plugin.php?action=check_update HTTP/1.1" 400 94
192.168.126.1 - - [26/Feb/2024:22:46:08 +0800] "GET /admin/plugin.php?action=active&plugin=tips/tips.php&token=2dac908ae2df3b0237dee7081da123d213176d24 HTTP/1.1" 302 -
192.168.126.1 - - [26/Feb/2024:22:46:08 +0800] "GET /admin/plugin.php?active=1 HTTP/1.1" 200 16392
192.168.126.1 - - [26/Feb/2024:22:46:08 +0800] "POST /admin/plugin.php?action=check_update HTTP/1.1" 400 94
192.168.126.1 - - [26/Feb/2024:22:46:20 +0800] "GET /content/plugins/tips HTTP/1.1" 301 252
192.168.126.1 - - [26/Feb/2024:22:46:20 +0800] "GET /content/plugins/tips/ HTTP/1.1" 404 -
192.168.126.1 - - [26/Feb/2024:22:46:23 +0800] "GET /content/plugins/tips/shell.php HTTP/1.1" 200 -
192.168.126.1 - - [26/Feb/2024:22:46:35 +0800] "POST /content/plugins/tips/shell.php HTTP/1.1" 200 -
192.168.126.1 - - [26/Feb/2024:22:46:35 +0800] "POST /content/plugins/tips/shell.php HTTP/1.1" 200 -
192.168.126.1 - - [26/Feb/2024:22:46:35 +0800] "GET /content/plugins/tips/shell.php?888666=619 HTTP/1.1" 200 -
192.168.126.1 - - [26/Feb/2024:22:47:54 +0800] "POST /content/plugins/tips/shell.php HTTP/1.1" 200 -
192.168.126.1 - - [26/Feb/2024:22:47:54 +0800] "POST /content/plugins/tips/shell.php HTTP/1.1" 200 -
192.168.126.1 - - [26/Feb/2024:22:48:47 +0800] "POST /content/plugins/tips/shell.php HTTP/1.1" 200 -
192.168.126.1 - - [26/Feb/2024:22:49:58 +0800] "POST /content/plugins/tips/%73%68%65%6c%6c%2e%70%68%70?%67%58%4e%44%4c%44%68%4b%45%71%47%6c%30%54%7a%6c%31%4c%4c%42%56%32%3d%48%65%4b%76%55%37%6c%45%37%46%36%33%36%67%44%31%31%70%35%4c%5a%50 HTTP/1.1" 200 -
192.168.126.1 - - [26/Feb/2024:22:49:58 +0800] "POST /content/plugins/tips/%73%68%65%6c%6c%2e%70%68%70?%41%34%44%65%6a%7a%4f%46%6d%37%75%37%4b%6e%79%55%54%31%49%62%59%39%74%63%4a%72%34%74%4d%78%41%41%6c%58%58%36%6d%4e%41%70%54%79%3d%4e%48%66%68%69%6b%36%68%66%6e%55%58%37%68%58%64%44%37%39%75%4b%6e%47%4c%35%4c%59%66%37%6b%56%71%43%4f%75%35%31%69%48%4f%5a%38 HTTP/1.1" 200 -
192.168.126.1 - - [26/Feb/2024:22:49:58 +0800] "GET /content/plugins/tips/shell.php?nzQbavYgN6ODoxF1=G65ASv8y3UvkREqS1BhtN8ZQ9rBOTuYm&YD2ZXadPSvHEOYc2=Mtp8qcxNdDLrUSDD7WH6NZB9LGuhPYLT&888666=7Sn1K3PXNdf2Fh0LymWfQDymalxp4ty1&Y0fAQLYotO6P9ZRM=dj3DhH6k3adKnymgE07L8YUSXjdkX4vx&pV8lXaCzdJhmssdK=V4VdNXaxzvxXLdkEB9DTv7Bqbg3qw92J HTTP/1.1" 200 -
192.168.126.1 - - [26/Feb/2024:22:50:33 +0800] "POST /content/plugins/tips/%73%68%65%6c%6c%2e%70%68%70?%7a%4e%61%30%59%52%68%54%39%4d%44%4a%76%38%4c%51%54%6f%36%64%56%33%76%4c%56%6b%3d%42%4b%53%46%76%6d%6a%33%61%54%61%30%32%77%68%76%6f%4f%73%6d%36%6d%41%6f%31%72 HTTP/1.1" 200 -
192.168.126.1 - - [26/Feb/2024:22:50:33 +0800] "POST /content/plugins/tips/%73%68%65%6c%6c%2e%70%68%70?%79%53%4b%41%62%49%6d%72%50%35%51%6a%75%4b%76%79%54%51%34%68%79%34%46%34%38%32%36%4b%37%64%36%6f%42%72%65%69%4b%4b%35%73%74%63%4d%62%66%73%68%6b%71%66%51%42%38%47%65%3d%4e%72%45%5a%54%6c%6a%68%38%42%6a%62%4f%44%66%78%30%66%4b%6b%72%56%32%42%6e%42%4e%6c%56%55%4a%36%4e%36%69%4e%6f%58%44%44%72%58%67%58%30%77%54%69%49%4d%4a%64%5a%72%59 HTTP/1.1" 200 -
192.168.126.1 - - [26/Feb/2024:22:50:33 +0800] "GET /content/plugins/tips/shell.php?AMKhtlTTEMKCZN5T=VbN2ItDmt0cZsJ8nFYFjPG8JpJHhNyqg&NQxMQd88ByKdwKQF=5vlwUtyYSChArIsZ3ajO6Jxzx7vRJuHl&888666=XSXMdgEcy5mYZOn9L4RoWLbwYo9nTxgr&htdk7suOo2SdXKmV=10I1HotZgl6Y50OMPTZRfKOMV1oVbQky&pp4TqWAlQHyYQdb1=rFVrQrbQT3VMlwPZxrnKVOekDCUcVeiX HTTP/1.1" 200 -
192.168.126.1 - - [26/Feb/2024:22:51:58 +0800] "POST /content/plugins/tips/shell.php HTTP/1.1" 200 -
|
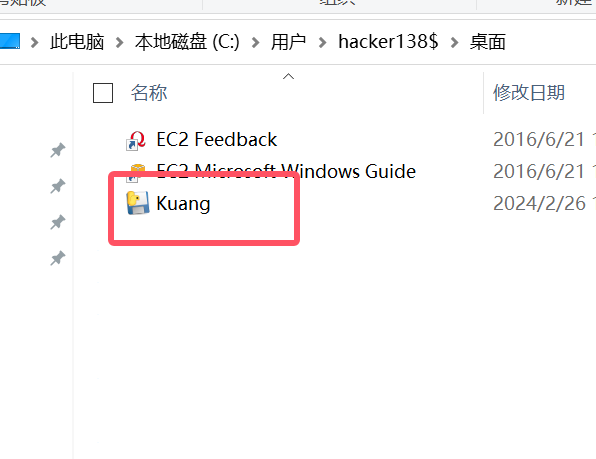
这里直接看到是pyinstaller打包,我们使用pyinstxtractor进行反编译
1
| https://github.com/extremecoders-re/pyinstxtractor
|
下载好之后搞进去
1
| python pyinstxtractor.py kuang.exe
|
emm发现一个问题,里面没有Python,那还是把kaung.exe搞到主机把
我们反编译就是要那个pyc文件所以这里直接把pyc放在010里面就好了
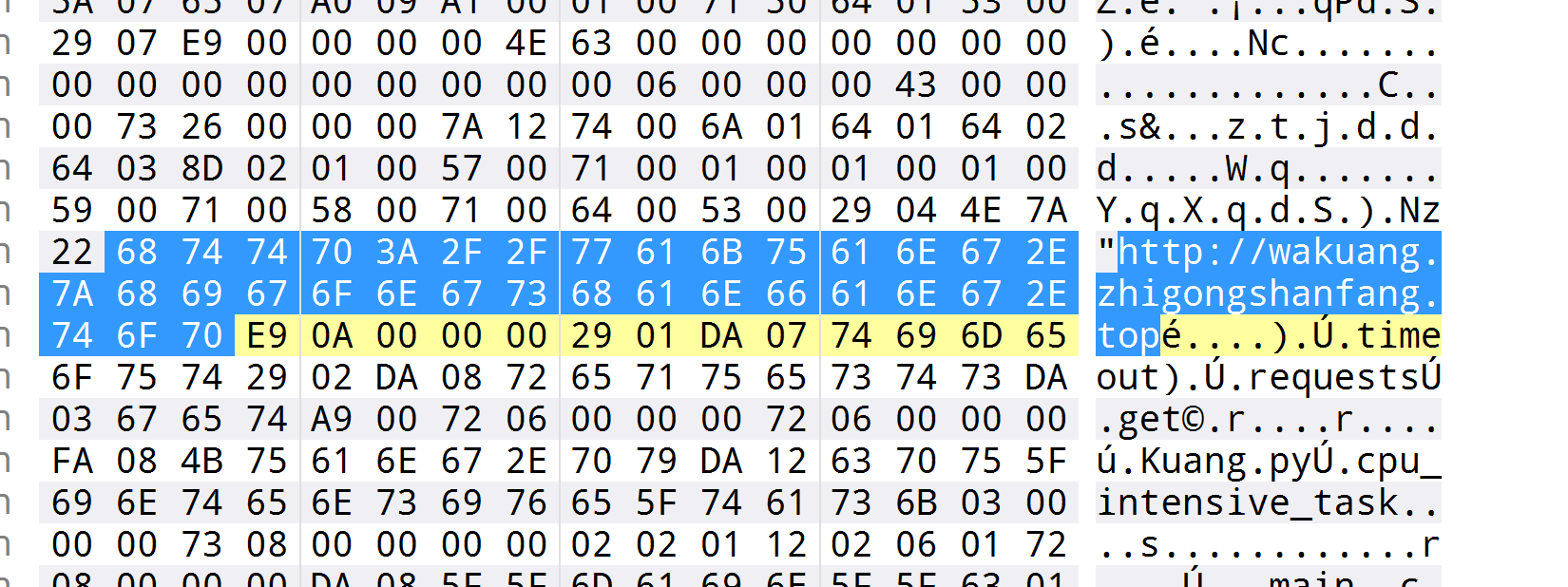
1
| flag{wakuang.zhigongshanfang.top}
|


